Micro-processor kernel used for cryptography arithmetic
A microprocessor core and cryptography technology, applied in the field of information security, can solve problems such as high security, low computing speed, and difficulty in sharing the same or similar functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
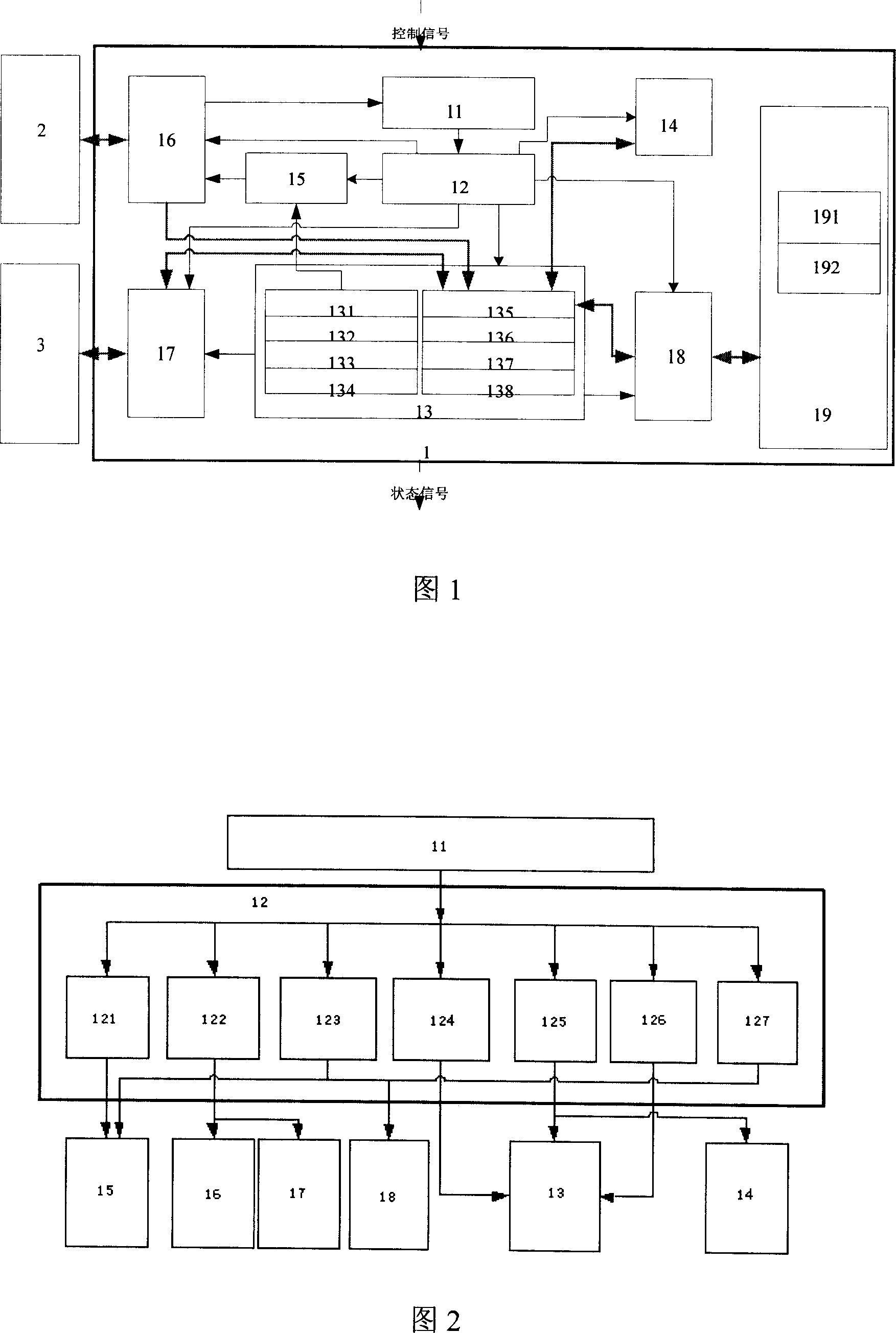
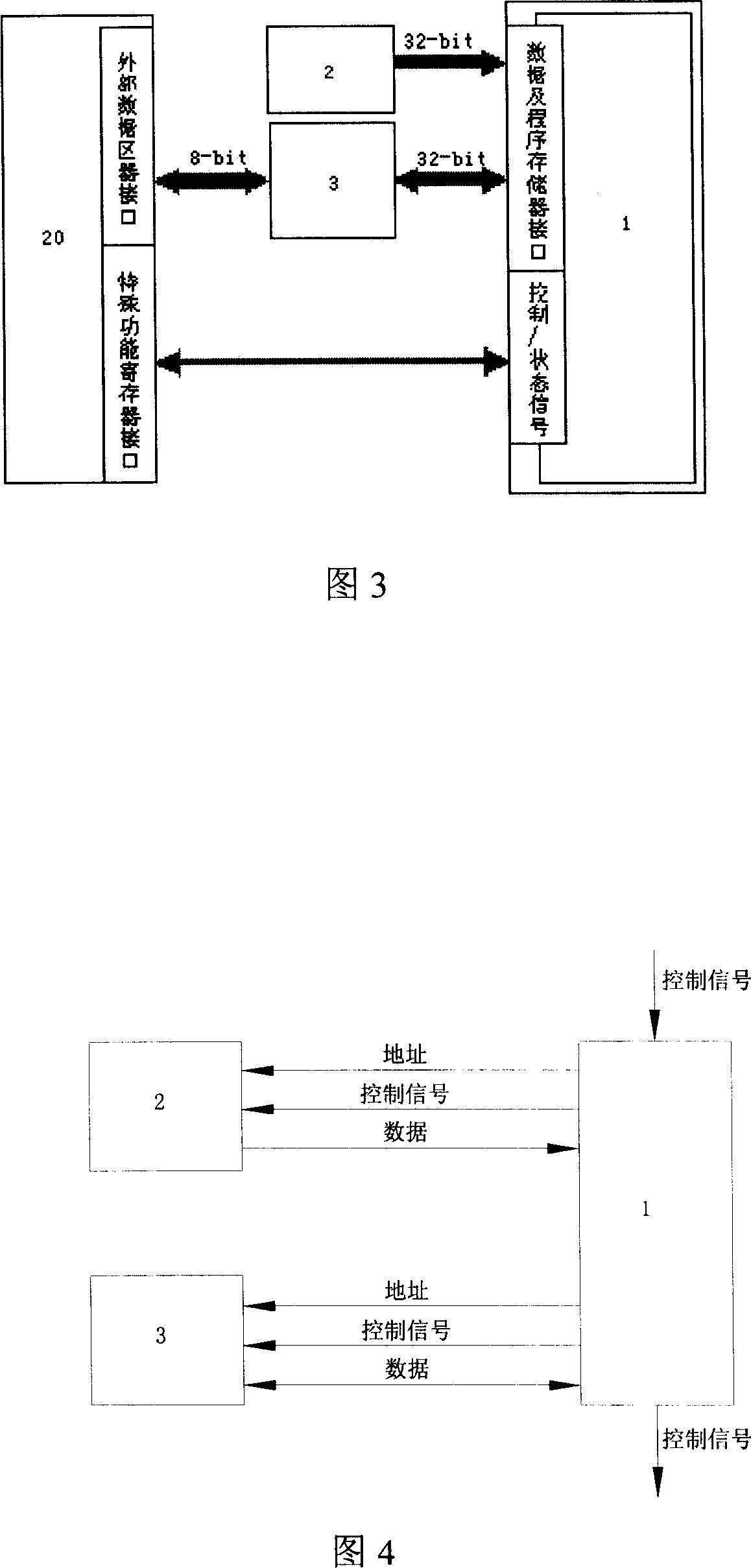
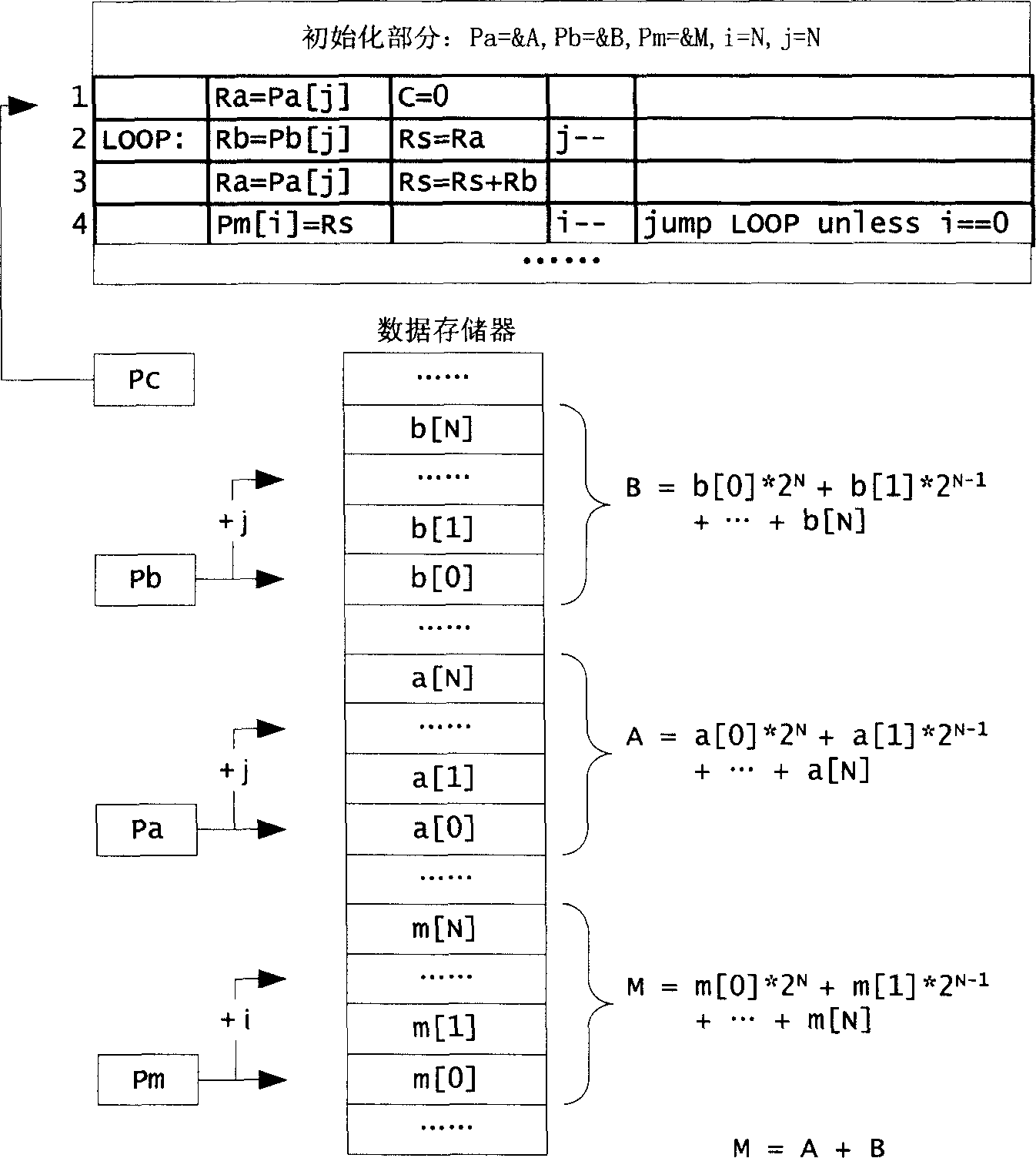
[0034] 1 and 2, the present invention includes an instruction register 11, an instruction decoding unit 12, a register file 13, a data operation unit 14, a program address generation unit 15, a program memory interface 16, a data memory interface 17, and a cryptographic acceleration module interface 18. A cryptography acceleration module 19 including a DES cryptography acceleration module 191 and an AES cryptography acceleration module 192 . The register file 13 includes a program counter 131 , a stack pointer 132 , a data pointer 133 , an acceleration module pointer 134 , a data register 135 , an index register 136 , a compare register 137 and a bit register 138 . The instruction decoding unit 12 includes a program control sub-instruction decoding unit 121, a memory access sub-instruction decoding unit 122, an acceleration module access sub-instruction decoding unit 123, a register copy sub-instruction decoding unit 124, an arithmetic logic sub-instruction decoding unit Code ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com