Method for controlling authority of mobile equipment under different conditions
A technology of mobile devices and permissions, which is applied in the direction of instruments, time registers, and individual input/output registers, etc., and can solve problems such as mobile device permission settings
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
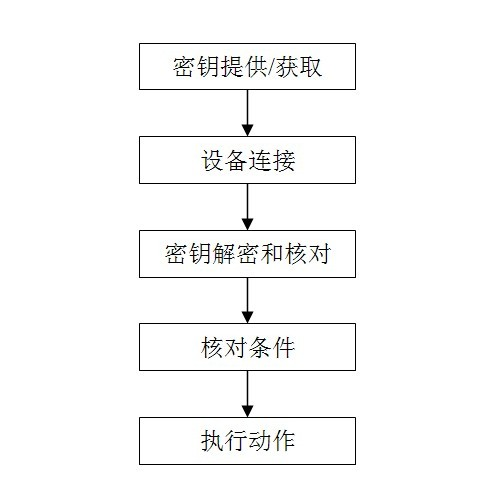
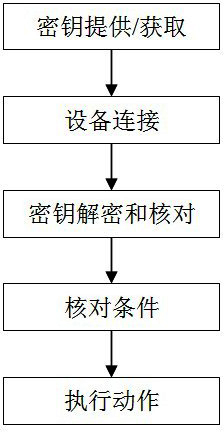
[0024] Example 1: In the simplest locking system, the key cooperates with the key to let the key perform a certain action, and the locking system enters the state of no audit, that is: any key can pass, and after passing , the locking system will also record the key. When connecting for the second time, the mobile device without administrator authority can use the same key as the first time to connect with the locking system and control the locking system. In this way, a mobile device without administrator rights has obtained an "invisible key" with no specific shape, color, and intangibility.
example 2
[0025] Example 2: In a complex centrally managed access control system, the rights of a mobile device without administrator rights are implanted through a device with management rights, that is, a mobile device without administrator rights is connected to a device with administrator rights. Connection, the device with administrator rights sends a key that can be recognized by the access control system to the mobile device without administrator rights, and the mobile device without administrator rights can control some functions of the access control system by using this key (open , off, etc.).
example 3
[0026] Example 3: In hotels, hotels, schools, companies, etc., the device with administrator privileges also assigns information including time intervals and environmental parameters in the key to mobile devices without administrator privileges, such as: When a passenger checks into a certain hotel and has paid a one-day deposit, the front desk of the hotel will require the customer's mobile device (such as a mobile phone, tablet, etc.) to connect to the hotel's computer system (a device with administrator authority), and then, The computer at the front desk of the hotel (a device with administrator authority) will send a key to the customer's mobile device (such as a mobile phone, a tablet, etc.), and the key is specially encrypted and stored in the customer's mobile device (such as a mobile phone, a tablet, etc.) computer, etc.).
[0027] Step 2: Device connection. A mobile device without administrator rights passes through step 1, which is equivalent to obtaining an "invis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com