Method for checking an optical security feature of a valuable document
A security feature, optical security technology, used in computer parts, banknote authenticity testing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
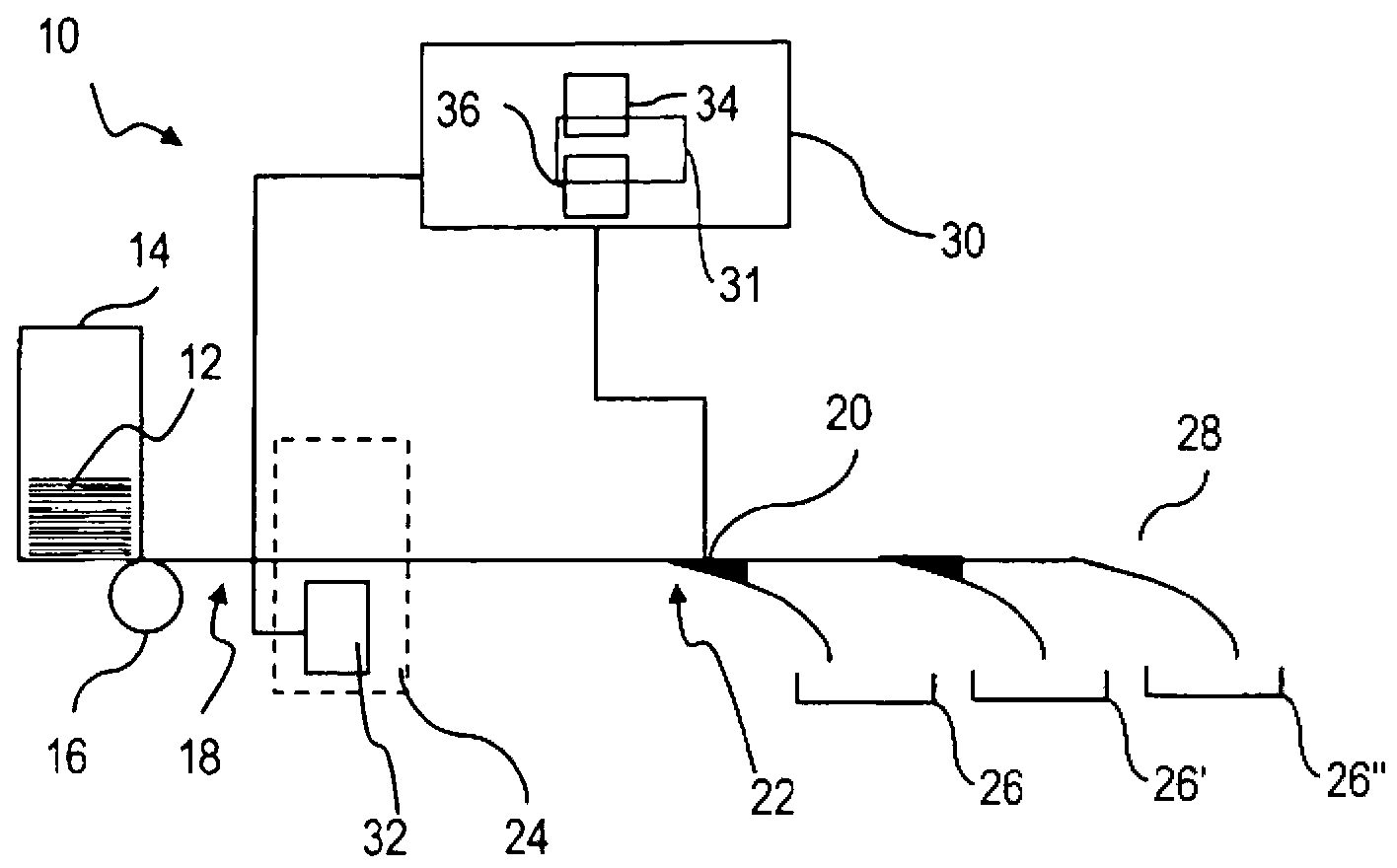
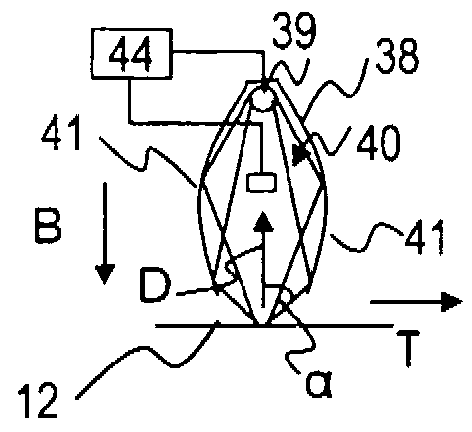
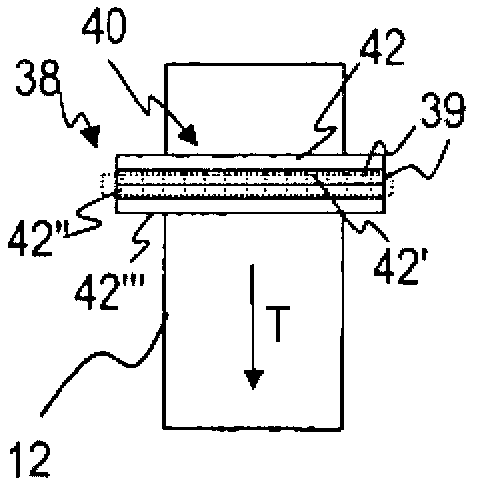
[0065] figure 1 The means 10 for processing value files (in this example banknote processing means) in the banknote form are used for checking the authenticity of value files 12 and for sorting depending on the result of the authenticity check, etc. Wait. The apparatus 10 has: an input pocket 14 for the input of value files 12 to be processed; a singler 16 which can access the value files 12 in the input slot 14; successively arranged gates 20 and 20 ′; and a respective output slot 26 or 26 ′ or 26 ″ after each gate, or at one end of the transport path 22 following both gates. Along the transport path 22 given by the transport device 18 , before the gate 20 and after the picker 16 is arranged a sensor assembly 24 for acquiring properties of the value files 12 fed in individual form, and Used to form sensor signals exhibiting the described properties. The control device 30 is connected via signal connections at least to the sensor assembly 24 and to the doors 20 and 20' and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com