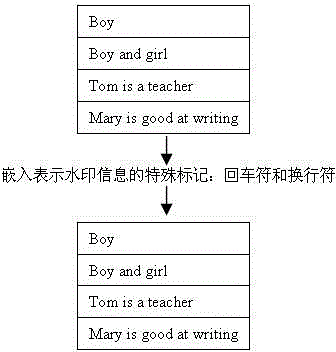
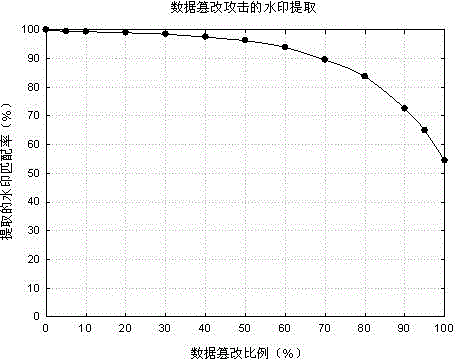
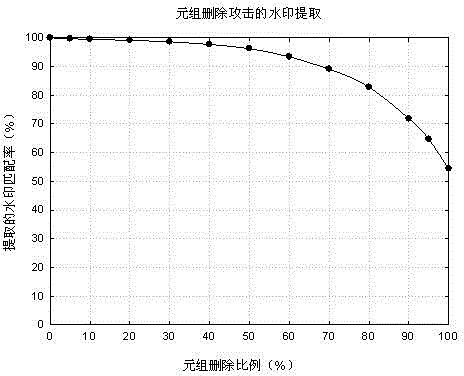
Text-type attribute-based relational database watermark embedding method
A technology of watermark embedding and text attribute, applied in the field of database security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] A watermark embedding method for a relational database based on text-type attributes. The watermark embedding means that the database owner mixes the binary watermark image with the text-type data in the database through a watermark embedding algorithm to protect the copyright of the database. The specific calculation steps are as follows:
[0055] (1) Set the database owner to determine some secret information: binary watermark image W, user key Key and group adjustment factor N.
[0056] (2) Digitize the binary watermark image into a binary sequence Wm_Bits represented by 0 and 1, calculate the watermark symbol length Wm_length, and calculate the group size e by formula (6).
[0057] (3) Based on the group size e, calculate the tuple mark and the hash remainder r according to the formulas (1) and (7) i .mod(1≤i≤η), and hash the remainder r i .mod (1≤i≤η) sorts the tuples in increasing order to realize the grouping of tuples.
[0058] (4) Embed each watermark symbol ...
Embodiment 2
[0062] A watermark extraction method for relational databases based on text attributes. If the owner A of the database R suspects that the database R' used by the user B is an illegal copy of R, then A can obtain the binary data hidden in R' through the watermark extraction algorithm. Value image watermark, in order to prove that the database R' is illegally embezzled. Watermark extraction is the reverse of watermark embedding process. The specific calculation steps of the extraction method are as follows:
[0063] (1) Some secret information known by A: user key Key, image watermark symbol length Wm_length (Wm_length=watermark image length Width×watermark image width Height) and group adjustment factor N.
[0064] (2) Calculate the remainder r of each tuple according to formulas (1), (6), and (7) i .mod, 1≤i≤η. based on r i .mod(1≤i≤η) press r for all tuples of R' i .mod (1≤i≤η) is sorted in increasing order to realize dynamic grouping of tuples.
[0065] (3) The waterm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com