Authentication method and device based on speech recognition
An authentication device and voice recognition technology, applied in the field of identity authentication, can solve the problems of stealing user's private information, counterfeiting, and low security of identity authentication methods, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
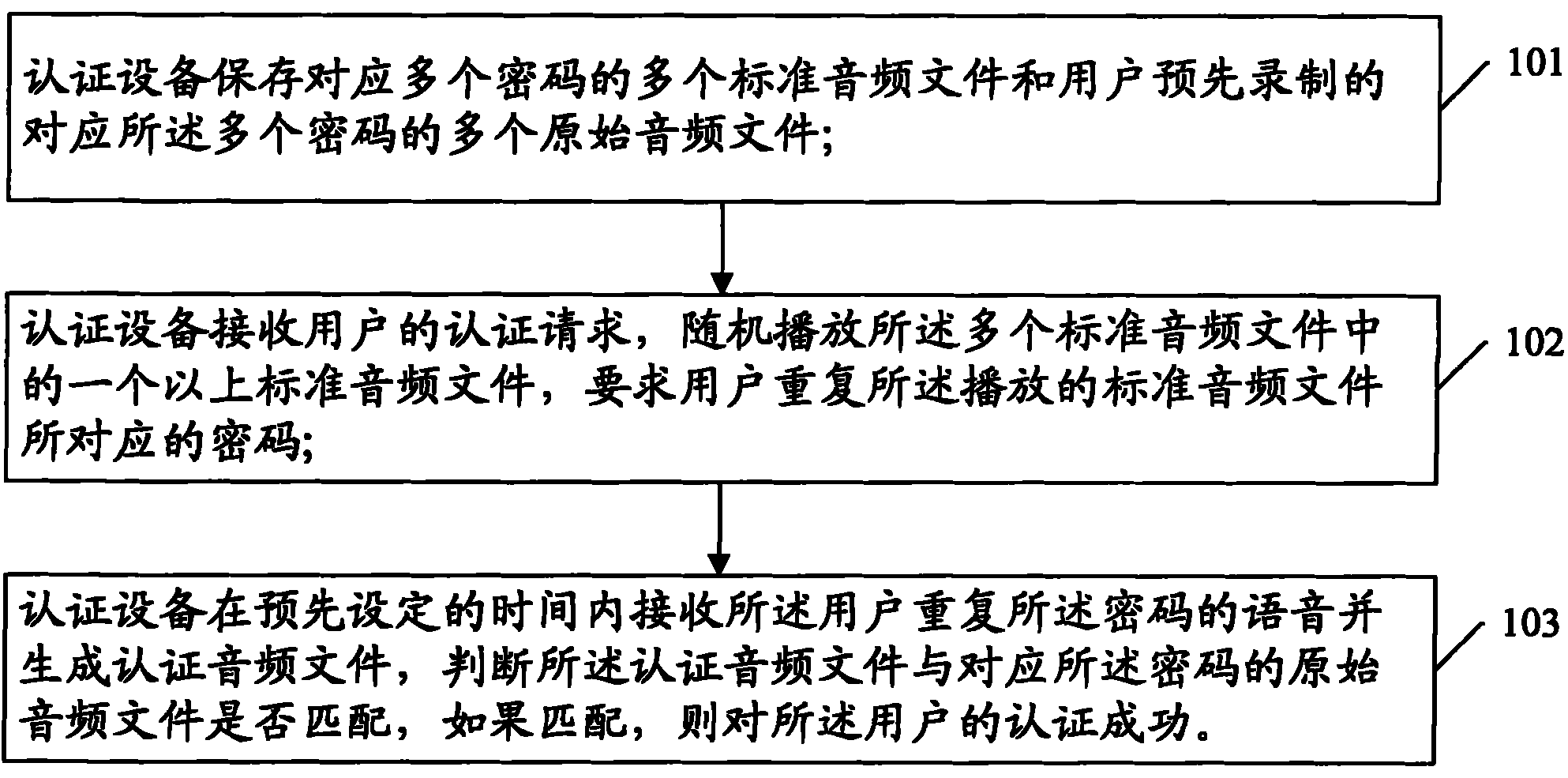
[0022] The present invention proposes an authentication method based on speech recognition, such as figure 1 It is a flow chart of the voice recognition-based authentication method of the present invention, the method comprising:
[0023] Step 101: The authentication device saves multiple standard audio files corresponding to multiple passwords and multiple original audio files corresponding to the multiple passwords pre-recorded by the user;
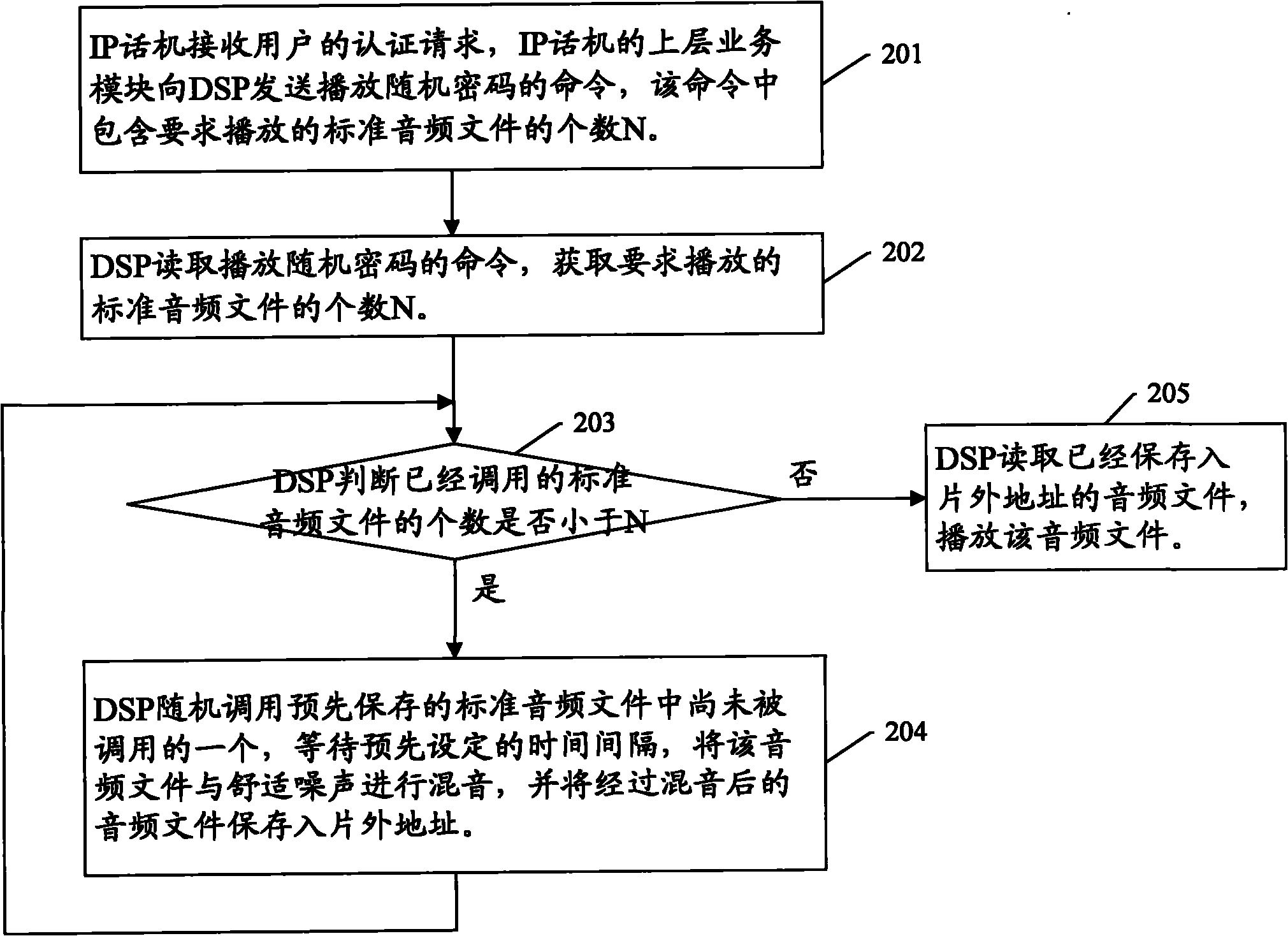
[0024] Step 102: The authentication device receives the user's authentication request, randomly plays more than one standard audio file among the plurality of standard audio files, and requires the user to repeat the password corresponding to the played standard audio file;
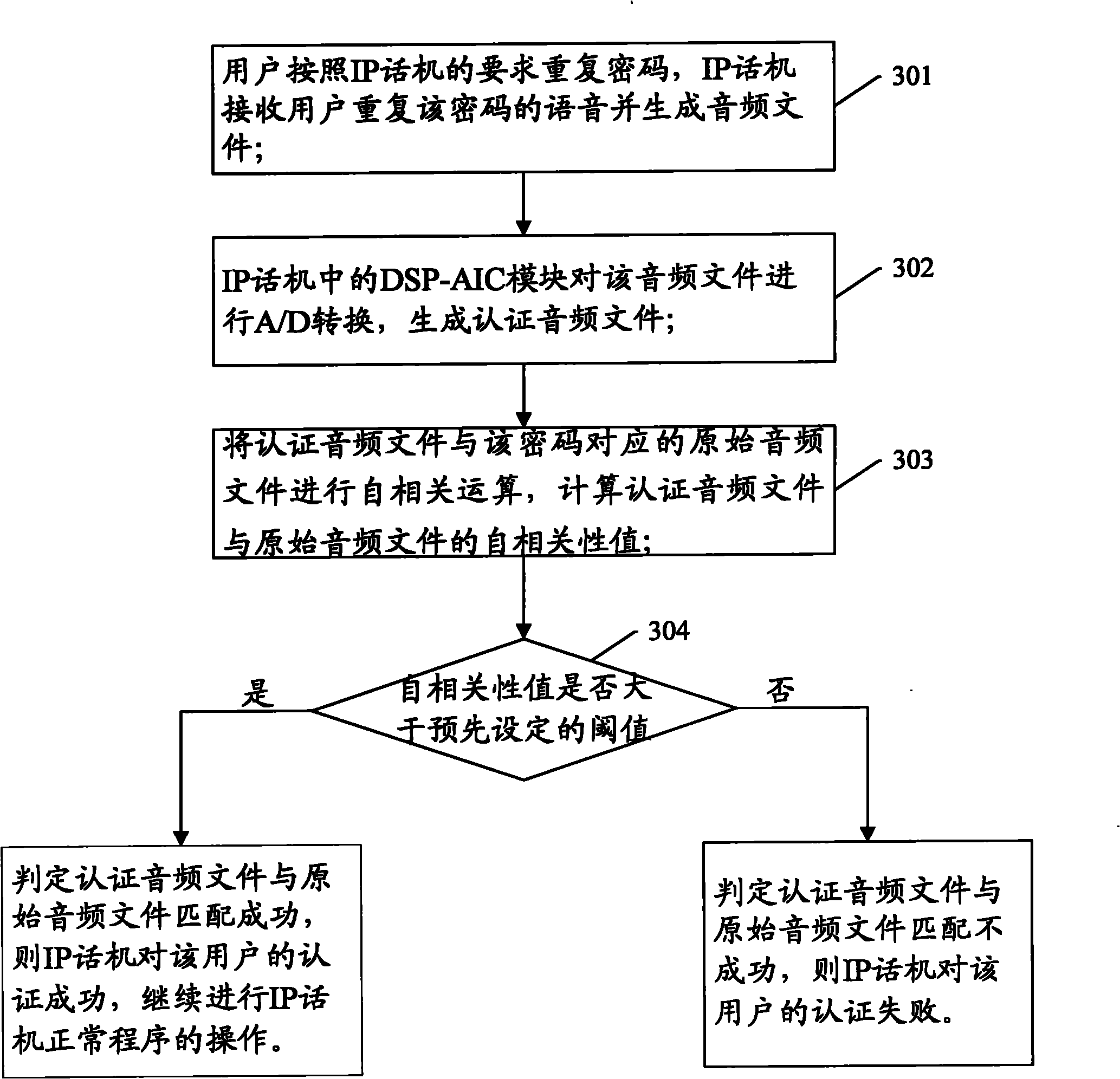
[0025] Step 103: The authentication device receives the voice of the user repeating the password within a preset time and generates an authentication audio file, and judges whether the authentication audio file matches the original audio file corresponding to the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com