Method and device for controlling access of user equipment
A technology of user equipment and equipment, applied in the field of communication, can solve problems such as the inability to control UE access to the network, and achieve the effect of reducing national information security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
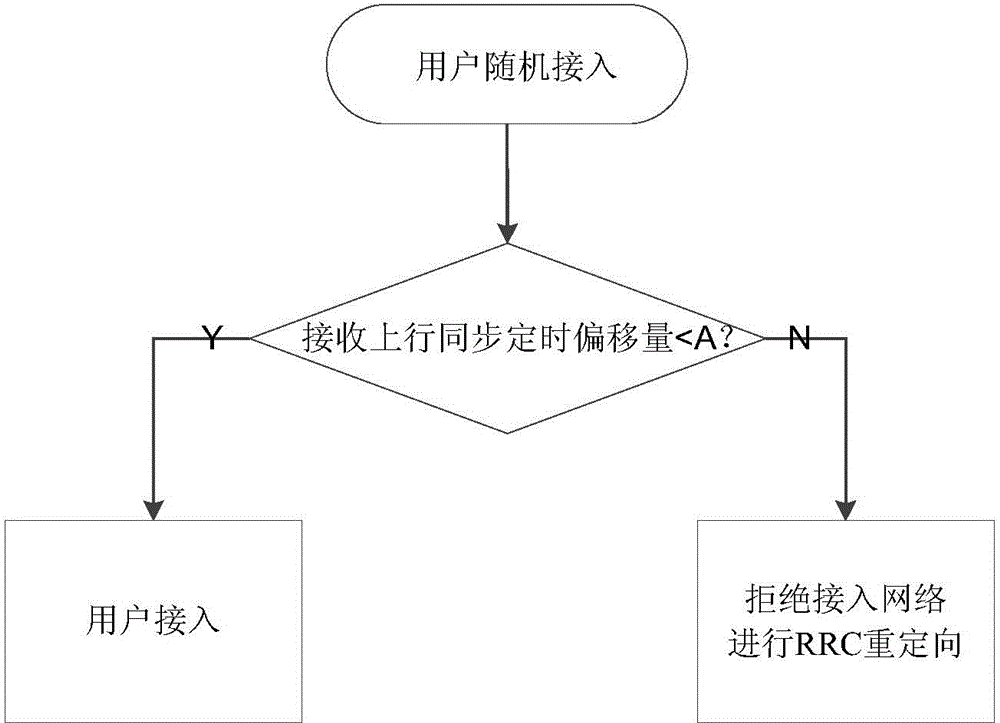
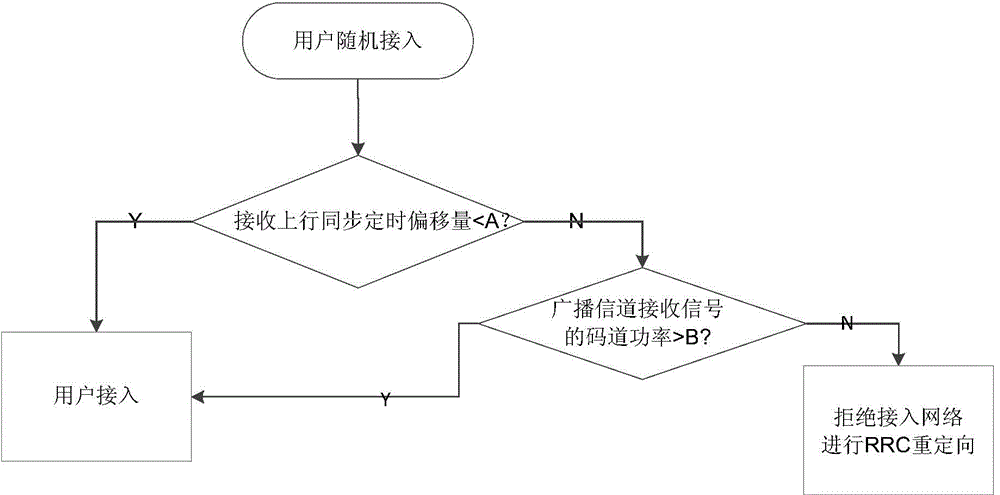
[0047] Embodiments of the present invention provide a method and device for controlling user equipment access, which are used to control whether all UEs can access the network, thereby reducing the illegal access network caused by UEs that do not report TA. national information security risks.
[0048] In the embodiment of the present invention, by comparing the receiving uplink synchronization timing offset reported by the base station with the preset synchronization timing offset threshold value, it is determined whether the UE is connected to the network, thereby realizing the monitoring of whether all UEs can access the network Control, which solves the problem of illegal access to the network abroad for UEs that do not report TA, and determines whether the UE is allowed to access the network before service access, thereby avoiding the release of the illegal access UE after access and business , reducing the hidden dangers of national information security caused by UE's il...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com