System and method for realizing authentication monitoring
A monitoring server, illegal technology, applied in the field of communication, can solve the problems of inability to grasp the specific situation of the functional module F, inability to deal with infringements, etc., to achieve the effect of ensuring healthy development, protecting intellectual property rights, and reducing harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
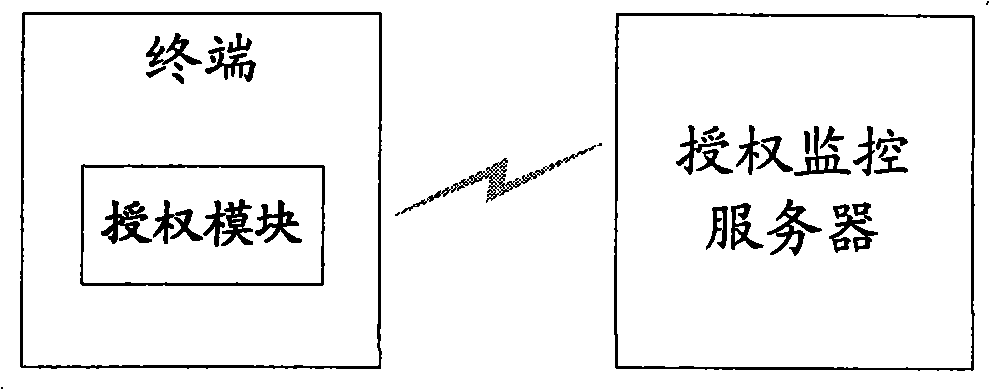
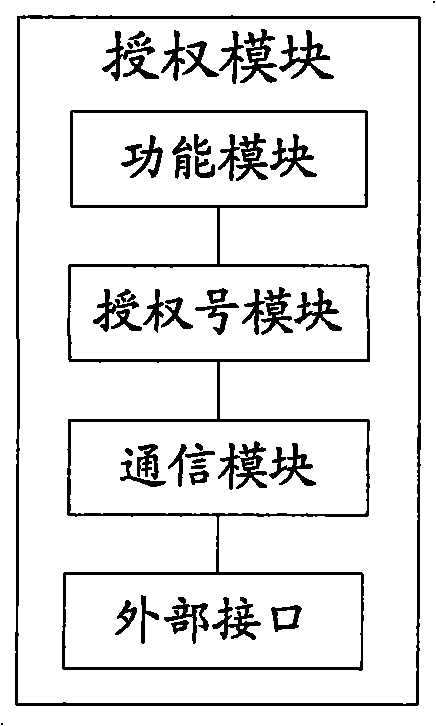
[0054] In the present invention, it is possible to monitor whether the scope of authorization is exceeded, and the implementation is as follows: when the function module is triggered, the terminal sends the manufacturer identification, authorization number and terminal equipment identification to the authorization monitoring server; The comparison between the number of device identifications corresponding to the authorization number and the scope of authorization determines whether there is illegal infringement. If it is determined that there is illegal infringement, the authorization monitoring server may further identify the manufacturer identifier and the corresponding authorization number as an authorization exception and / or generate an alarm.
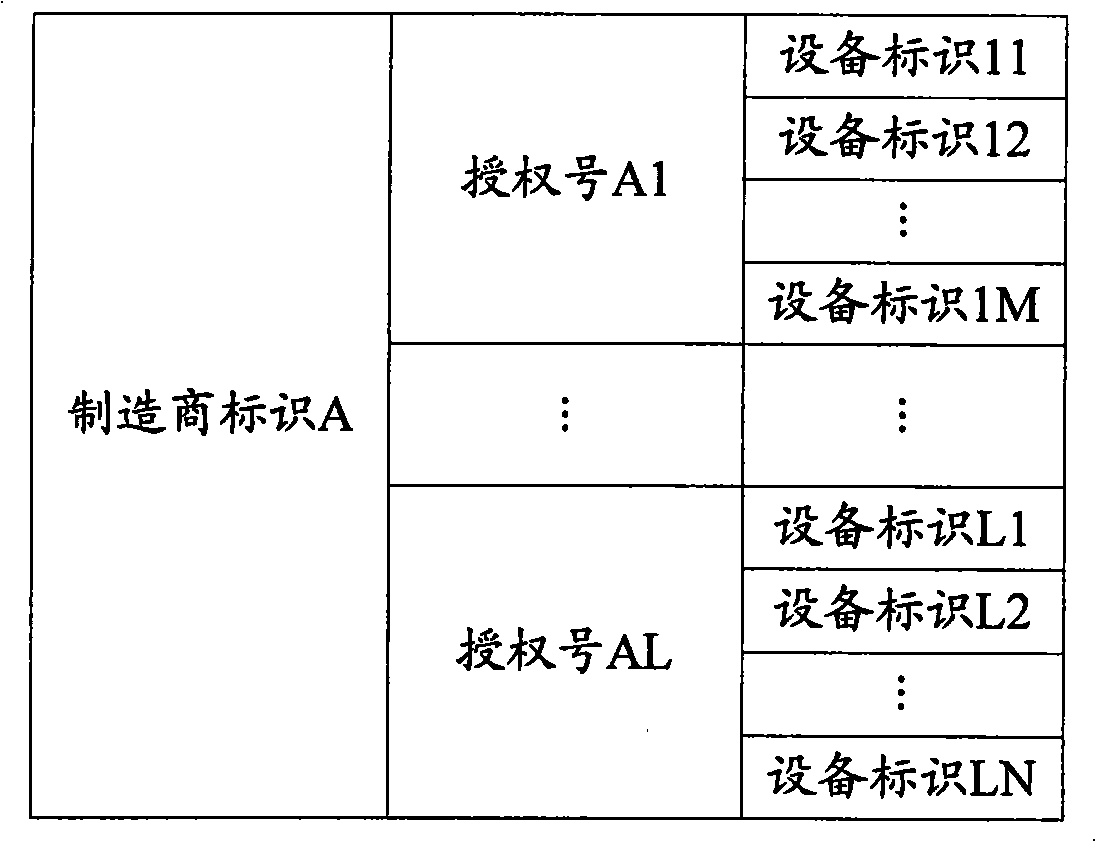
[0055] The authorization monitoring server stores the manufacturer ID and the corresponding authorization number. In this way, before counting the number of device IDs corresponding to the manufacturer ID and the authorization numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com