A working method of a safety keyboard
A working method, technology of a secure keyboard, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
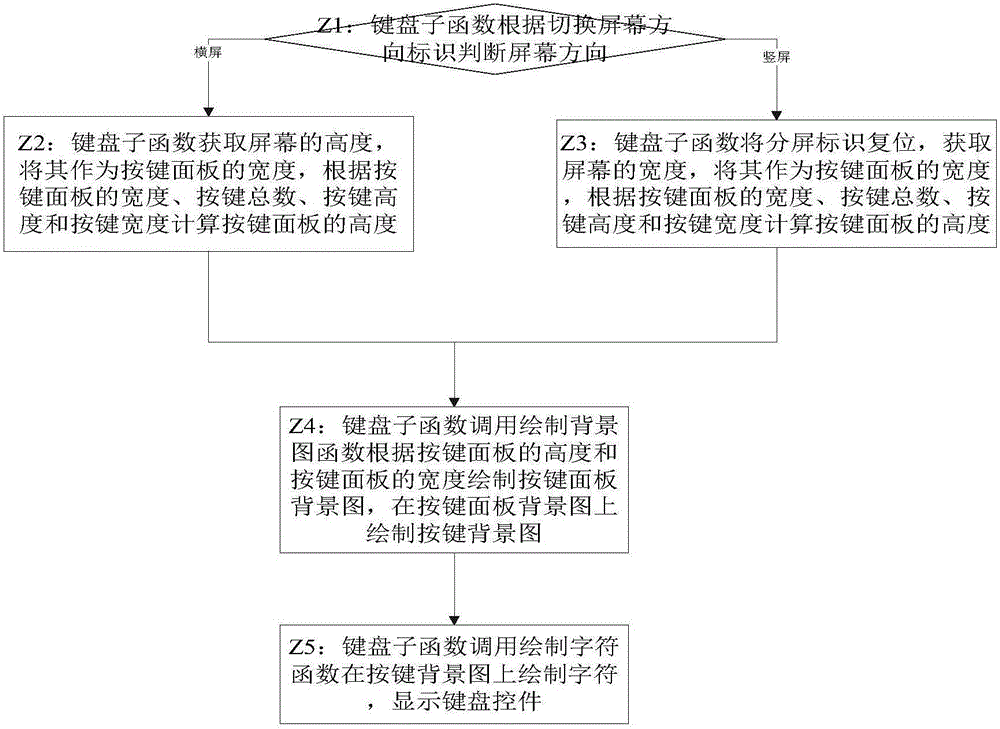
[0069] The technical solution provided by the embodiment of the present invention is applied to the Android system, and involves keyboard control, password box control, keyboard touch screen event processing function, password box touch screen event processing function, switching screen direction event processing function, keyboard sub-function and JNI Encryption function and decryption function defined in (Java Native Interface, Java native call).
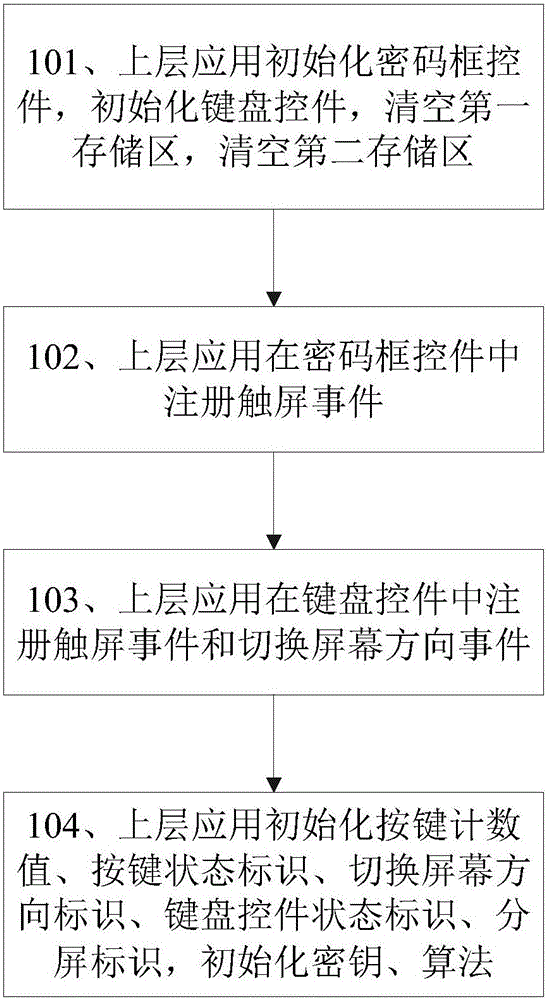
[0070] Such as Picture 1-1 As shown, the upper layer application performs the following operations, including:
[0071] Step 101, the upper layer application initializes the password box control, initializes the keyboard control, clears the first storage area, and clears the second storage area;
[0072] Step 102, the upper layer application registers the touch screen event in the password box control;
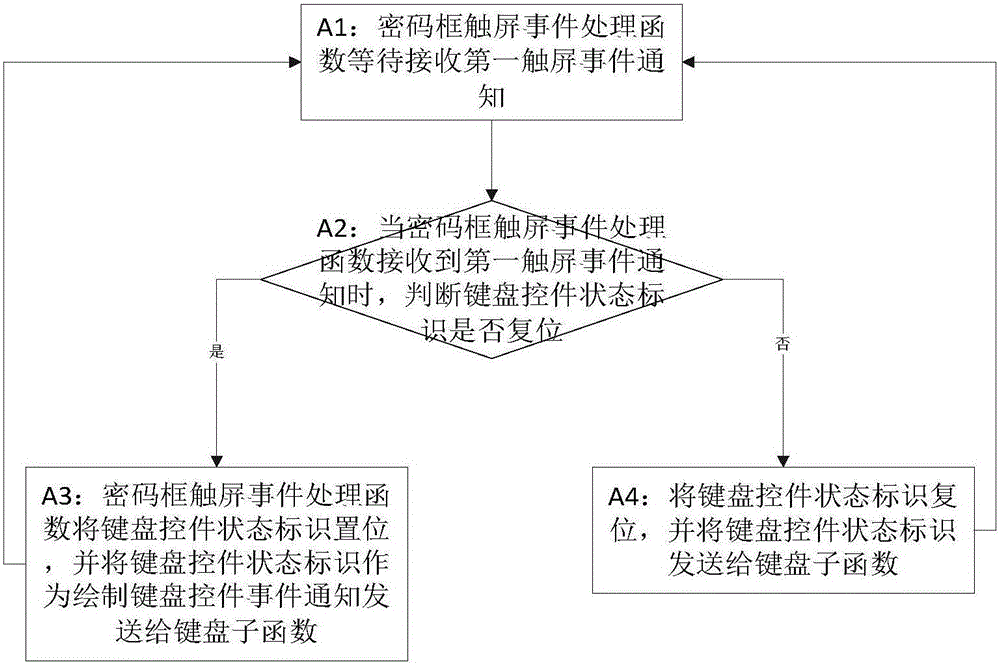
[0073] In this embodiment, a touch screen event is registered in the password box control, and when a touch screen event occur...
Embodiment 2
[0185] An embodiment of the present invention provides a working method of a security keyboard, including:
[0186] The upper application initializes the password box control, initializes the keyboard control, clears the first storage area and the second storage area, registers touch screen events in the password box control, registers touch screen events and switching screen direction events in the keyboard control, and initializes the key count value , key state identification, switch screen direction identification, keyboard control status identification, split screen identification, initialization key, algorithm.
[0187] In this embodiment, the touch screen event is registered in the password box control. When a touch screen event occurs in the password box control, the password box control sends the first touch screen event notification to the password box touch screen event processing function by broadcasting; The touch screen event is registered in the control. When a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com