System and method for processing information using encryption key block
An information processing system and key group technology, applied in the field of information processing systems, can solve the problems of inconvenient update processing, increased storage capacity, large computing load, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0109] [System Outline]
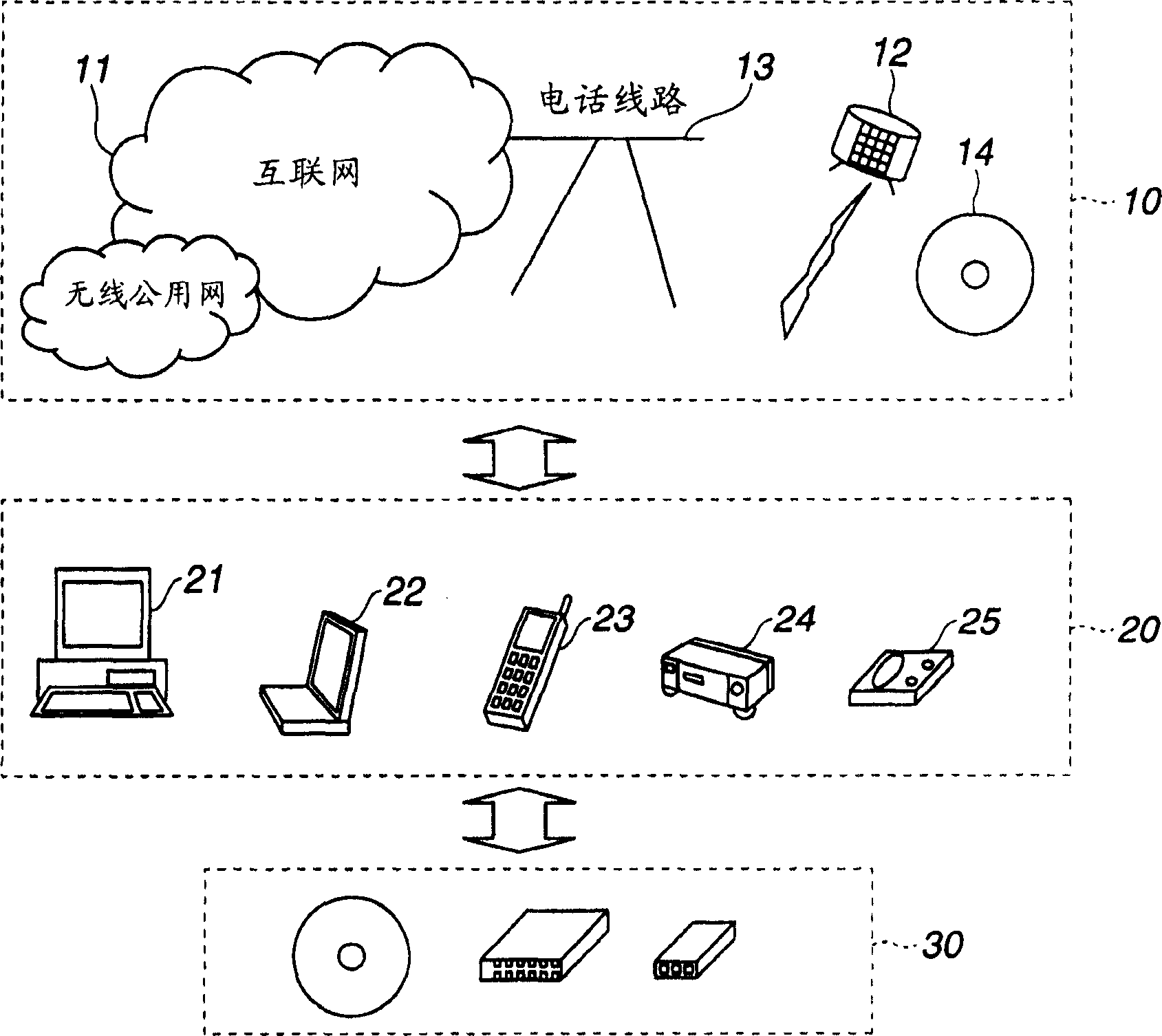
[0110] figure 1 An example of a content distribution system to which the data processing system of the present invention is applicable is shown. The content distribution side 10 encrypts the content or the content key and transmits it to a device on the content receiving side 20 capable of reproducing various contents. The device on the receiving side 20 decrypts the received encrypted content or encrypted content key to obtain the content or content key, reproduces image data and audio data, or executes various programs. Data exchange between the content distribution side 10 and the content receiving side 20 is performed via a network such as the Internet, or a traversable recording medium such as DVD or CD.
[0111] As a data distributor on the content distribution side 10, there are Internet 11, satellite broadcasting 12, telephone line 13, DVD, CD and other media 14, etc. On the other hand, as a device on the content receiving side 20, there is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com