Highly secure ellipse curve encryption and decryption method and device
An elliptic curve encryption and elliptic curve technology, applied in the field of data encryption and decryption, can solve the problem of not reaching the security of IND_CCA2
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
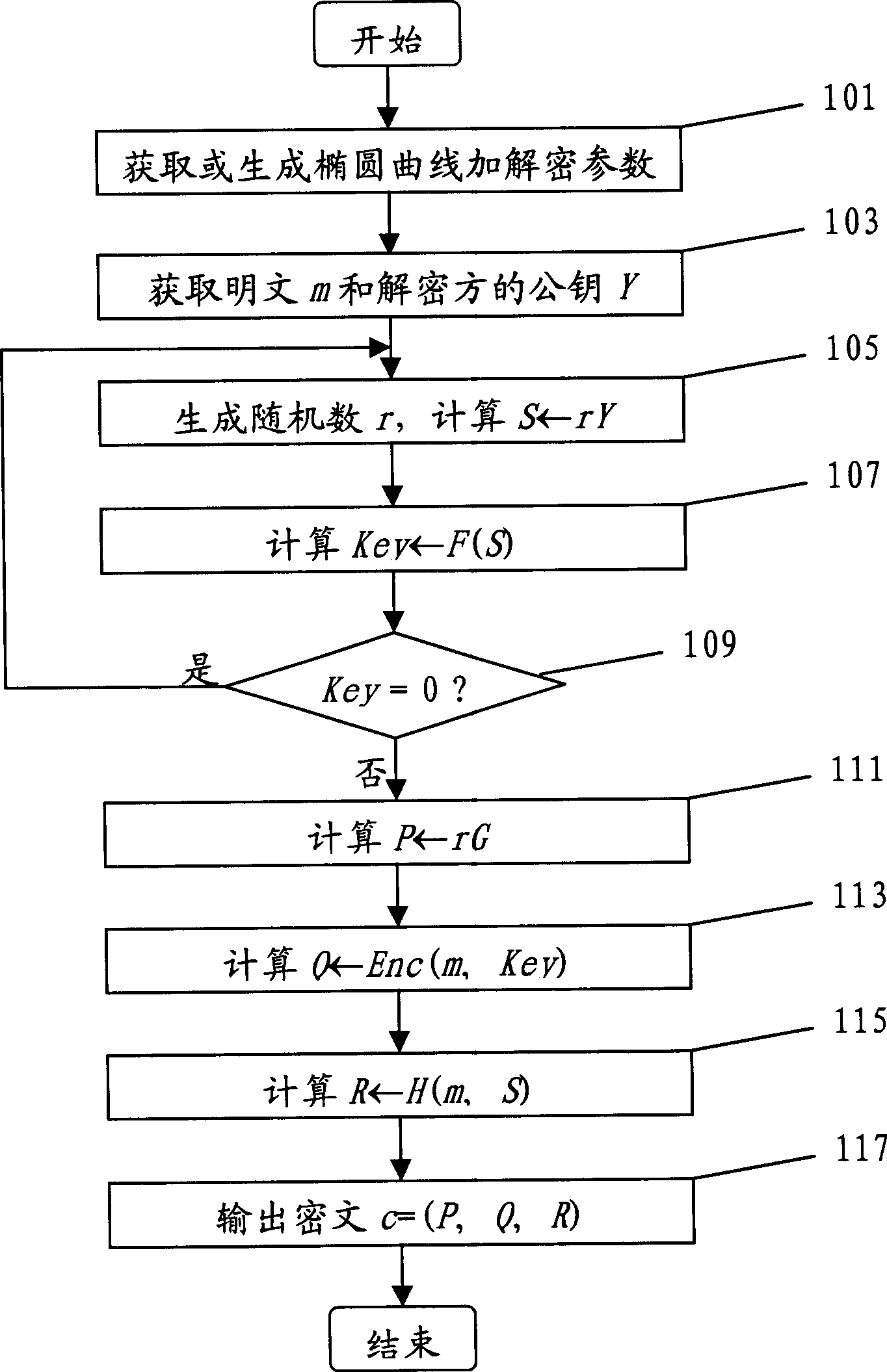
[0100] figure 1 A flowchart showing the encryption method of the present invention.
[0101] In step 101, elliptic curve encryption and decryption parameters E, G, n, H(), F(), Enc(,), Dec(,) are acquired or generated. The selection of parameters for elliptic curve encryption and decryption can be performed by both encryption and decryption parties or a third party trusted by both parties. in:
[0102] 1.1. Select the elliptic curve E on the finite field and a point G on it, so that the point group generated by G The elliptic curve discrete logarithm problem on is computationally unsolvable, let The order of is n, and E, G and n are disclosed;
[0103] 1.2. Select a safe message authentication code (MAC) generation function H(), select a key derivation function F(), select encryption function Enc(,) and decryption function Dec(,), so that for any plaintext m and encryption The key Key satisfies: m=Dec(Enc(m, Key), Key);
[0104] 1.3. Description of the selecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com