Encryption method of block cipher
An encryption method and block cipher technology, applied in the field of information security encryption, can solve the problems of insufficient application security, slow algorithm speed, and failure to find a balance, etc., and achieve easy and fast implementation, high security, and safe and reasonable design Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Describe the present invention in detail below in conjunction with accompanying drawing.
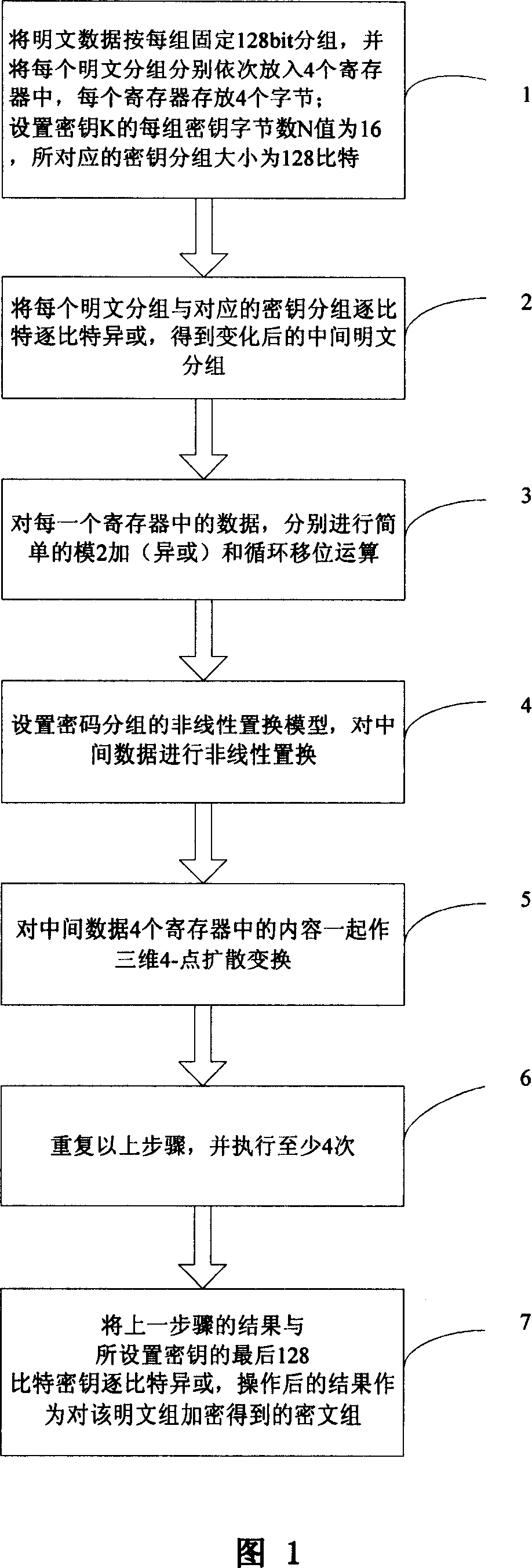
[0028] With reference to accompanying drawing 1, in one embodiment of the present invention, the technical scheme that realizes the object of the invention comprises the following steps:
[0029] Step 1: Group the plaintext data into groups of fixed 128 bits, and put each plaintext group into 4 registers in turn, and each register stores 4 bytes. Set the number of key bytes N of each group of key K to 16, and the corresponding key group size is 128 bits.
[0030] Step 2: XOR each plaintext group with the corresponding key group bit by bit to obtain the changed intermediate plaintext group.
[0031] Step 3: Perform simple modulo 2 addition (exclusive OR) and circular shift operations on the data in each register.
[0032] Step 4: Set the nonlinear permutation model of the cipher block, and perform nonlinear permutation on the intermediate data.
[0033] Step 5: Perform a three-d...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap