MAC access management method and unit
A technology for access management and channel access, which is applied in the field of MAC access management methods and management units, can solve problems such as waste, inability to guarantee service fairness, waste of network resources, etc., to avoid waste and take into account business priority and time Delayed, high-priority effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
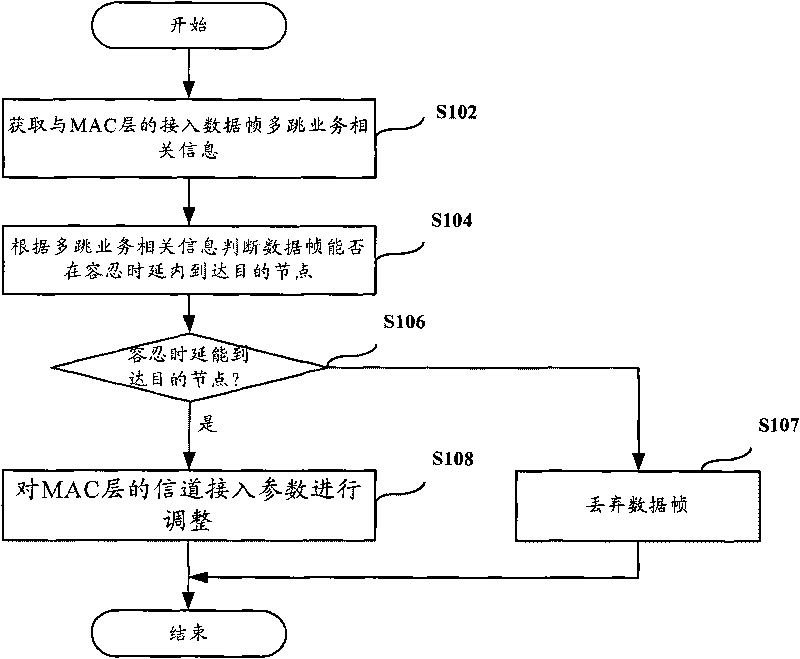
[0032] According to an embodiment of the present invention, a MAC access management method is provided, figure 2 It is a flow chart of Embodiment 1 of the MAC access management method according to the present invention. Such as figure 2 As shown, this embodiment includes:
[0033] Step S102: Obtain information related to the multi-hop service of the access data frame of the MAC layer;
[0034] Step S104: judging whether the data frame can reach the destination node within the tolerance delay according to the multi-hop service related information;
[0035] Step S106: If the data frame can reach the destination node within the tolerance time delay, execute step S107, otherwise execute step S108;
[0036] Step S107: Discard the data frame, end the process, and the upper layer decides to retransmit or terminate the service;
[0037] Step S108: Adjust the channel access parameters of the MAC layer.
[0038] In this embodiment, by collecting multi-hop service-related informat...
Embodiment 2
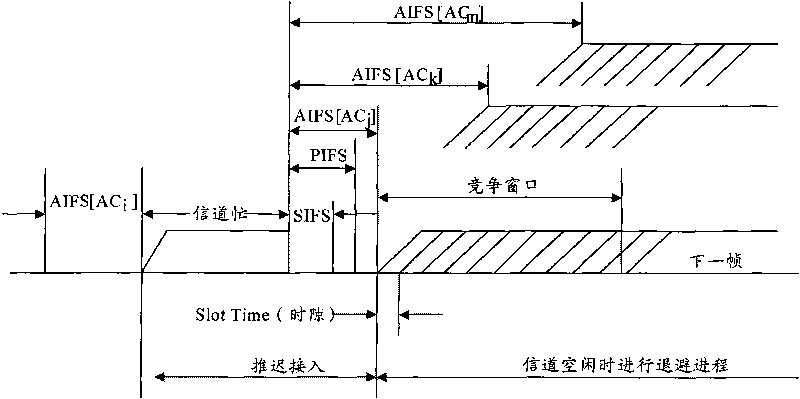
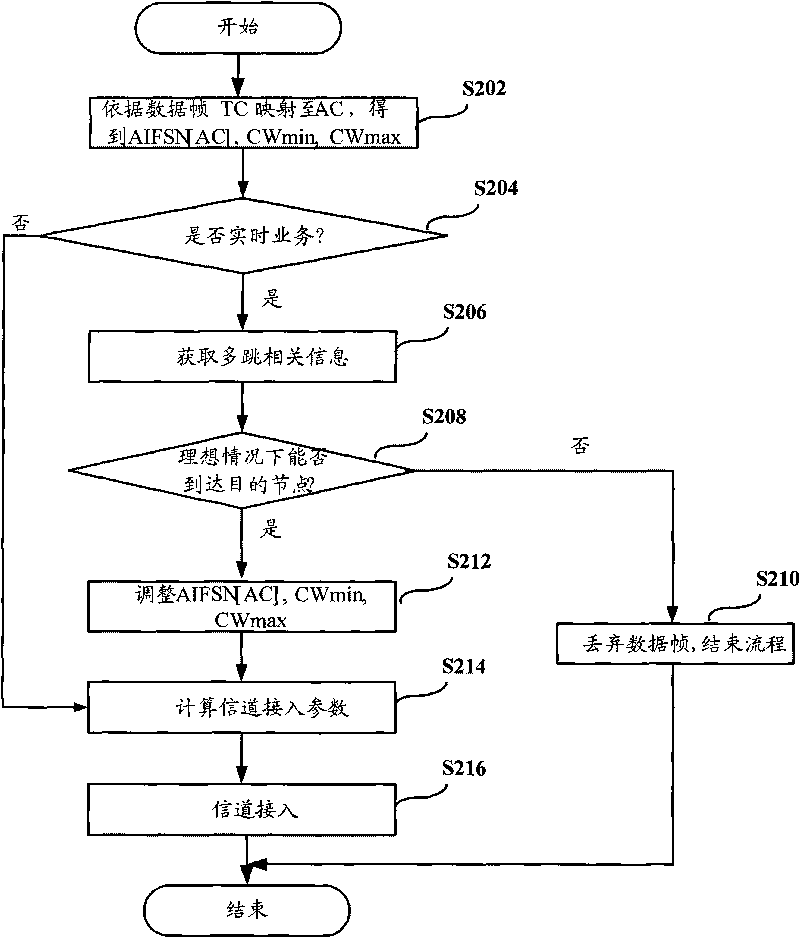
[0040] image 3 It is a flowchart of Embodiment 2 of the MAC access management method according to the present invention. This embodiment introduces the collection, judgment and application of real-time service delay information, and adjusts the channel access parameters obtained according to EDCF, so that data frames with short remaining lifetimes can obtain a higher channel access priority. Such as image 3 As shown, the channel access parameter adjustment process of the MAC access management method in this embodiment includes:
[0041] Step S202: Map the service category TC to the access category AC according to the EDCF mechanism, obtain the AC mapped according to the data frame TC, and further obtain AIFSN[AC], CWmin, CWmax;
[0042] Step S204: Determine whether it is a real-time service, if yes, enter step S204, otherwise, enter step S214;
[0043] Step S206: Obtaining multi-hop related information may require a cross-layer design mechanism;
[0044] Step S208: Determi...
Embodiment 3
[0052] The process of Embodiment 2 of the present invention is described in detail below by way of example:
[0053] 1) According to the EDCF mechanism (there are unified and detailed regulations in the IEEE 802.11e standard document), the service category TC is mapped to the access category AC, and the AC mapped according to the data frame TC is obtained, as shown in Table 1. According to this mapping relationship table, The priorities of TCs are mapped to ACs:
[0054] Table 1 Mapping relationship between TC priorities and ACs
[0055] TC priority (with 802.1D
same)
access category
AC
Corresponding business
0
0
do your best
1
0
do your best
2
1
do your best
3
2
video
4
2
video
5
2
video
6
3
voice
7
3
voice
[0056] Further obtain AIFSN[AC], CWmin, and CWmax according to the obtained AC, as shown in Tab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com