Key generation and distribution method, key generation device and key management system
A key generation device and key generation technology, applied in the field of information security, can solve the problems of lack of advantages in information storage and key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
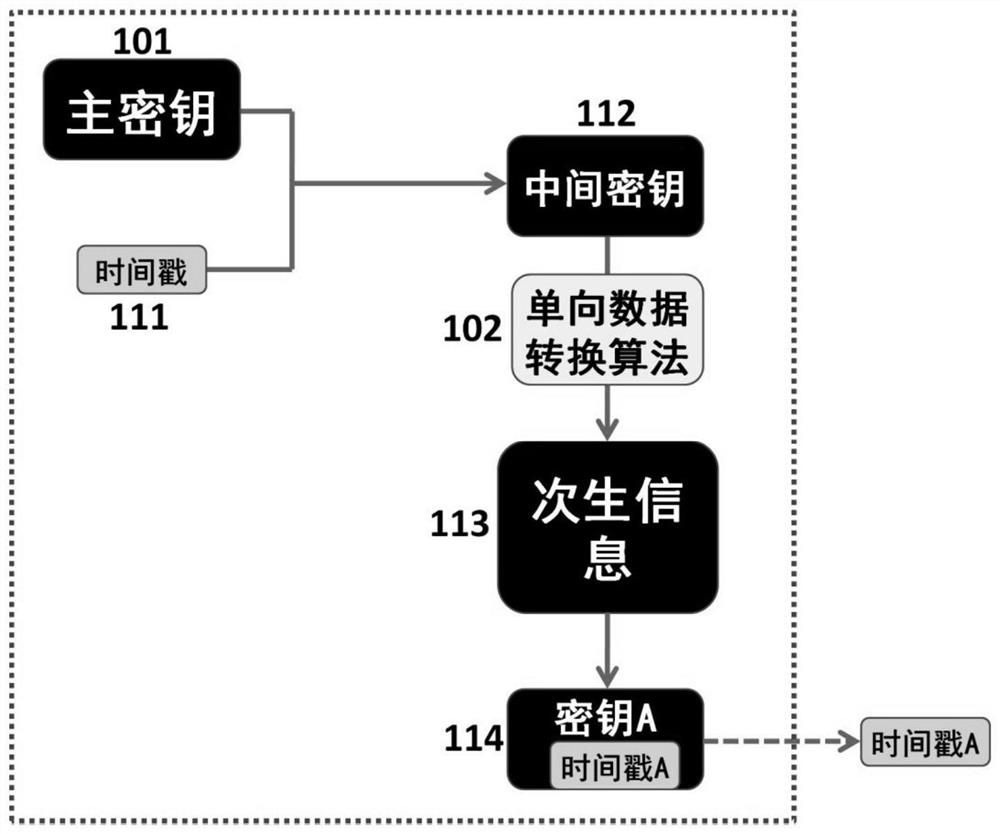
[0196] figure 1A schematic diagram showing key generation by the method of the present invention. with the help of figure 1 , this embodiment describes the use of the method of the present invention, with the help of time stamps that can be composed of arbitrary information, at least through a one-way data conversion algorithm, relying on a master key generation and secure distribution to meet the required number, key strength The implementation method of an independent key that can be equivalent to the number of bits of the master key.
[0197] The method in the embodiment of the present invention can usually be realized by a key generation module; the key generation module can be used in various systems, including but not limited to key generation devices, key management systems, encryption and decryption devices, and file management system, information security transmission system, etc., can be used as a component of the communication equipment in the system, in the form ...
no. 2 example
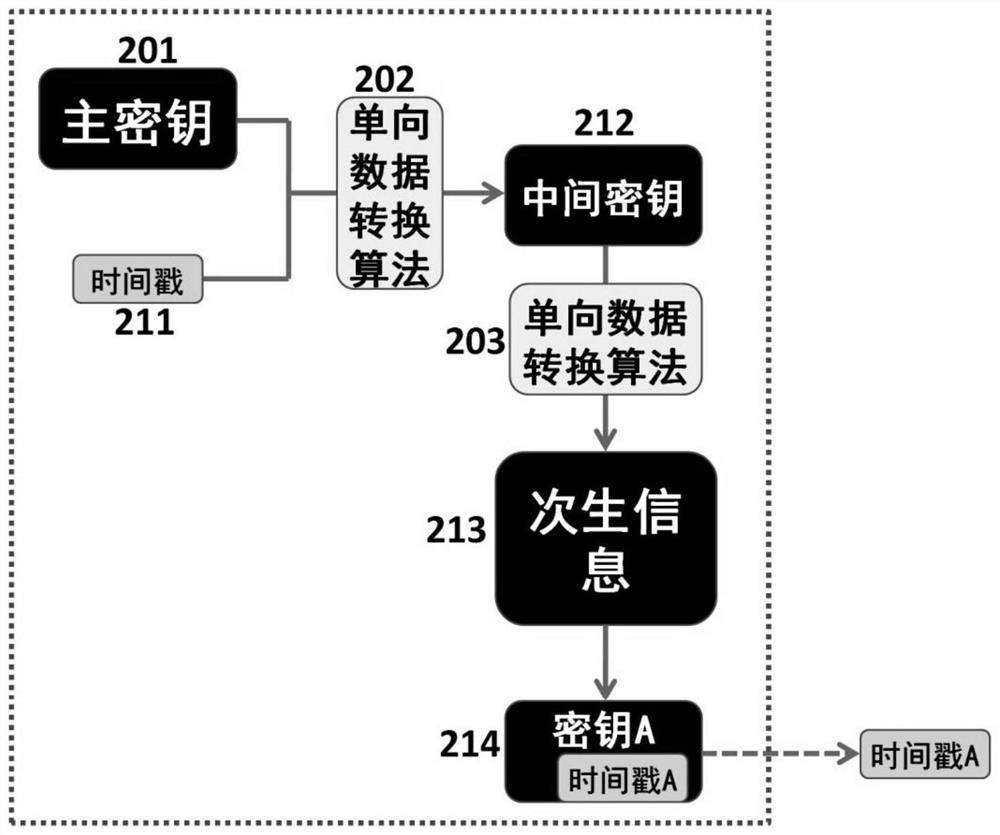
[0373] Below, will combine Figure 4 A specific example of generating a key according to the second embodiment is described. The one-way data conversion algorithm employs common data conversion under the control of input information. That is, the one-way data conversion algorithm performs data conversion using input information as control information to generate output information.
[0374] Such as Figure 4 As shown, the system information may include a master key 401, a public database 402, and one-way data conversion algorithms 403, 404 and 405;
[0375] In the method of the second embodiment, the system information further includes public data stored in the public database of the key generating device, and the number of bits contained in the public data is much larger than the number of bits contained in the master key.
[0376] In this example, a one-way data transformation algorithm performs data transformation on the common data to generate output information using i...
no. 3 example
[0431] Below, will refer to Figure 5 A key generation device according to an embodiment of the present invention is described.
[0432] Such as Figure 5 The key generation device 500 shown in this embodiment of the present invention may include:
[0433] System information module 510, configured to store or / and generate system information of the key generating device, may include a master key, at least one one-way data conversion algorithm, and may add a public database as required; the one-way data The conversion algorithm generates output information determined from input information from which it is not feasible to speculate or / and deduce the input information.
[0434] The key generation module 520 is configured to generate a time stamp that can be encoded by any information that is not repeated, and generate a key corresponding to the time stamp according to the system information;
[0435] The transmission module 530 is configured to receive and send the time stamp....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com