Method, system and base station for locking illegal copied mobile terminal
A mobile terminal and illegal copying technology, which is applied in the field of locking illegally copied mobile terminals, can solve problems such as wrong locking and loss of mobile terminals, and achieve the effect of avoiding wrong locking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
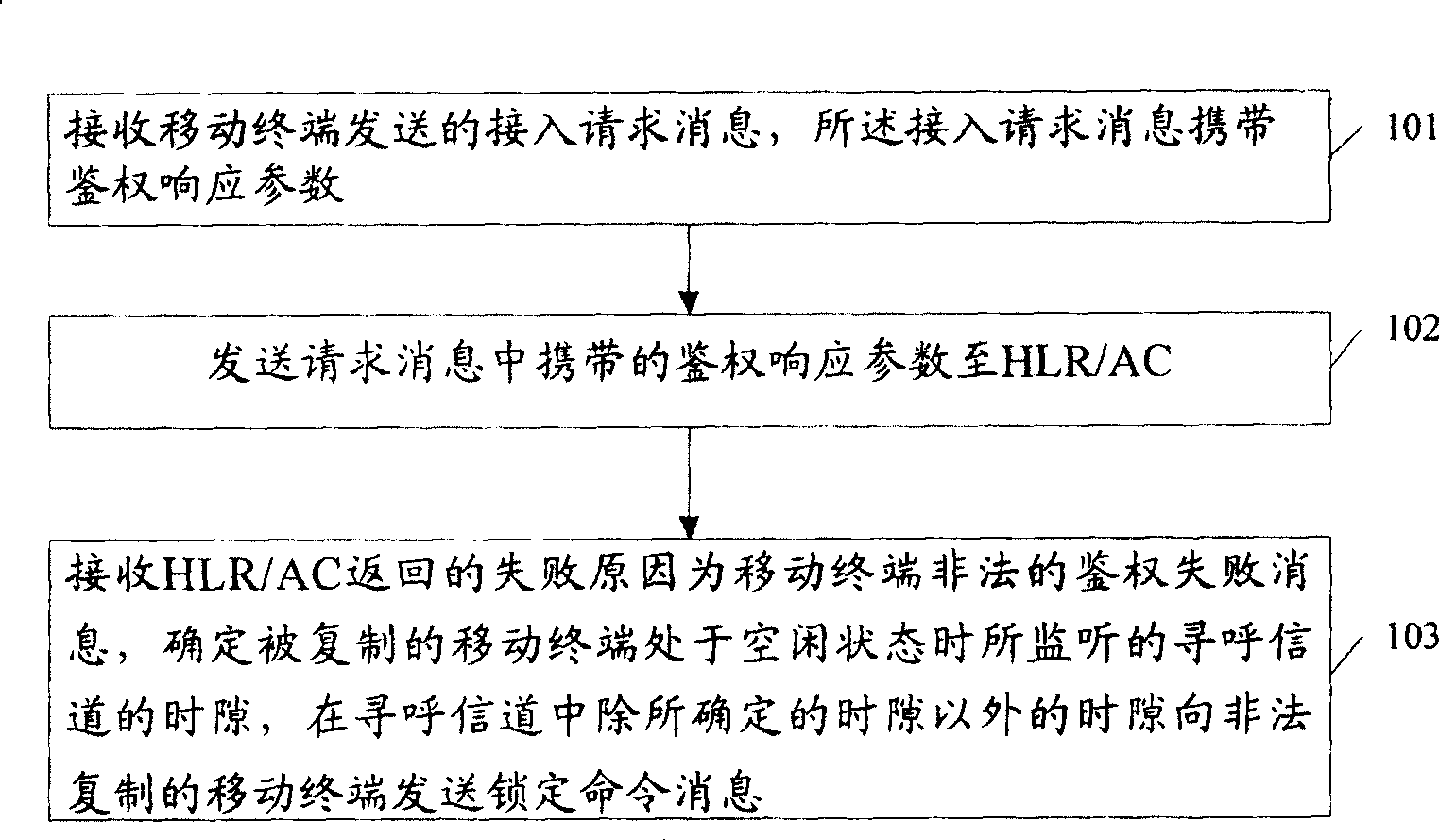
[0028] The embodiment of the present invention proposes a method for locking an illegally copied mobile terminal, see figure 1 , figure 1 It is a flowchart of a method for locking an illegally copied mobile terminal according to an embodiment of the present invention. The method includes:
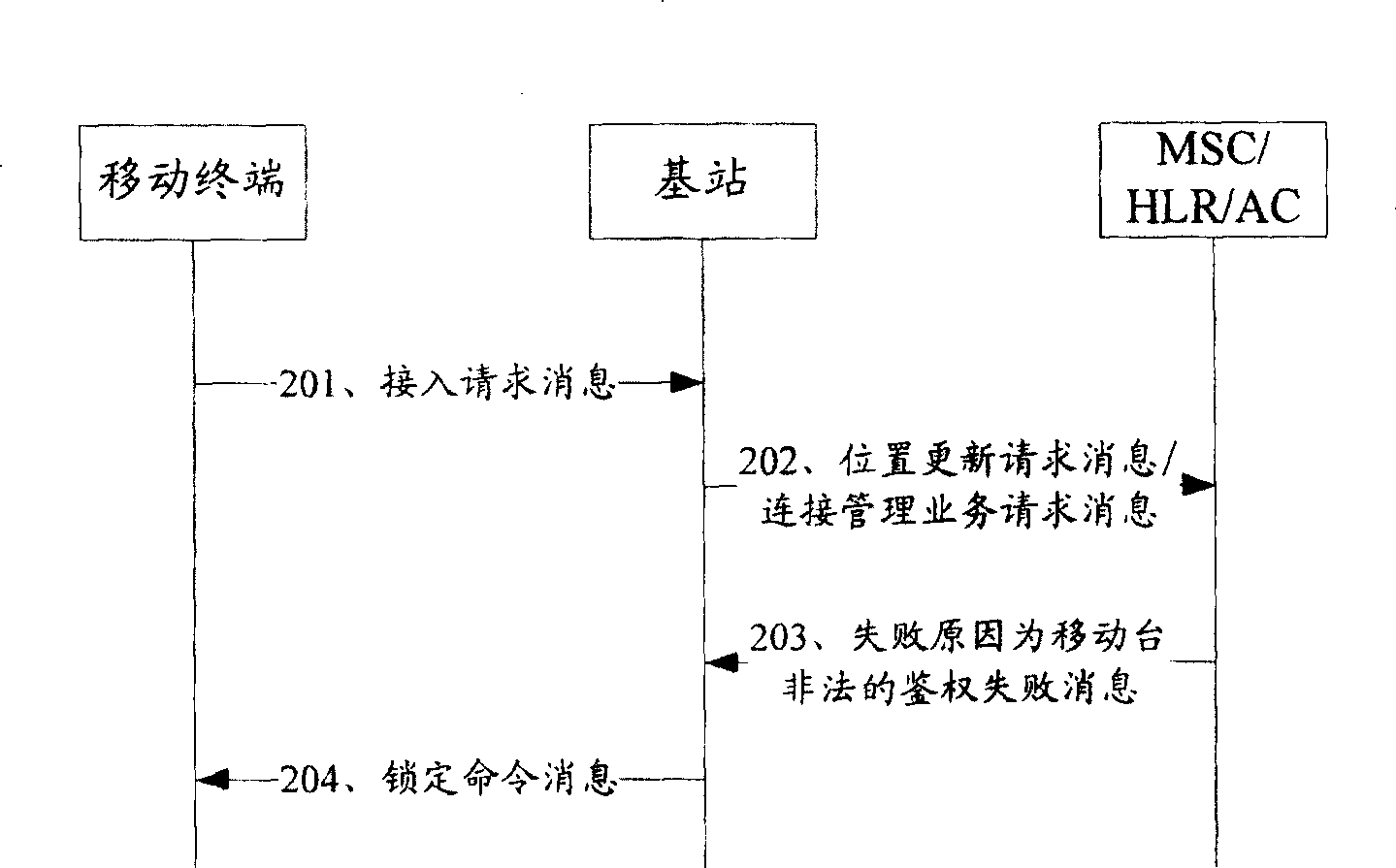
[0029] Step 101: Receive an access request message sent by a mobile terminal, where the access request message carries an authentication response parameter;
[0030] Step 102: sending the authentication response parameter carried in the access request message to the HLR / AC;
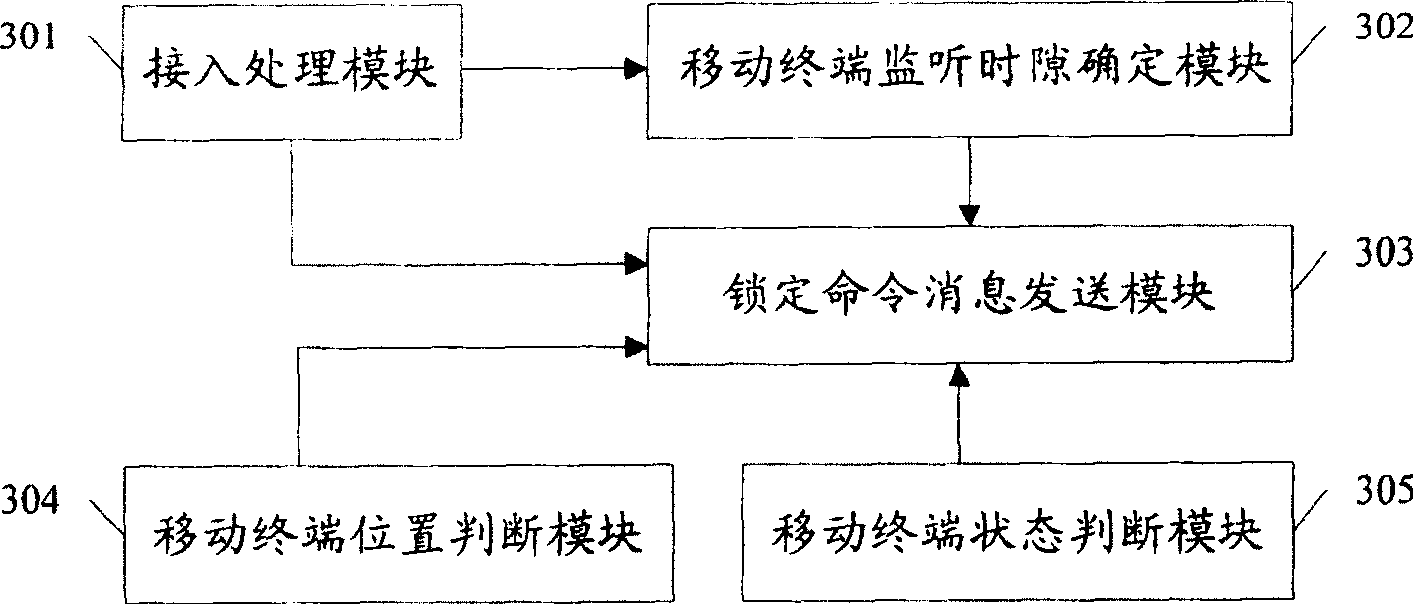
[0031] Step 103: Receive the failure reason that HLR / AC returns is the illegal authentication failure message of mobile terminal, determine the time slot of the paging channel that is monitored when the copied mobile terminal is in an idle state, and remove the determined time slot in the paging channel The time slot other than the time slot sends a lock command message to the illegally copied mobile terminal.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com