Entity secret talk establishing system based on multiple key distribution centers and method therefor
A key distribution center and key distribution technology, applied in key distribution, can solve the problems of lack of key perfect forward secrecy, threatening system security, etc.
Active Publication Date: 2010-11-10
CHINA IWNCOMM
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
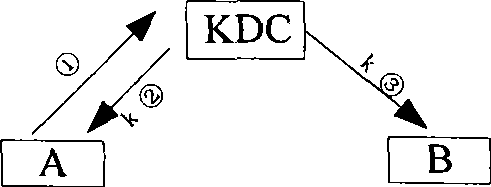
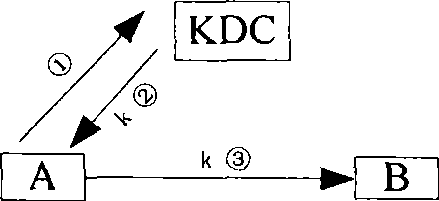
Due to the participation of the key distribution center or key transfer center, each pair of entities can use a fresh communication key each time they communicate, but each user needs to save a shared key with the key distribution center or key transfer center. The secret management key is used for a long time, and for the key distribution center and the key transfer center, it not only needs to store a huge number of secret management keys, but also bears a large security risk, because once there is a problem, it will directly Threat to the security of the entire system, and none of the above key distribution methods has the perfect forward secrecy PFS (Perfect ForwardSecrecy) of the key
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
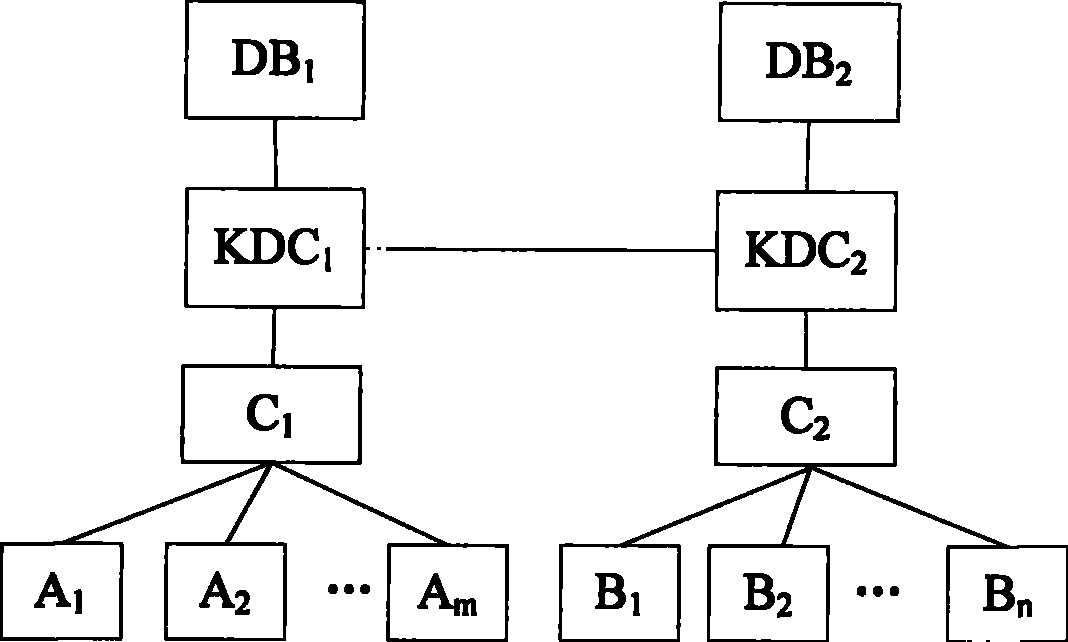
The invention relates to a system for establishing private communication of entities based on a plurality of key distribution centers and the method thereof. The system comprises a first network and a second network, wherein the first network includes first communication entities A1, A2, ellipsis, Am, a first load-bearing apparatus C1 and a first key distribution center KDC1; the second network includes second communication entities B1, B2, ellipsis, Bn, a second load-bearing apparatus KDC2, and a second key distribution center KDC1; the first key distribution center KDC1 is connected with the second key distribution center KDC2; the first key distribution center KDC1 is connected with the first communication entities A1, A2, ellipsis Am through the first load-bearing apparatus C1; and the second key distribution center KDC2 is connected with the second communication entities B1, B2, ellipsis, Bn through the second load-bearing apparatus. The system and the method thereof can achieve private communication between entities in different networks, and can distribute communication keys to each entity. Due to the PFS attribute of the keys, the complexity in managing the system keys is reduced.
Description
Entity secret call establishment system and method based on multiple key distribution centers Technical field The invention relates to a system and a method for establishing an entity secret call based on multiple key distribution centers. Background technique When confidential communication is required between communication network entities, key management is one of the key technologies. Small networks can use the method of sharing a key for each pair of users, but it is not feasible in large networks. For a system with N users, in order to realize secure communication between any two users, it is necessary to generate and distribute N(N-1) / 2 keys to ensure secure communication between any two users in the network. As the scale of the system increases, the complexity increases sharply. For a network with N of 1,000, about 500,000 keys are needed for distribution and storage. In order to reduce the complexity, a centralized key management method is usually adopted. A reliabl...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/08H04W84/04
Inventor 铁满霞曹军赖晓龙黄振海
Owner CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com