A Spatial Anonymization Method Applicable to Mobile Location Privacy Protection
A privacy protection and mobile terminal technology, applied in the field of network security, can solve problems such as increasing interference value, achieve the effect of increasing computing speed and reducing communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
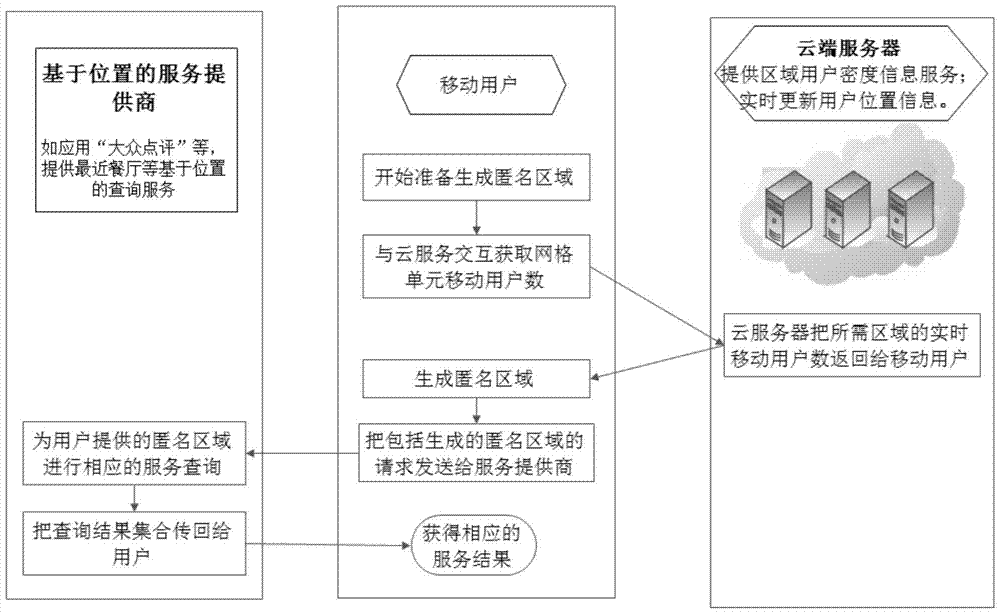
[0076] The invention specifically demonstrates the method for realizing the initial recursive area of the improved spatial anonymity algorithm.
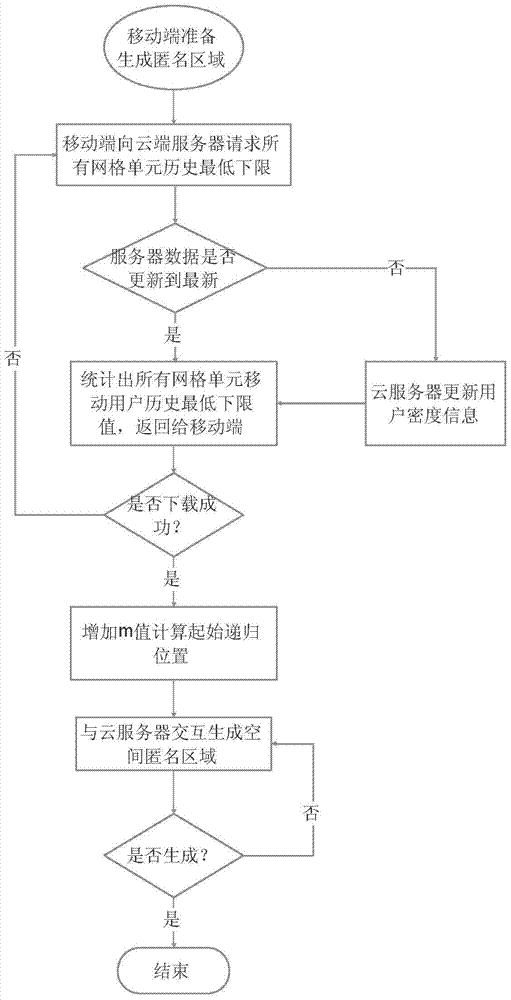
[0077] First, using the historical statistical data of mobile users in each grid unit provided by cloud services, the historical minimum number of mobile users in each grid unit can be obtained, that is, the historical lower limit of the number of mobile users, denoted as c LB , and then download these historical lower limit values to the mobile terminal at one time, so that it can be operated locally, avoiding the communication overhead caused by interacting with the cloud server for each recursion from top to bottom. Of course, this process will have a certain initialization cost. And because the historical data of each grid unit is already on the user's mobile terminal, the initialization area can be calculated directly on the mobile terminal, and there is no need to interact with the cloud to obtain data. This process is oper...
Embodiment 2
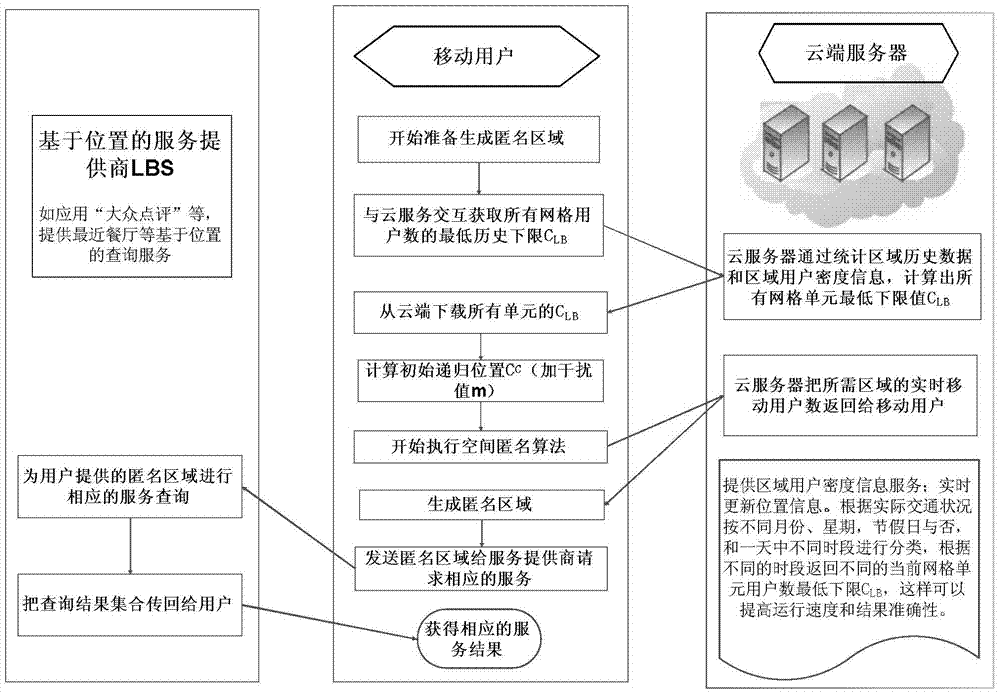
[0099] The present invention increases the interference value m to deal with privacy threats.
[0100] The previous section analyzed how to determine the initial recursive area of the improved spatial anonymity algorithm, but the anonymous area R calculated based on historical data LB grid cell c LB As the initial grid unit, there is actually a risk of privacy leakage. because when c LB When >=k, the grid unit c is not necessarily guaranteed LB The number of real-time users is not less than k. At this time, the number of users in the grid unit may be the lowest point in history and less than k, then the improved top-down anonymous algorithm will return c LB , at this time, if the number of mobile users in the anonymous area is less than k, then k-anonymity will be invalidated, and the location of the requesting user will be exposed. Therefore, in order to better balance the three elements of speed, communication cost and location privacy protection, we have made further ...
Embodiment 3
[0128] This patent uses time segmentation to replace the initial static one-time update.
[0129] based on c LB Casper anonymous algorithm, we calculate the lower limit of the historical minimum number of mobile users based on all historical data, however, mobile phone users are mobile, and the actual traffic conditions will vary with time periods The density of mobile users in time periods will also vary greatly. If the historical lower limit is calculated based on all historical data each time, although it can be guaranteed to be the lowest value, it will also affect the calculation speed and accuracy to a certain extent. For example, when it is rush hour, the density of mobile users on the road is relatively high. At this time, if the historical lower limit of all time periods is used to calculate the historical anonymous area as the initial area of the actual anonymous area, then the historical anonymous area will be much larger than the actual demand area, because the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com