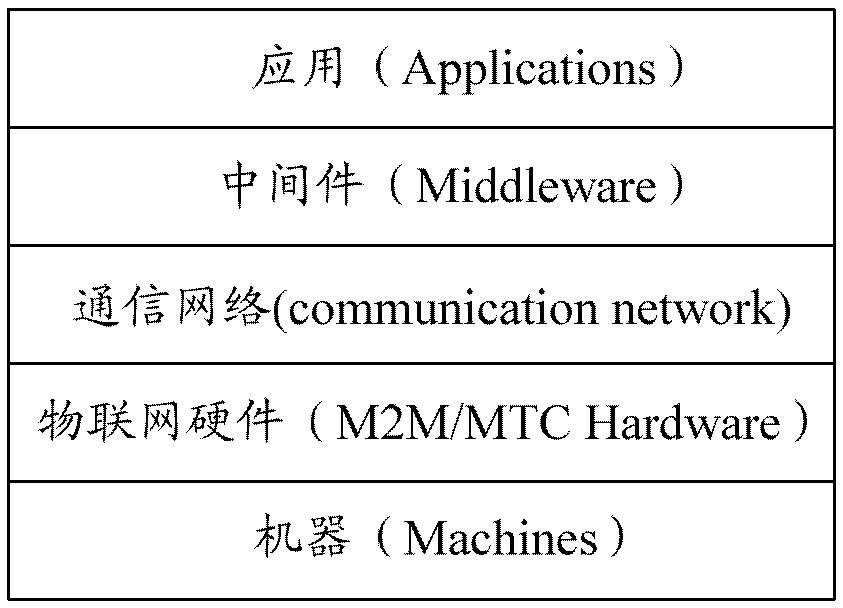
A network access method and system
A network access and network technology, applied in the field of communications, can solve problems such as no solution, and achieve the effects of improving user satisfaction, ensuring access quality, and reducing collisions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
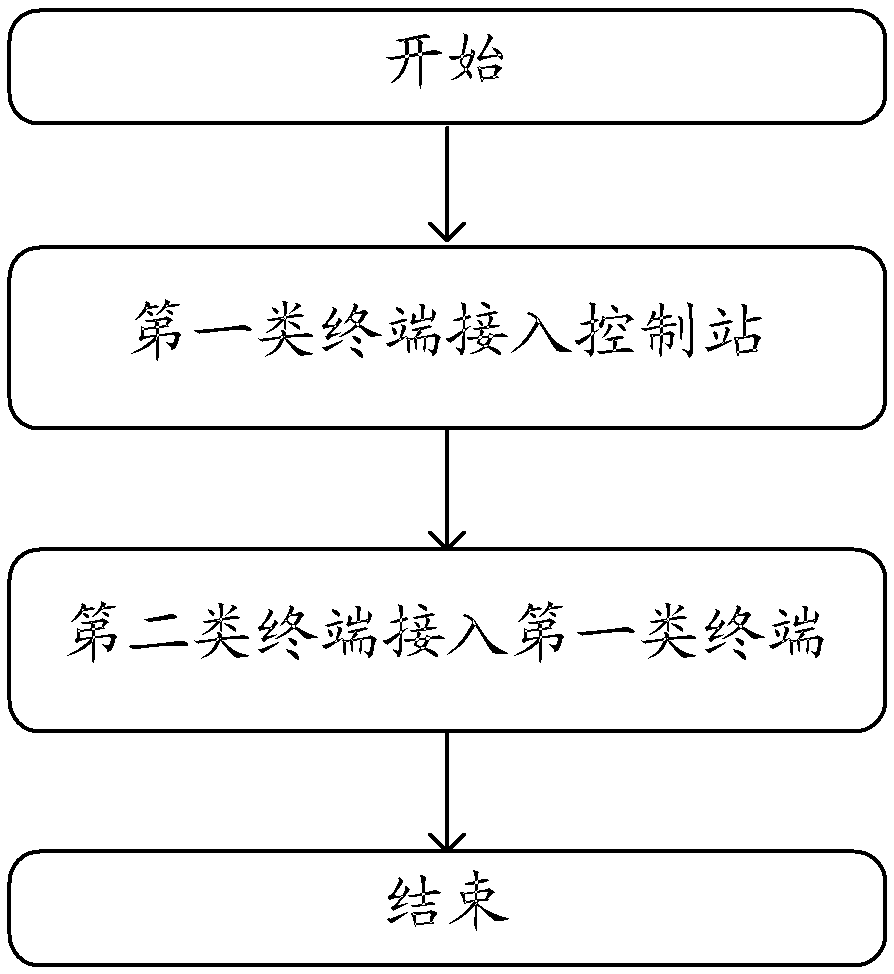
[0071] Embodiment one, such as Figure 5 shown.
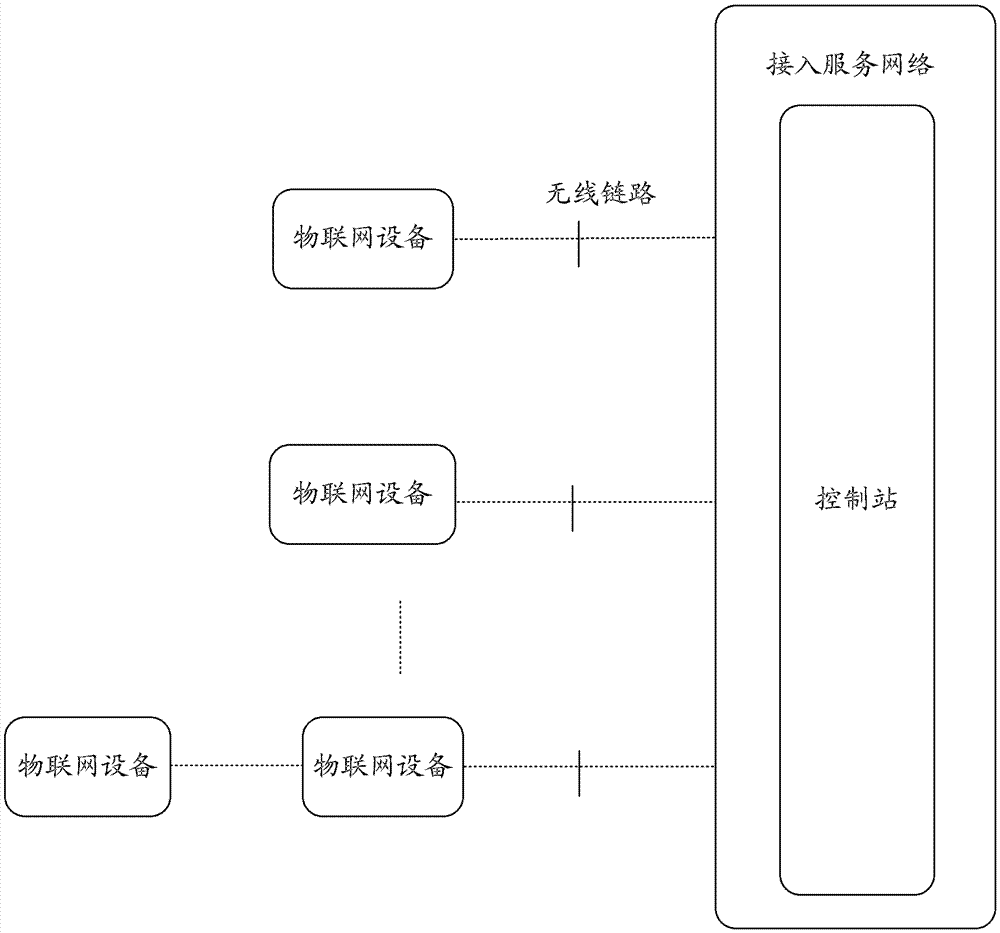
[0072] The network or the control station broadcasts the hierarchical access information through the air interface of the control station.
[0073] The terminal of the first type that receives the hierarchical access information accesses the control station according to the normal network access process.
[0074] The terminal of the first type receives resource information allocated by the control station for accessing the terminal of the second type.
[0075] The second type of terminal accesses the first type of terminal according to a normal network access process on the resource. Since the control station has marked the hierarchical access information on the air interface, the second type of terminal will not attempt to access the control station according to its own category.
[0076] Further, the resource information for accessing the second type of terminal is sent by the first type of terminal to the second type of t...
Embodiment 2
[0081] Embodiment two, such as Figure 6 shown. The difference between Embodiment 2 and Embodiment 1 is that the process of the control station sending the resource accessed by the terminal of the second type to the terminal of the first type is removed, and the resource used for access can be scheduled by the terminal of the first type.
[0082] The network or the control station broadcasts the hierarchical access information through the air interface of the control station.
[0083] The terminal of the first type that receives the hierarchical access information accesses the control station according to the normal network access process.
[0084] The second type of terminal accesses the first type of terminal according to a normal network access process. Since the control station has identified the layered access information on the air interface, the second type of terminal will not attempt to access the control station according to its own category.
[0085] Further, the...
Embodiment 3
[0091] Embodiment three and embodiment four removed the last step in embodiment one and embodiment two respectively, can refer to respectively Figure 7 , Figure 8 . In embodiment three and embodiment four:
[0092] The terminal of the first type may not forward the information of the terminal of the second type to the control station during the access process. At this time, the first type of terminal has a full access control function.
[0093] The terminal of the first type may only forward the information of the accessed terminal of the second type to the control station or the network. From the point of view of the access layer of the control station, all information comes from the first type of terminal. The advantage of doing this is that the overhead between the first type terminal and the control station can be further reduced.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com