Adaptive active defense realizing method and system in WSN (wireless sensor network)
A technology of active defense and implementation method, applied in electrical components, wireless communication, network topology, etc., can solve the problems of not considering the active defense of network attacks, unable to solve network attack defense, increase network transmission overhead, etc., to achieve security and robustness Performance improvement, additional transmission consumption reduction, and the effect of life cycle growth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
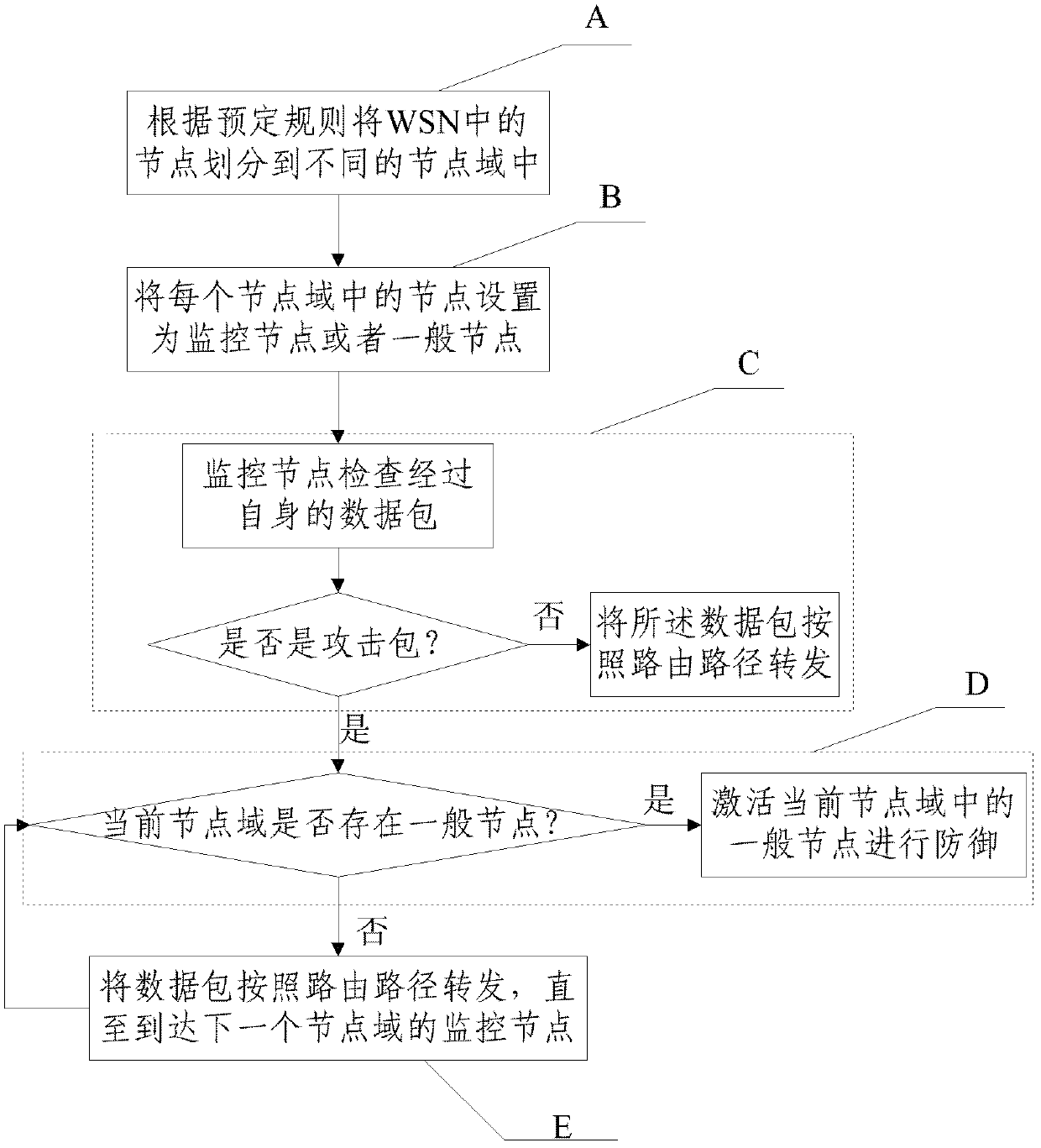
Embodiment Construction
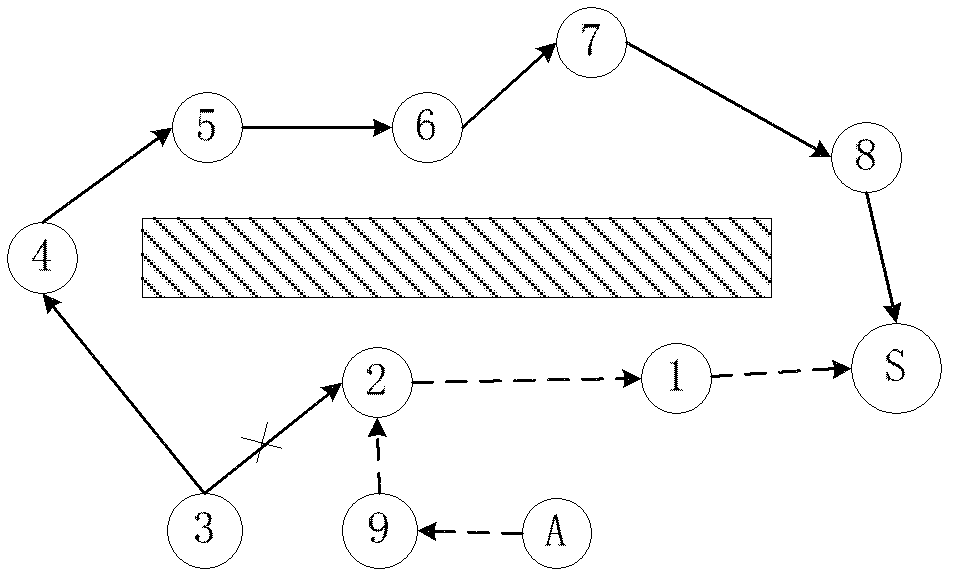
[0063] In WSN, the network attacks on the physical layer and the link layer have been basically solved, but although many solutions have been proposed for the attacks on the network layer, they are basically evasive strategies, and effective security protection cannot be carried out. The essential reason is that it is impossible to determine the source node under attack and to defend on the source node in time. Below we will specifically illustrate the adverse consequences of this evasion strategy on WSNs through greedy destruction attacks.
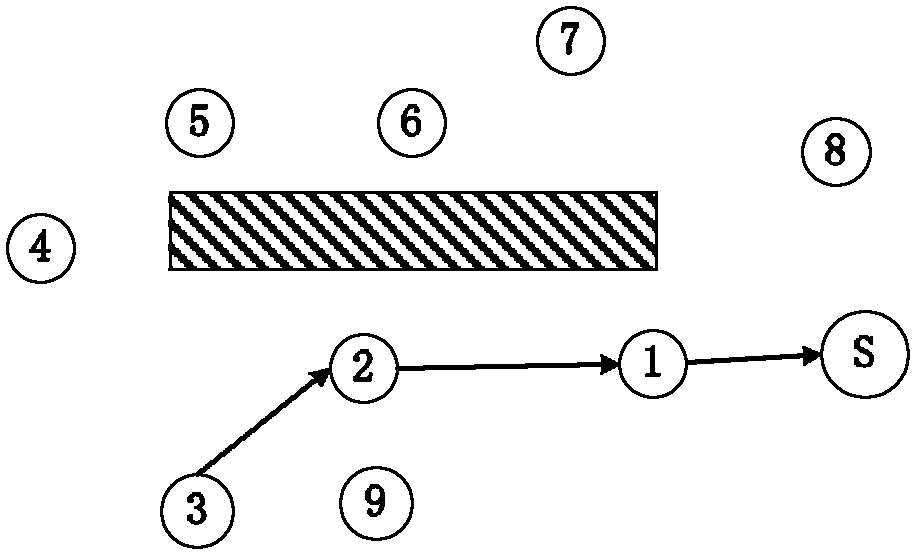
[0064] figure 1 It is a schematic diagram of data transmission when the existing WSN is not attacked by greed. Such as figure 1 As shown, S is the terminal node, the main task is to forward the command of the terminal PC and send the data transmitted by the node to the terminal PC; nodes 1-9 are general nodes, the main task is to collect data and forward the data packets of neighboring nodes . At this time, node 3 sends data to termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com