An administration portal
A technology for managing portals and administrators, applied in the field of management portals of network security systems, and can solve problems such as inefficiency and disadvantage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
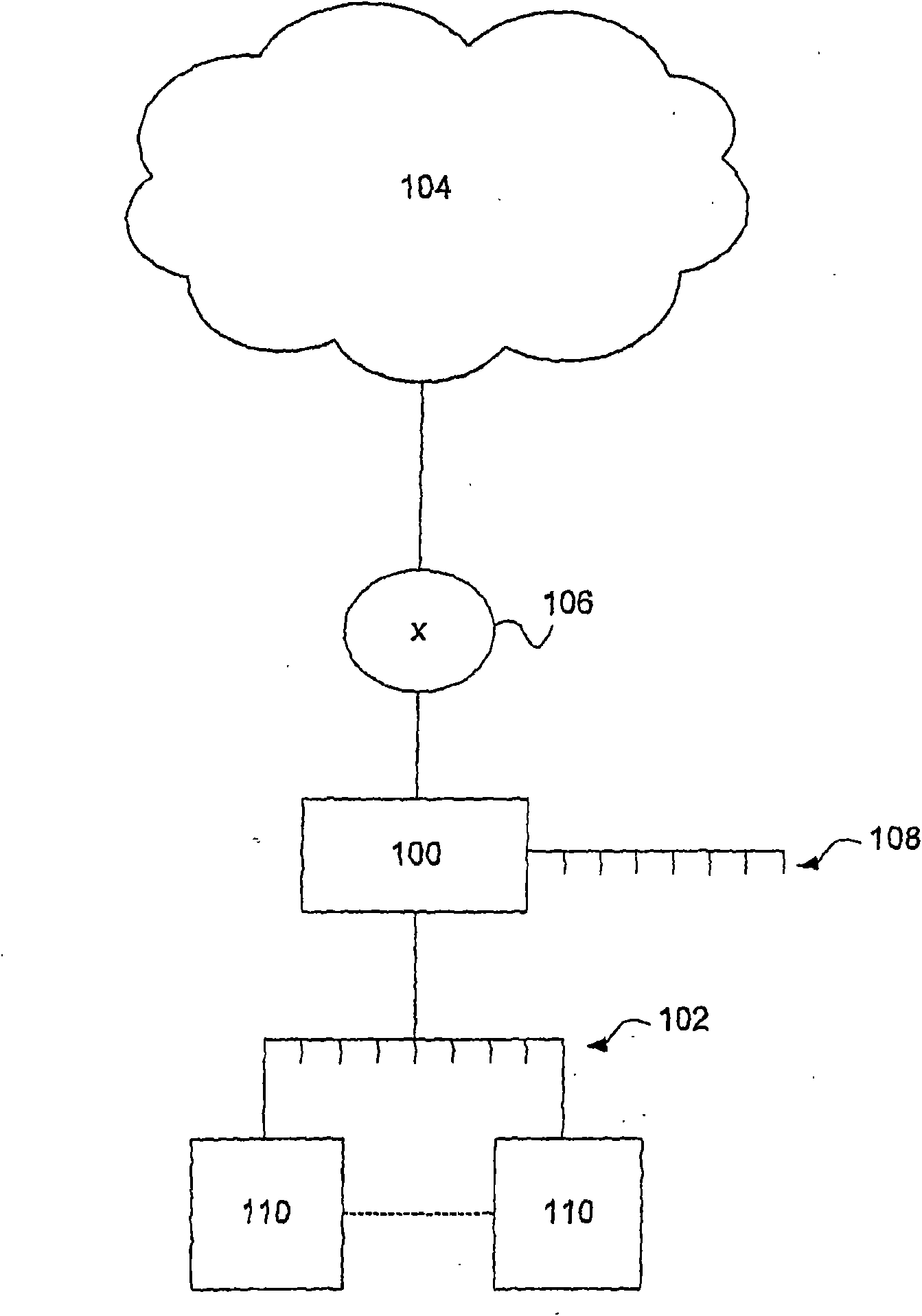
[0022] Such as figure 1 As shown, security server 100 provides Internet threat protection facilities to protect an enterprise's local area network (LAN) 102 from many types of Internet threats. These threats include viruses, worms, Trojan horses, phishing, spyware, spam, unwanted content, and hacking, as well as any other form of unwanted code, traffic, or activity related to LAN 102 . A security server or box 100 is directly connected to an external communication network 104 , such as the Internet, via a router 106 , thereby being located between a LAN 102 and the Internet 104 . LAN 102 connects a plurality of terminals 110 on network 102 . Terminals 110 are computer devices, such as personal computers or telephones, that are capable of handling network traffic and messages, such as email and HTTP requests and responses. A security server or box 100 may also provide support for a demilitarized zone (DMZ) 108, which in an alternative embodiment, server 100 may comprise sever...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com