Fragments-reassembling method of IP messages and device thereof
A technology of IP packets and packets, which is applied in the field of communication, can solve problems such as slow reassembly speed and poor real-time performance of packet reassembly, and achieve the effects of helping maintenance, avoiding processing burden, and avoiding hash conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
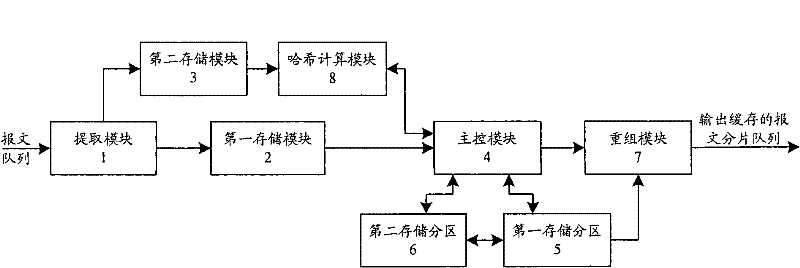
[0040] In this embodiment, a method for fragment reassembly of IP packets is provided, wherein the first storage partition and the second storage partition are used as a buffer group, and the third storage partition and the fourth storage partition are used as a buffer group. blocks.
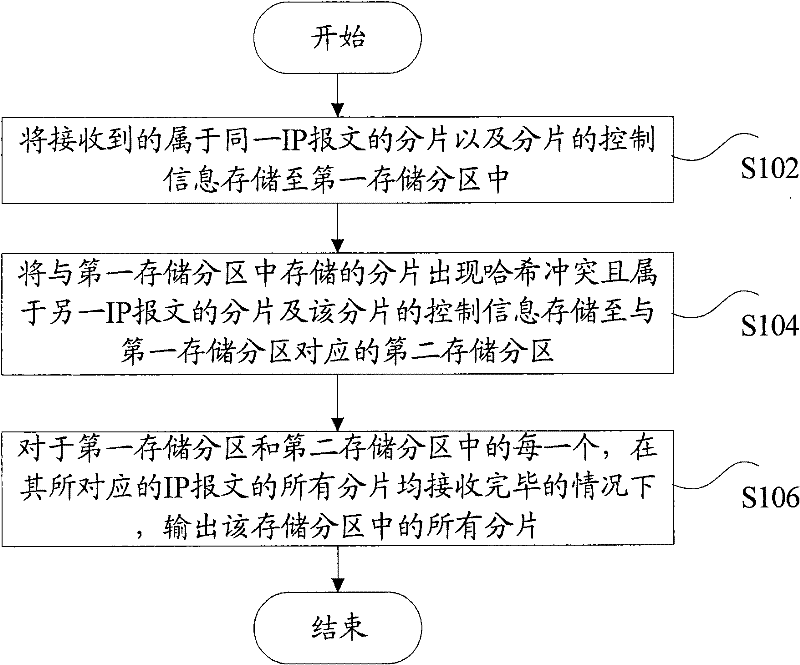
[0041] figure 1 It is a flow chart of the fragment reassembly method for IP packets according to this embodiment. like figure 1 As shown, the method for fragment reassembly of the IP message according to the present embodiment includes:
[0042] Step S102, the control information (preferably, the control information of message can at least include: four-tuple information (comprising source address, purpose address, ID, and protocol) of the fragmentation and fragmentation belonging to the same IP message received )), IP header length, IP packet length, and fragment identifier) are stored in the first storage partition;
[0043] Step S104, there will be a hash conflict with the slice stored ...
Embodiment 2
[0059] In the first method embodiment, the processing method for one hash collision is mainly described, that is, the shard with the hash collision is stored in the second storage partition or the fourth storage partition. In practical applications, there are often more hash collisions. At this time, the number of storage partitions in each group of buffers can be increased.
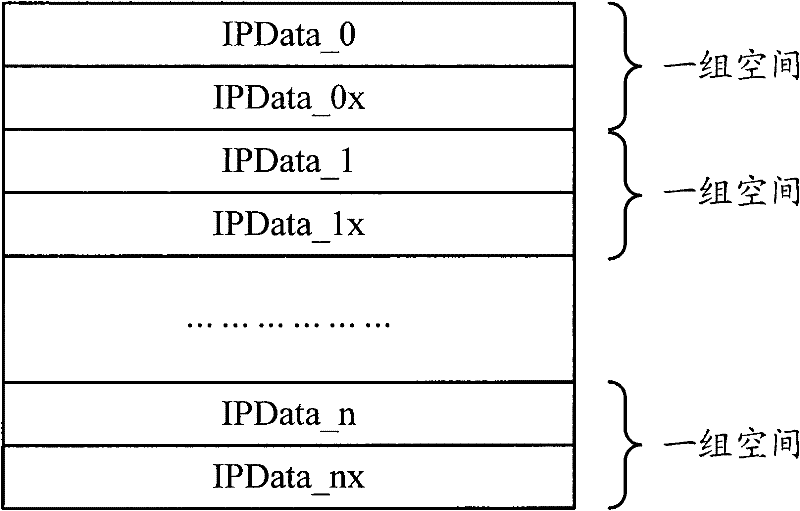
[0060] For example, the three storage partitions of storage partition 1, storage partition 2, and storage partition 3 can be used as a group of spaces, and the three storage partitions of storage partition 4, storage partition 5, and storage partition 6 can be used as another group of spaces. At this time, the fragment received first can be stored in storage partition 1, the fragment received later that has a hash conflict with the fragment stored in storage partition 1 can be stored in storage partition 2, and the fragment received later and stored in The fragments stored in partition 1 and storage part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com