Method and device for identifying risk users
An identification method and user technology, applied in the field of data processing, can solve problems such as bad behavior hazards and user hazards, and achieve the effect of flexible detection methods and reduced hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the above objects, features and advantages of the present application more obvious and understandable, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
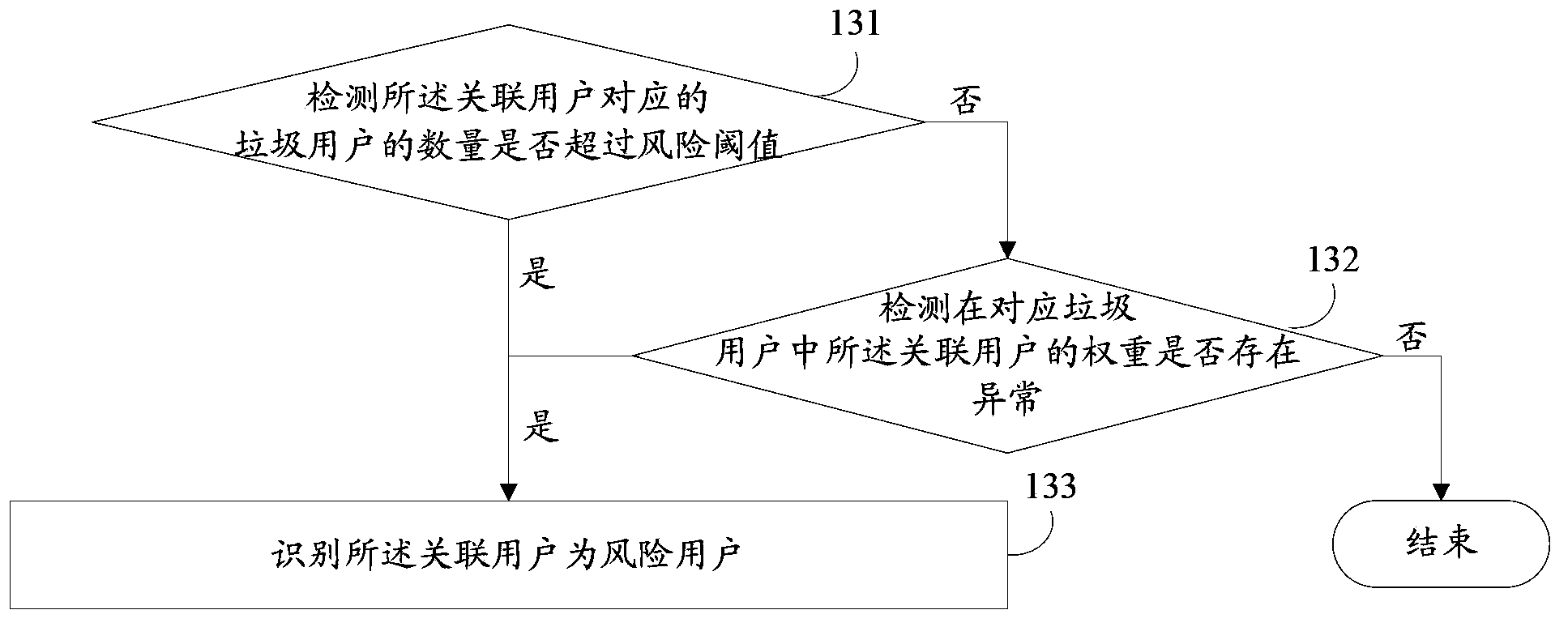
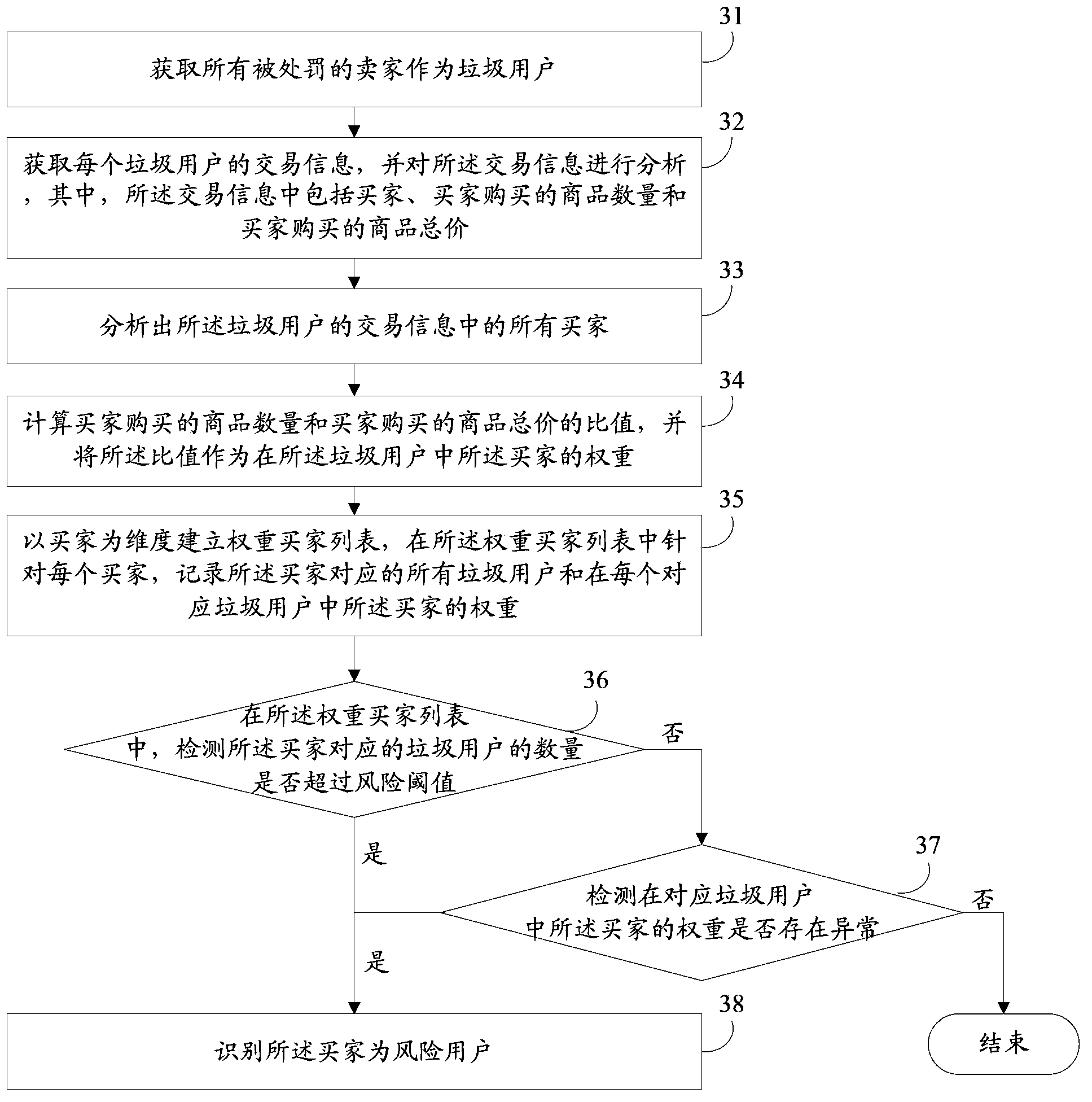
[0039] In the prior art, it is only possible to punish spam users who perform these bad behaviors, but it is impossible to identify users who intentionally spread spam information related to bad behaviors.
[0040] The present application provides a method for identifying risky users, which can identify associated users who intentionally spread spam information related to bad behavior, so that risky users can be identified. Furthermore, the identified risk users can be monitored, and the operation authority of the risk users can be restricted, thereby further reducing the harm caused by bad behaviors.
[0041] The method described in this application will be described in detail below through examples.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com