Dynamic authorizing method of data based on ITSM system
A technology of dynamic authorization and system data, applied in the direction of program control devices, etc., can solve the problems of wrong output results, difficult software maintenance, failure, etc., to reduce complexity and improve scanning efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The ITSM system-based data dynamic authorization method proposed by the present invention is described as follows in conjunction with the accompanying drawings and embodiments.
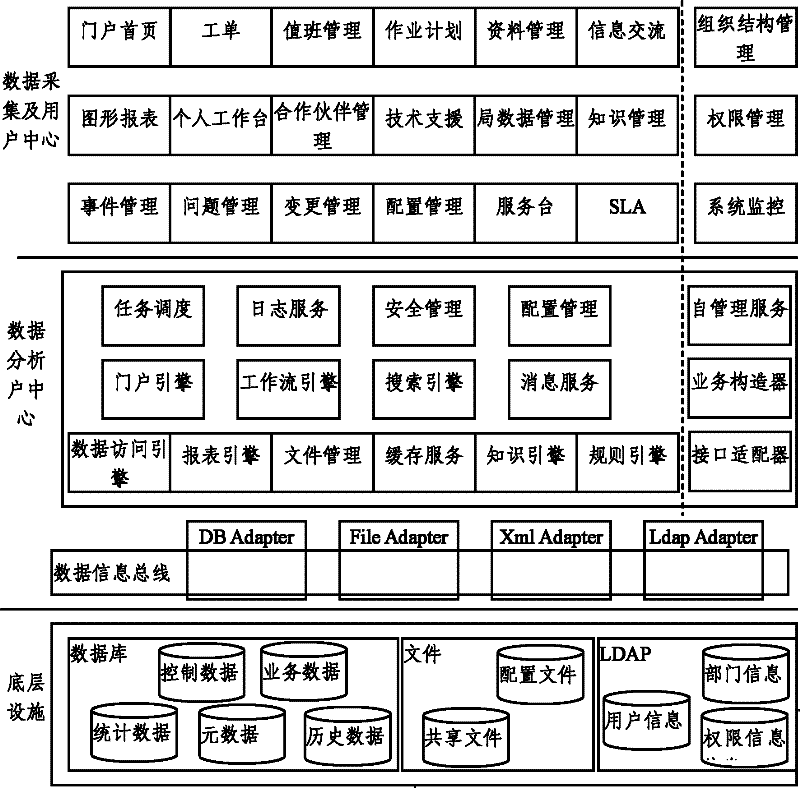
[0046] Such as figure 1 As shown, it is a structural diagram of the ITSM system based on the present invention, and a typical ITSM model is divided into the following layers:
[0047] User layer. The user layer is the interface for users to use the system. Employees can make requests to the system to query existing relevant data and obtain business data;
[0048] Data collection, data collection mainly refers to the use of some methods to search or data mining business data;
[0049] Data analysis center, the data analysis center is the core of the model, it is responsible for managing and storing the user's business data;
[0050] The underlying facility, the underlying facility is a logical structure that uses the network to connect external users and enterprises. It is a virtual network fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com