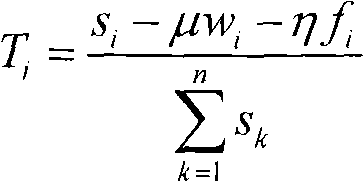Method for sorting network virus reports
A sorting method and network virus technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as large-scale spread, confidential information theft, wide coverage, etc., to achieve comprehensive sorting, easy implementation, simple and clear Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] 1. Virus report submission and processing process
[0017] When the user terminal finds that its computer is running abnormally, such as the central processing unit works at a peak when not performing heavy work, the memory is heavily occupied, the hard disk is constantly working, or the free space is shrinking abnormally, etc., or a suspected malicious computer is found in the computer memory. process, or when a suspected malicious file is found on the auxiliary storage of the computer, or when the local anti-virus software finds that a certain software is very suspicious, but it is not enough to determine that it is a malicious software containing a network virus program, the system can follow the following procedures Work:
[0018] ① The user terminal sends a report and related virus samples to the portal node.
[0019] ② After the system server receives the report, it first compares it with the report in the virus report database.
[0020] There are two types of r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com