Anti-counterfeiting label and anti-counterfeiting method based on combination of two-dimensional code and RFID chip
A technology of RFID label and two-dimensional code label, applied in the carrier field of RFID electronic label, can solve the problems of being easily counterfeited, unable to track and trace items, and inconvenient for anti-counterfeiting verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
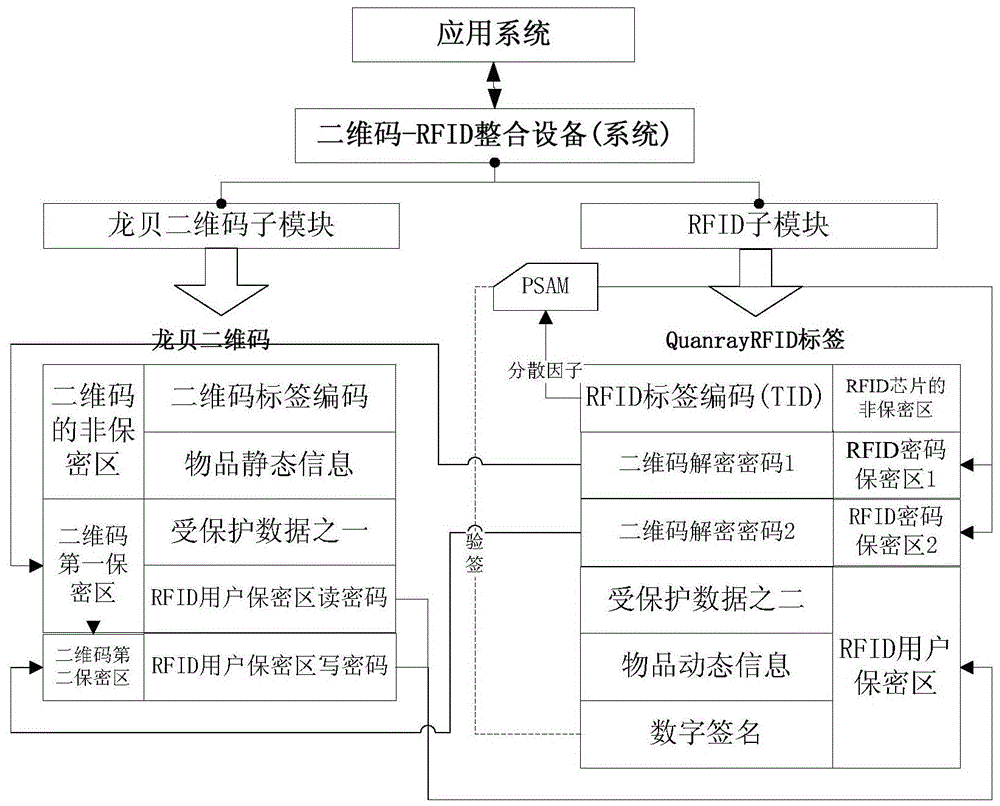
[0115] Such as figure 1 What is shown is a preferred embodiment of the present invention, which will be explained emphatically now.
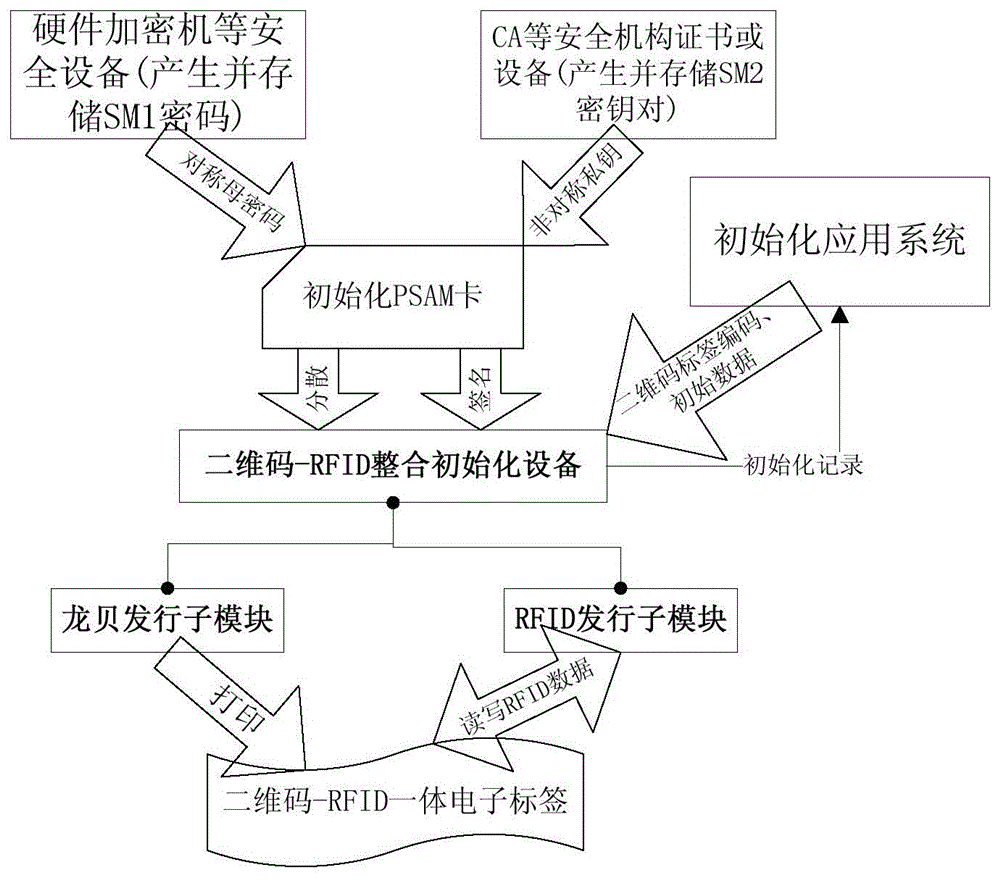
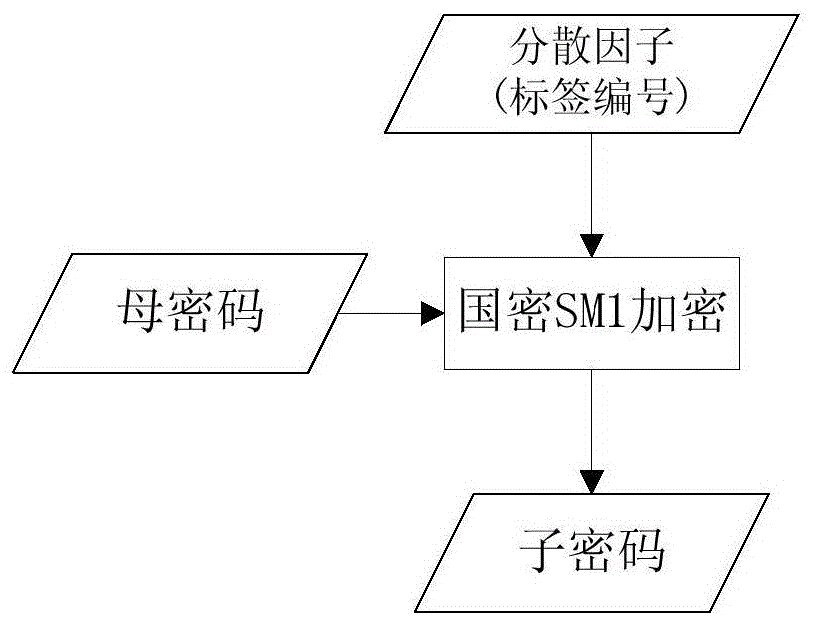
[0116] refer to figure 2 As shown, the anti-counterfeiting label needs to be initialized, and the password and initial data are printed into a two-dimensional code and written into the RFID chip. For an anti-counterfeiting system, the protection password must first be generated. Compared with a single application label, the generated password is the parent password. The parent password is not directly written into the label, but the unique dispersion factor for a single label must first be changed through a decentralized algorithm. into a unique sub-password. The generation of the master password can be realized by a hardware encryption machine supporting the SM1 algorithm. Once generated, the system will continue to use this master password until the system password version is upgraded. After the encryption machine generates the password, t...
example 2
[0149] Such as Figure 6 As shown, it is a modification of Example 1. The authorized PSAM card stores the password of the two-dimensional code security area. After unlocking the password of the two-dimensional code security area, read the password of the RFID user security area to unlock the RFID User confidential area, read the digital signature in it for signature verification.
example 3
[0151] Such as Figure 7 As shown, for the simplification of Example 1, the authorized PSAM card can directly unlock the RFID password security area and the RFID user security area, read the password of the QR code in the RFID password security area to access the QR code, and read the password of the RFID user security area. Digital signature for verification.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com