Border control method, access controller and system
An access controller and border control technology, applied in the network field, can solve problems such as illegal access to the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
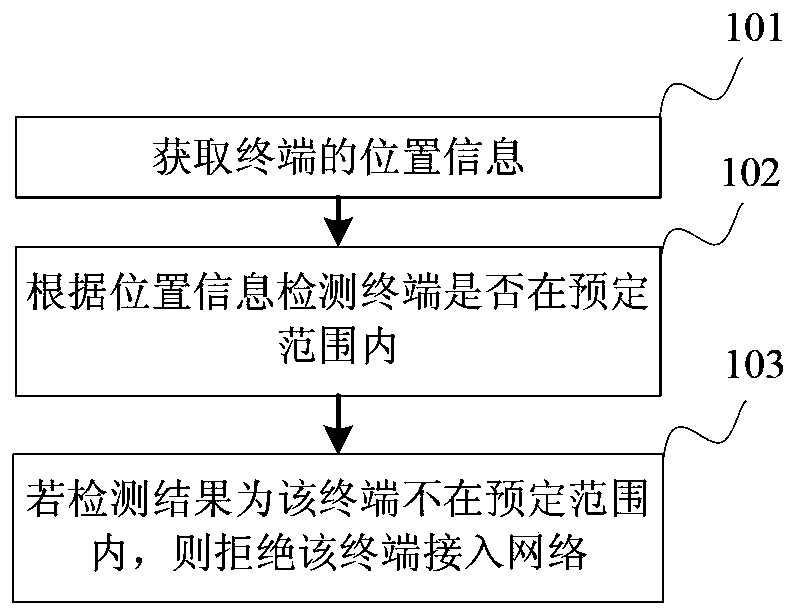
[0072] Please refer to image 3 , which shows a method flowchart of the border control method provided in Embodiment 1 of the present invention. Embodiments of the present invention are described by taking the border control method applied to an access controller in a network system as an example. The border control methods include:
[0073] Step 101, acquiring the location information of the terminal;
[0074] The access controller acquires the location information of the terminal, and the location information is used to determine the location of the terminal.
[0075] Step 102, detecting whether the terminal is within a predetermined range according to the location information;
[0076] The access controller detects whether the terminal is within a predetermined range according to the location information, and the predetermined range is a range allowed to access the network.
[0077] Step 103, if the detection result is that the terminal is not within the predetermined r...
Embodiment 2
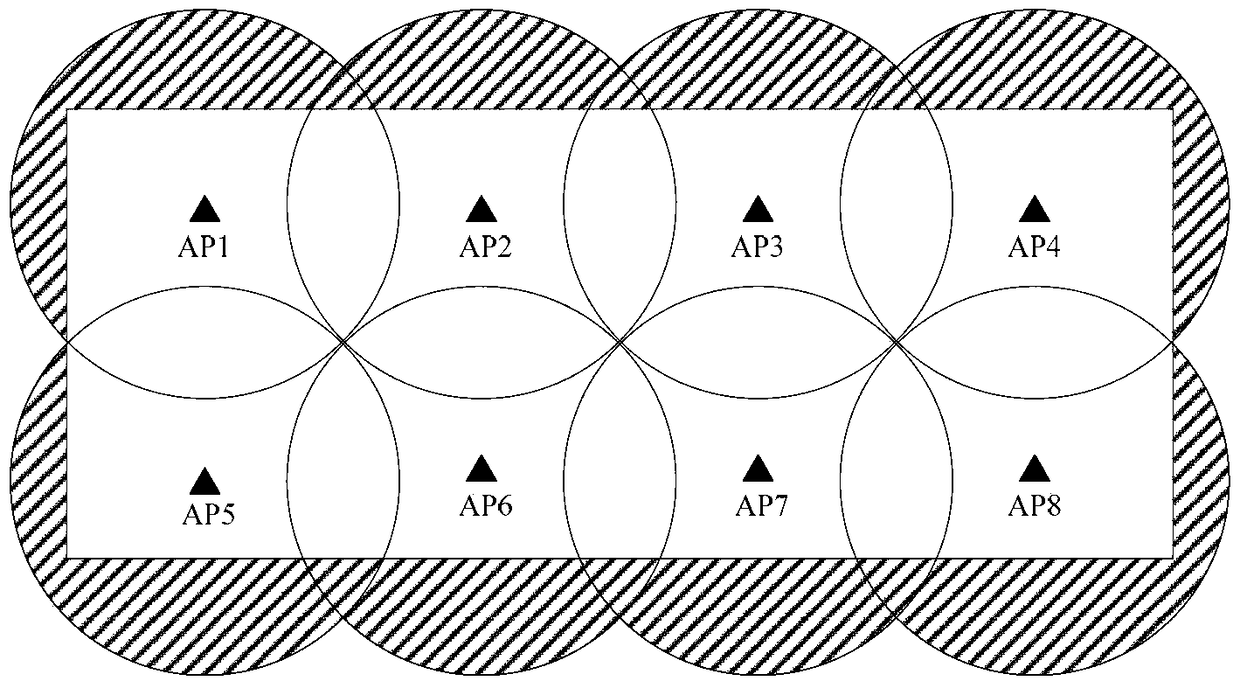
[0081] Please refer to Figure 4 , which shows the flow chart of the boundary control method provided by the second embodiment of the present invention, which is applied to the boundary control method in the embodiment of the present invention Figure 5 The application scenario shown is taken as an example for description. refer to Figure 5 It can be seen that, assuming that an enterprise uses AP1 to AP8 to cover the internal area of the enterprise with wireless signals, the internal area of the enterprise is the range shown in the box 501, and the external area of the enterprise is the shaded part. For the convenience of description, it should be noted that Figure 5 The midline segment MC is perpendicular to the connection line between AP1 and AP2, the line segment ND is also perpendicular to the connection line between AP1 and AP2, and the line segment EF is the distance between the connection line between AP1 and AP2 and one side of the rectangle. The border cont...
Embodiment 3
[0108] Please refer to Figure 8 , which shows a structural block diagram of the access controller provided in Embodiment 3 of the present invention, the access controller belongs to a border control system, and the border control system also includes a wired network or a wireless network with the access controller At least two APs connected, the access controller includes:
[0109] An acquisition module 810 , a detection module 820 and a rejection module 830 .
[0110] The obtaining module 810 is configured to obtain location information of the terminal, and the location information is used to determine the location of the terminal;
[0111] The detecting module 820 is configured to detect whether the terminal is within a predetermined range according to the location information obtained by the obtaining module 810, and the predetermined range is a range allowed to access the network;
[0112] The rejecting module 830 is configured to reject the terminal from accessing the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com