Program operation characteristic extracting method for detecting vulnerability model
A technology of program feature and model detection, applied in instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problem of repeated work affecting the detection speed, etc., to achieve the effect of speeding up the detection speed and overcoming the repeated work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
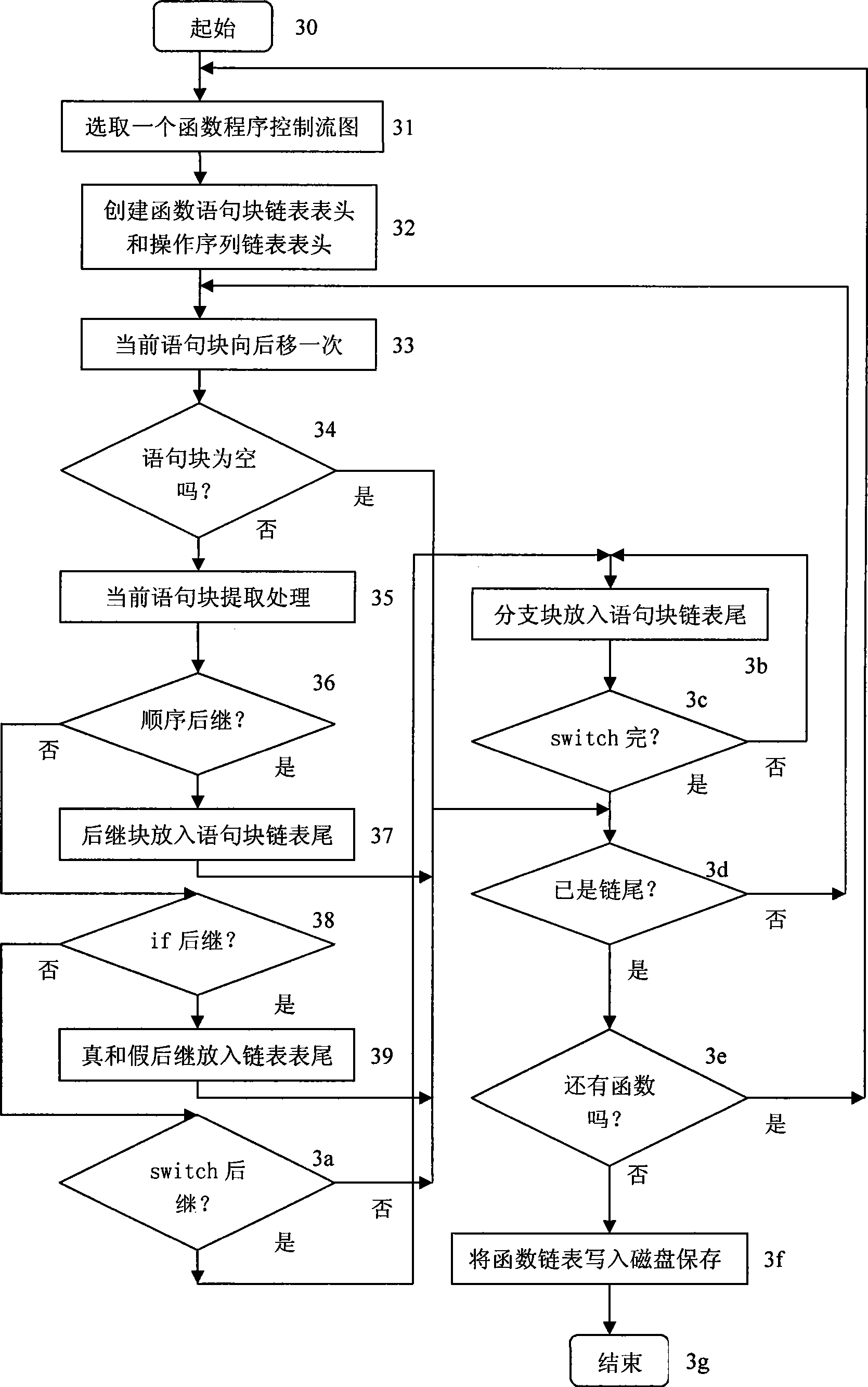
[0014] The working process of the inventive method is as Figure 1-Figure 4 shown.
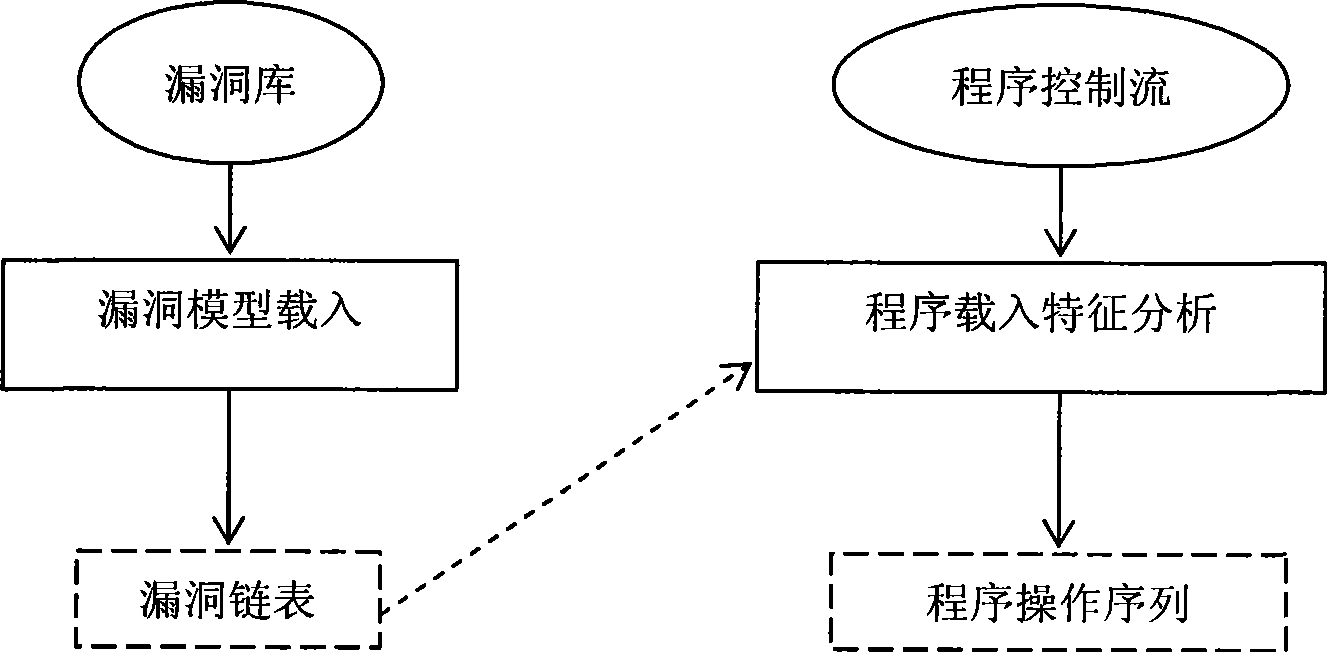
[0015] figure 1 Shown is the overall structure and working principle of this method implementation. The purpose of this method is to analyze and filter the programs to be detected according to the operations involved in the vulnerability model. Therefore, it is necessary to load the vulnerability model from the database into the memory so that it can be used as a reference when analyzing the program; the program is loaded into the feature analysis process, and the required operations are extracted according to the information related to the operation of the vulnerability model to complete the abstraction of the program and obtain the program feature sequence.
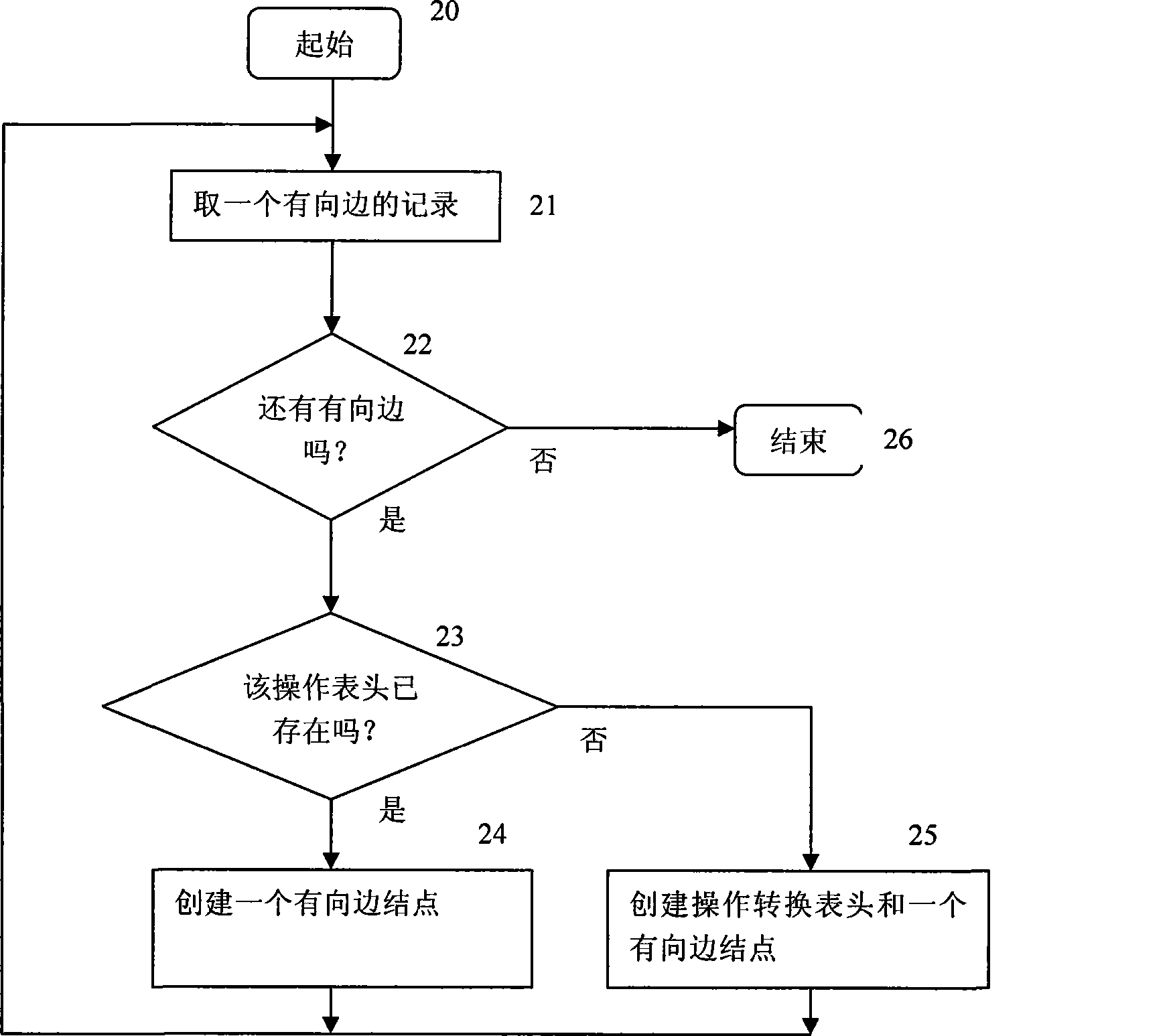
[0016] figure 2 Indicates the vulnerability model loading process. The vulnerability model is composed of state nodes and directed edges of the vulnerability state machine. There are three types of state nodes: start, intermediat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com