An identifier mapping method and apparatus and a policy control method
A mapping method and mapping relationship technology, applied in the field of communication, can solve the problem of inability to fix device policy control, and achieve the effect of policy control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
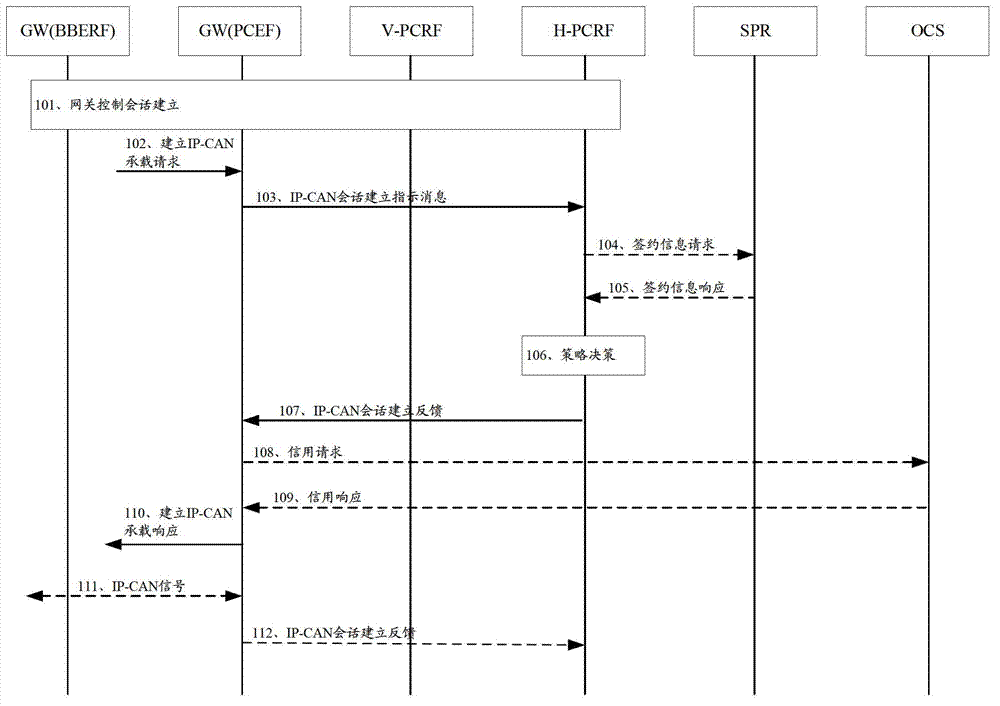
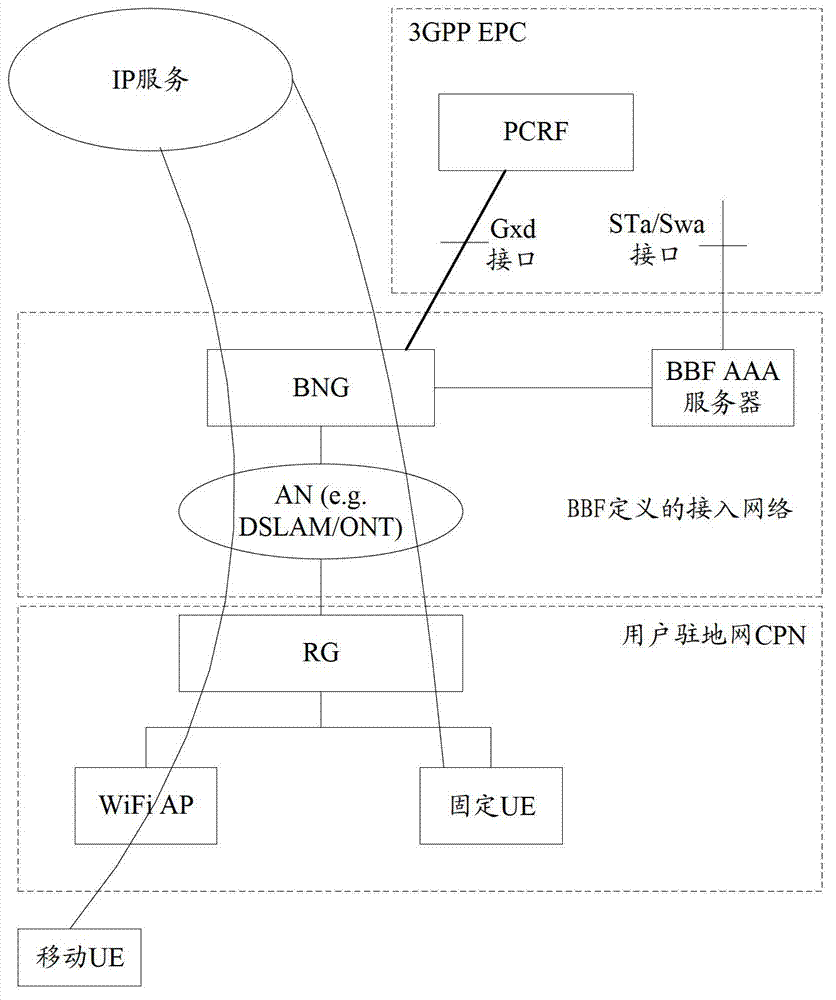
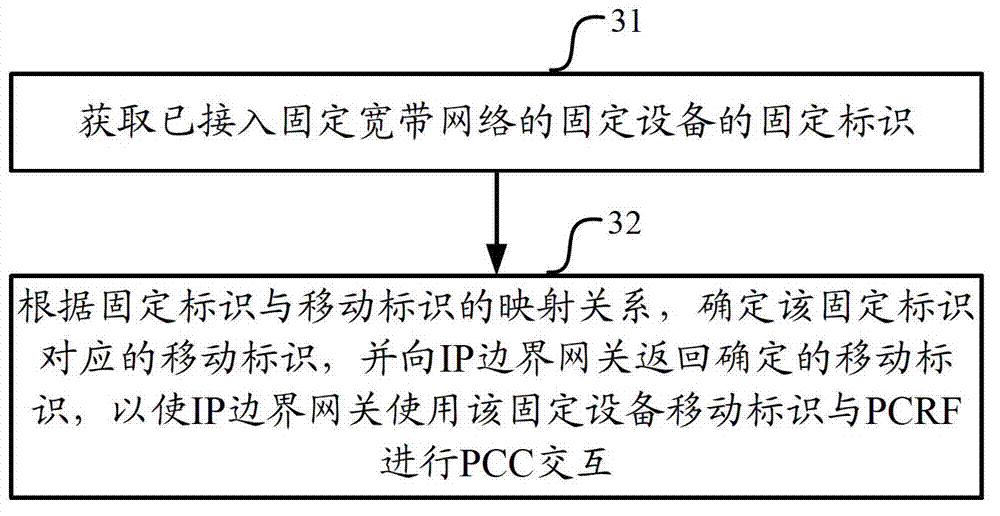
[0099] Embodiment 1. The mapping relationship between the fixed ID and the mobile ID is stored on the BBF AAA server, that is, the BBF AAA server realizes the ID mapping of the fixed device;
[0100] Specifically, after the fixed device accesses the fixed broadband network, the authentication process will be triggered. The authentication process involves the interaction between the fixed device, the IP border gateway and the BBF AAA server. The fixed device sends an authentication request to the IP border gateway, During the authentication process, the IP border gateway, as an access node, does not process the authentication request, but directly sends the authentication request to the BBF AAA server. Since the BBF AAA server has the function of identity mapping, it receives the IP After the authentication request sent by the border gateway, query the mobile identity corresponding to the fixed identity carried in the authentication request from the saved mapping relationship, a...
Embodiment 2
[0107] Embodiment 2. The mapping relationship between the fixed identifier and the mobile identifier is stored on the 3GPPAAA server, that is, the 3GPPAAA server realizes the identifier mapping of the fixed device;
[0108] Specifically, after the fixed device accesses the fixed broadband network, the authentication process will be triggered. The authentication process involves the interaction between the fixed device, the IP border gateway and the BBF AAA server. The fixed device sends an authentication request to the IP border gateway, During the authentication process, the IP border gateway, as an access node, does not process the authentication request, but directly sends the authentication request to the BBF AAA server. Since the 3GPP AAA server has the function of identity mapping, the BBF AAA server After receiving the authentication request sent by the IP border gateway, send an identification request to the 3GPP AAA server, wherein the identification request carries a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com