Bug attack graph generation method based on script
An attack graph and vulnerability technology, applied in the field of script-based vulnerability attack graph generation, to achieve the effect of easy intelligent processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention is further described as follows in conjunction with accompanying drawings and embodiments.
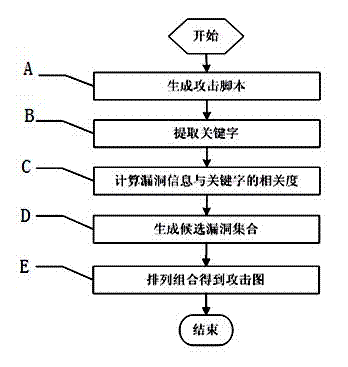
[0039] like figure 1 Shown is an embodiment of a method for generating a script-based vulnerability attack graph, comprising the following steps:
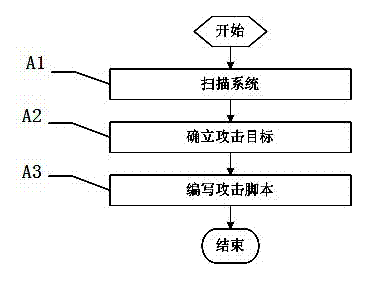
[0040] A. Generate attack script: propose an attack script describing the attack path, and the generation process of the attack map starts from the step A to generate the vulnerability attack script;
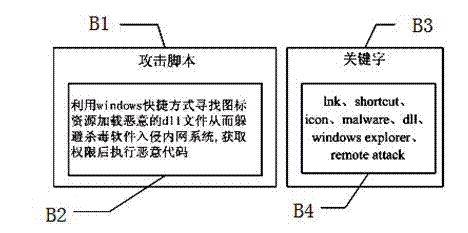
[0041] B. Extract keywords: extract a certain number of keywords according to the attack script; this keyword can indeed identify the content of the attack script, and has the ability to distinguish the attack script from other texts. The number should not be too many, but the content of the keywords It can be far richer than several keywords in traditional queries;
[0042] C. Calculate the correlation between vulnerability information and keywords: calculate the vulnerability database The TF-IDF weight betwe...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap