Two-factor authentication method based on digital certificate and biological identification information
A biometric information and digital certificate technology, applied in the field of accounting voucher management system, can solve the problems of enterprise loss, being used by others, and the authenticity of loss transactions, and achieve the effect of ensuring absolute security and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
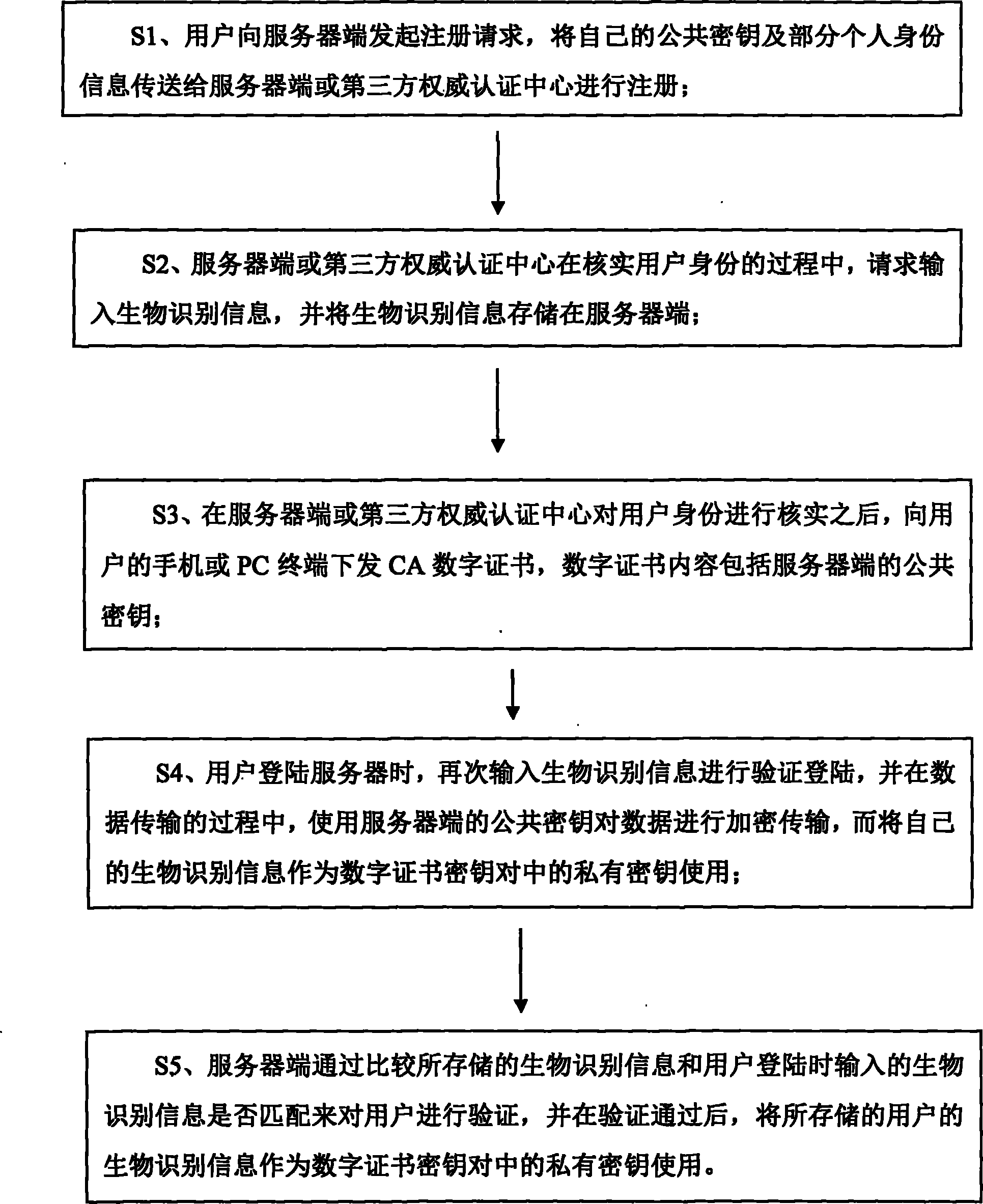
[0014] In order to make the above-mentioned purposes, features and advantages of the present invention more obvious and understandable, the realization principle of the present invention is described in detail below, and the present invention is further described in detail in conjunction with the accompanying drawings:
[0015] In 1976, American scholars Dime and Henman proposed a new key exchange protocol in order to solve the problems of information public transmission and key management, allowing communication parties on insecure media to exchange information and securely reach an agreed key. This is the "public key system". Compared with "symmetric encryption algorithm", this method is also called "asymmetric encryption algorithm".
[0016] Unlike symmetric encryption algorithms, asymmetric encryption algorithms require two keys: a public key (publickey) and a private key (privatekey). The public key and the private key are a pair. If the data is encrypted with the public...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com