Software credibility measurement and estimation method based on data mining
A data mining and credibility technology, applied in the fields of software engineering and information security, can solve untrustworthy explicit and implicit problems
Inactive Publication Date: 2011-09-21
BEIJING UNIV OF POSTS & TELECOMM
View PDF0 Cites 19 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
When a user makes a decision to trust the software, it means that the user also bears the explicit and implicit risks caused by the untrustworthy software
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
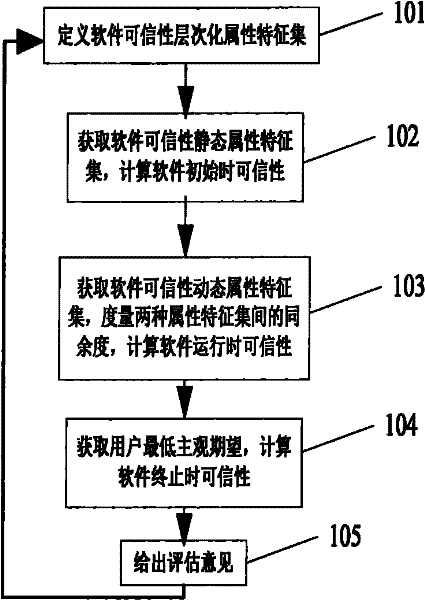
[0102] The algorithm flow for implementing this method is as follows:
[0103]
[0104]
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
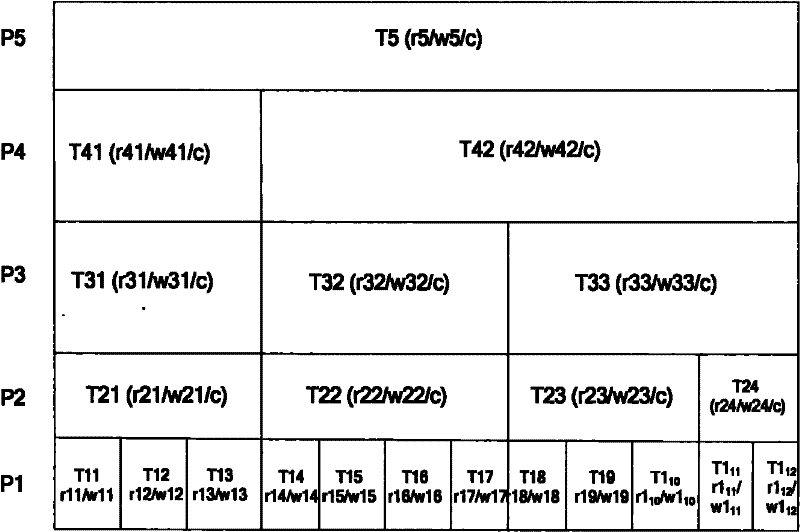
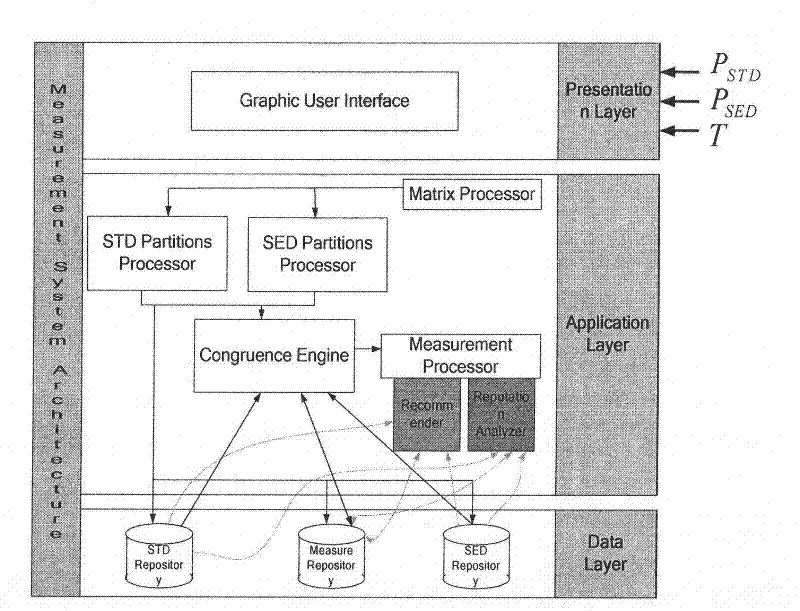
The invention discloses a software credibility measurement and estimation method based on data mining, and the method comprises the following steps of: (1) on the basis of a concept hierarchy, defining a construction relation of each attribute weight and an adjacent layer attribute set in the same attribute set; (2) based on a software testing environment, providing a credibility computing base operator facing to an attribute feature set by combining with an artificial intelligence theory; (3) based on a software blackbox testing method, combining a data mining theory, obtaining a software credibility static state attribute feature set and a credibility computing base operator by using the blackbox testing, computing the initial credibility of the software layer by layer, obtaining a software dynamic attribute feature set by testing the software when running, and obtaining the credibility of the software in running by using a congruence measurement operator; (4) defining the lowest subjective expectation to the attribute feature set through a user, and computing the credibility of the software when in termination layer by layer; and (5) providing an estimation recommendation to the credibility of the to-be-estimated software.
Description
technical field [0001] The invention relates to the fields of software engineering and information security, in particular to measurement and evaluation of software credibility. The method disclosed in the present invention aims to provide a method of dividing software credibility to form an attribute feature set using the concept hierarchy method, and by setting different weights, construction types and confidence probabilities, according to the congruence measurement operator based on data mining Software credibility assessment method for software credibility. Background technique [0002] Verification and Validation are one of the basic principles and methods used to build software quality in the research field of software engineering disciplines [1] . In the past decade, Internet-based software applications have gradually evolved from the closed and centralized private R&D environment since the last century, and the specific function usage mode for specific user groups...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F11/36
Inventor 袁玉宇韩强刘川意张旸旸杨金翠
Owner BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com