Signature method, device and system thereof
A technology of digital signature and intelligent key device, which is applied in the field of information security and can solve the problems of data has been tampered with and intercepted, digital signature fraudulently used, and the security of data and information cannot be guaranteed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
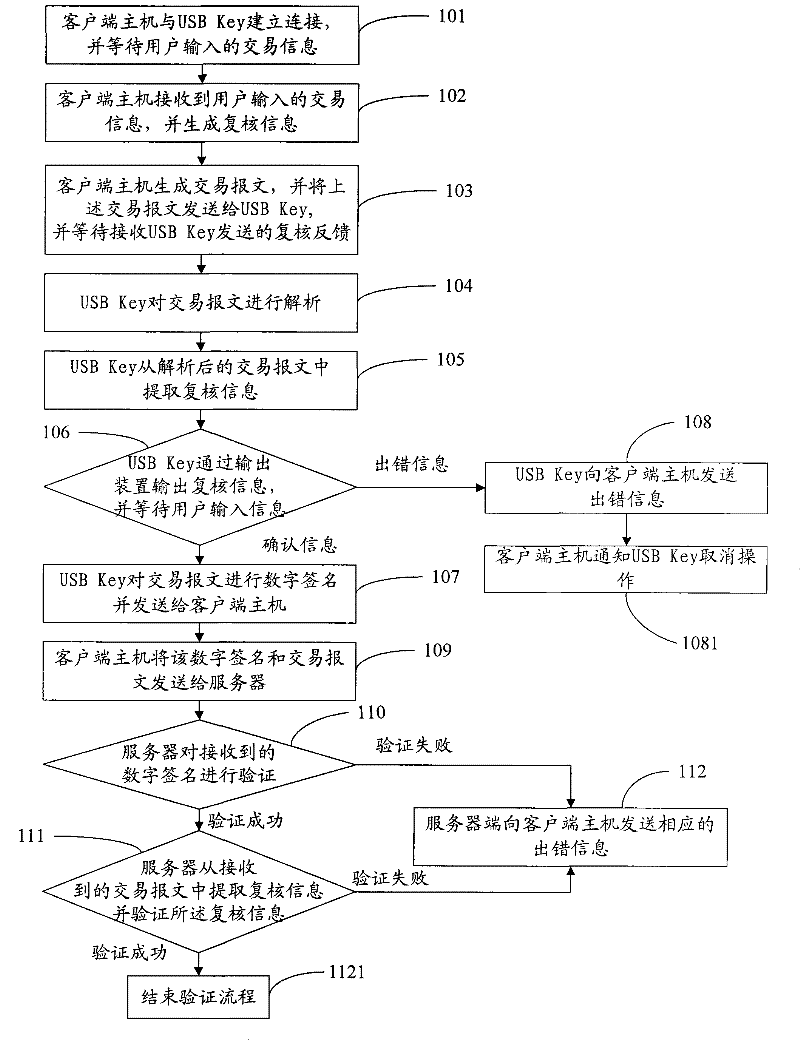
[0119] In this embodiment, a signature method is specifically described by taking the case where the smart key device is a USB Key as an example. In the embodiment of the present invention, the review information identifier is pre-agreed among the client host, the USB Key and the server, wherein the above-mentioned USB Key has an output device and buttons, wherein the output device can be a liquid crystal display or can be It's a voice announcer.
[0120] Such as figure 1 As shown, the method includes:
[0121] 101. The client host establishes a connection with the USB Key, and waits for the transaction information input by the user.
[0122] 102. The client host receives the transaction information input by the user, and uses key fields in the transaction information to form review information.
[0123] In this embodiment, the key fields are: the account number, account name and amount transferred in the business data.
[0124] 103. The client host generates a transaction...
Embodiment 2
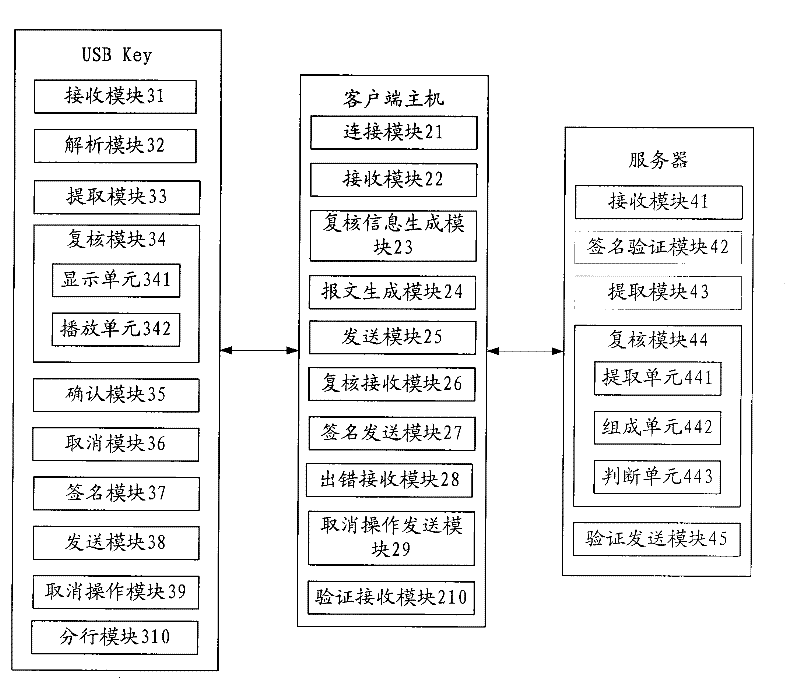
[0164] Corresponding to the method in Embodiment 1 above, this embodiment provides a client host to facilitate the implementation of the above method. Such as figure 2 As shown, the client host includes: connection module 21, receiving module 22, review information generating module 23, message generating module 24, sending module 25, review receiving module 26, signature sending module 27, error receiving module 28, cancel operation The sending module 29 verifies the receiving module 210 .
[0165] The connection module 21 is used to establish a connection with the smart key device, i.e. the USB Key; the receiving module 22 is used to receive the transaction information input by the user, and the transaction information contains key fields; the review information generation module 23 is used to The key field in the information generates review information; message generation module 24 is used for generating transaction message with described review information, review ...
Embodiment 3
[0182] This embodiment discloses a signature system, such as image 3 As shown, the system includes: client host 20 , USB Key 30 and server 40 .
[0183] After the above-mentioned client host 20, USB Key30 and server 40 have pre-agreed on the review information identifier, the client host 20 is used to establish a connection with the USB Key30 and receive the transaction information input by the user. The information contains key fields, after receiving the transaction information, generating review information according to the key fields in the transaction information, using the review information, review information identifier and transaction information to generate a transaction message, and then, Send the generated transaction message to USB Key30, and wait to receive the review feedback sent by USB Key30; USB Key30 is used to receive the transaction message sent by client host 20, and extract the review in the transaction message information, after extracting the re...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap