Key generation device, encryption device, and key generation and distribution system
A key generation device and key generation technology, applied in the field of information security, can solve the problems of limited information volume and limited use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
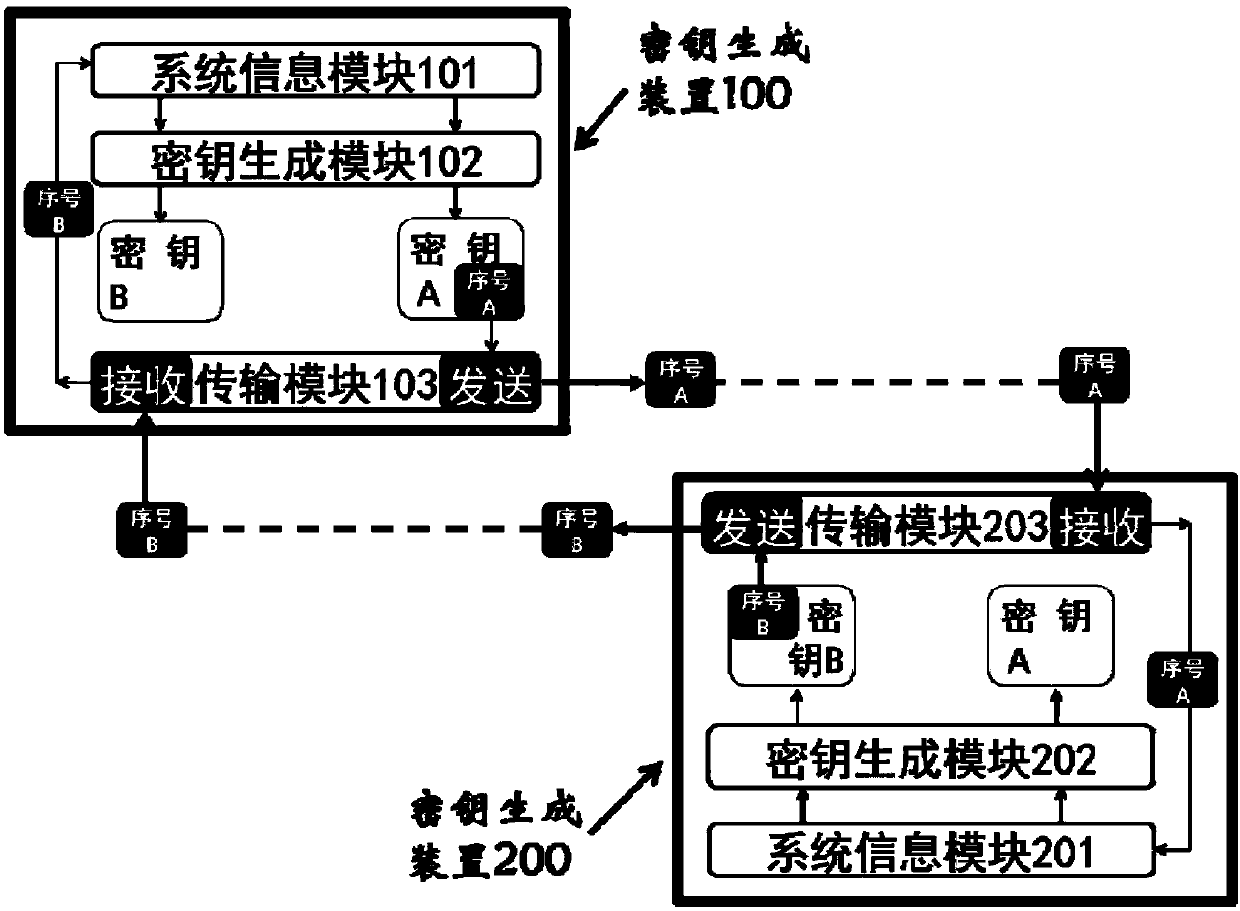
[0104] first, figure 1 is a schematic diagram showing a key generation device and a key distribution system according to an embodiment of the present invention. Such as figure 1 As shown, the key distribution system 1 according to the embodiment of the present invention includes a paired key generation device 100 and a key generation device 200 .
[0105] The key generation device 100 may include:
[0106] A system information module 101 configured to store system information of the key generation device;
[0107] The key generation module 102 is configured to controllably and orderly generate unpredictable information as a key according to the system information, and use the generation sequence number of the unpredictable information as the corresponding key sequence number; and
[0108] The transmission module 103 is configured to send the key sequence number to a paired key generation device, wherein the paired key generation device stores second system information corre...
no. 2 example
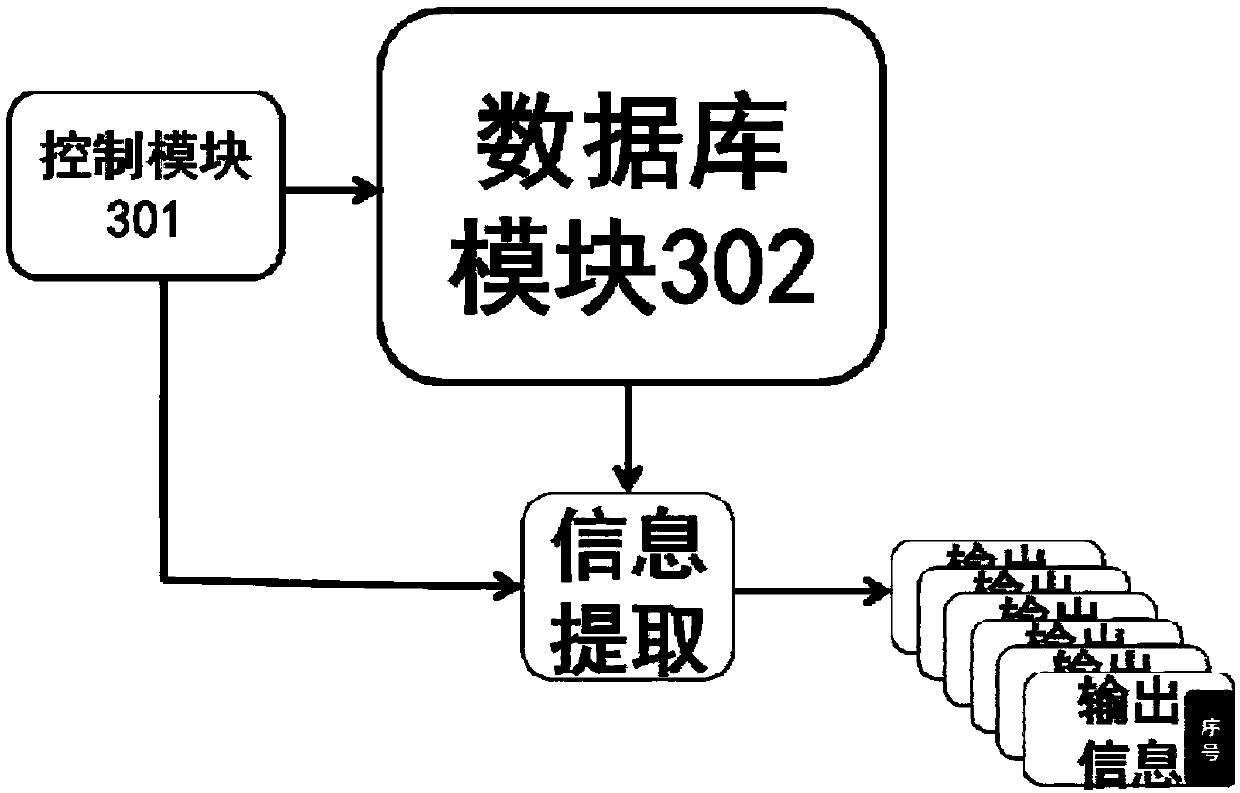
[0130] Below, will refer to image 3 The unpredictable information controllable order generation module in the key generation device according to the embodiment of the present invention is described.
[0131] The system information module 101 in the key generation device 100 described in the first embodiment above includes image 3 The unpredictable information shown can control the ordered generation module 300 .
[0132] Such as image 3 As shown, the controllable order generating module 300 includes:
[0133] A control module 301 configured to control the generation of unpredictable information;
[0134] a database module 302 configured to store unpredictable information,
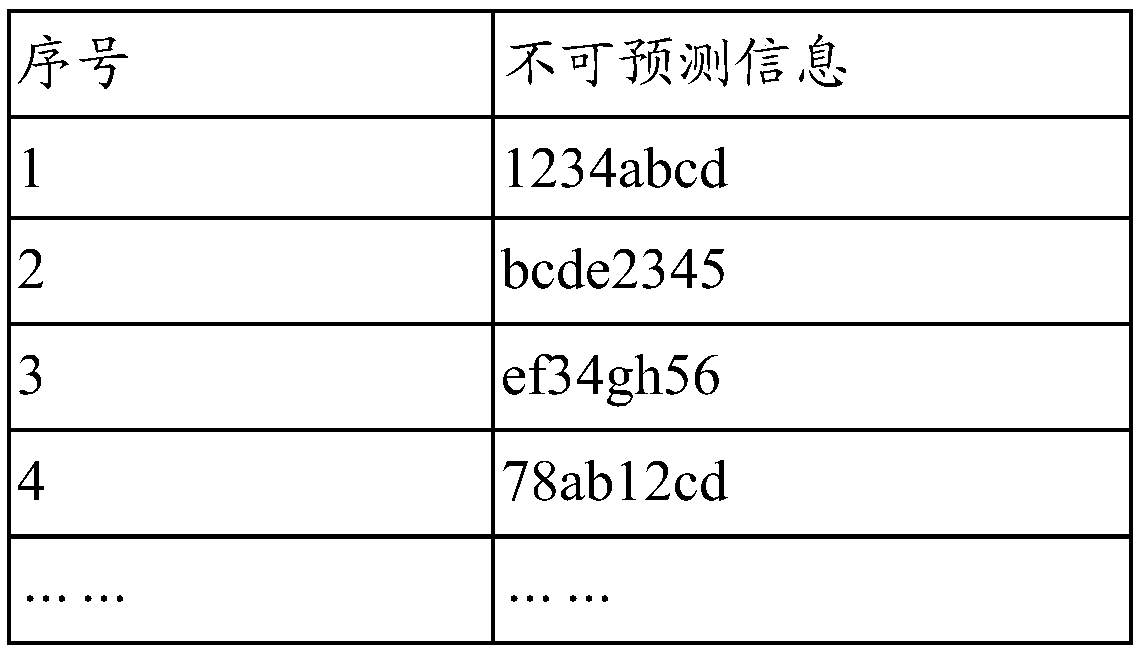
[0135]According to the control of the control module 301 in the first embodiment, the key generation module 102 extracts unpredictable information from the database module 302 in a controllable and orderly manner as a key, and uses the generated serial number as the corresponding key serial number. ...
no. 3 example
[0138] Below, will refer to Figure 4 The unpredictable information controllable order generation module in the key generation device according to the embodiment of the present invention is described.
[0139] The system information module 101 in the key generation device 100 described in the first embodiment above includes Figure 4 Unpredictable information is shown as controllable ordered generation module 400 .
[0140] Such as Figure 4 As shown, the controllable order generating module 400 includes:
[0141] A control module 401 configured to control the generation of unpredictable information;
[0142] A dynamic information module 402 configured to provide input information to be processed;
[0143] The information processing module 403 is configured to convert the input information provided by the dynamic information module into generated information through a predetermined algorithm according to the control of the control module, and extract part of the informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com