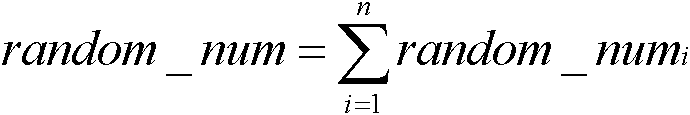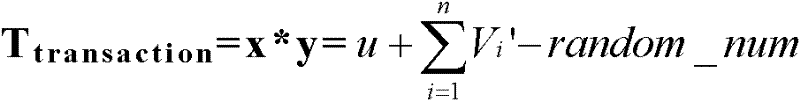Network transaction method based on privacy protection trust evaluation
A technology for network transactions and privacy protection, which is used in sales/rental transactions, electrical components, transmission systems, etc., to achieve the effect of clear concept, privacy protection security, and wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0020] Embodiment 1 Embodiment of network transactions based on privacy protection trust evaluation
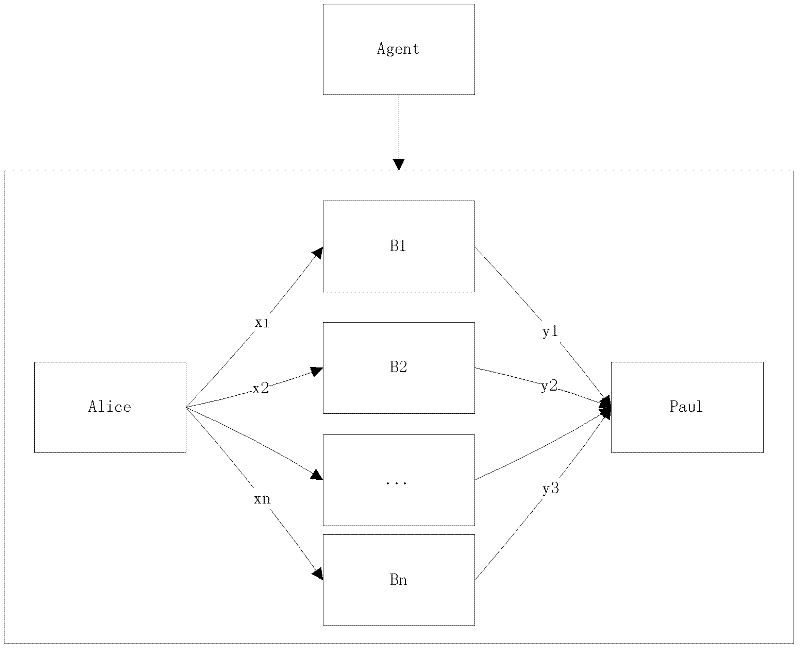
[0021] The network environment of large-scale deployment of the present invention is implemented such as figure 1 Shown, denoted as graph G (V, E) said. Among them, V is a set of all points, each point in the figure represents each node in the network, E is a set of edges, each edge in the figure represents a communication link between nodes, and there is a direct link between any two nodes in the figure Or an indirect communication link, that is, the graph must be a Unicom graph. The integrated network environment consists of |V| ordinary nodes and a semi-honest third-party node Agent, where semi-honest means that the node follows the protocol in the network like other nodes, but it can arbitrarily use all intermediate data to infer other nodes private data. According to actual network conditions, the range of V is between 2 and 100,000. The semi-honest node Agent can com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com