Malware searching and killing method and device
A malicious program, killing technology, applied in the computer field, can solve problems such as not fundamentally cleared, user troubles, and ROM virus with high authority
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0094] The embodiment of the present invention provides a method for checking and killing malicious programs. The method can thoroughly remove some stubborn malicious programs by reflashing the mobile terminal, and it can be implemented on the PC through antivirus software, first aid systems of the antivirus software, and the like.
[0095] Wherein, in some ways of checking and killing (such as a first aid kit), the malicious program can be selected to be immune-processed, but this method can only eliminate the malicious behavior of the malicious program, but does not remove the malicious program from the system, and the present invention The method provided by the embodiment can eliminate this stubborn malicious program.
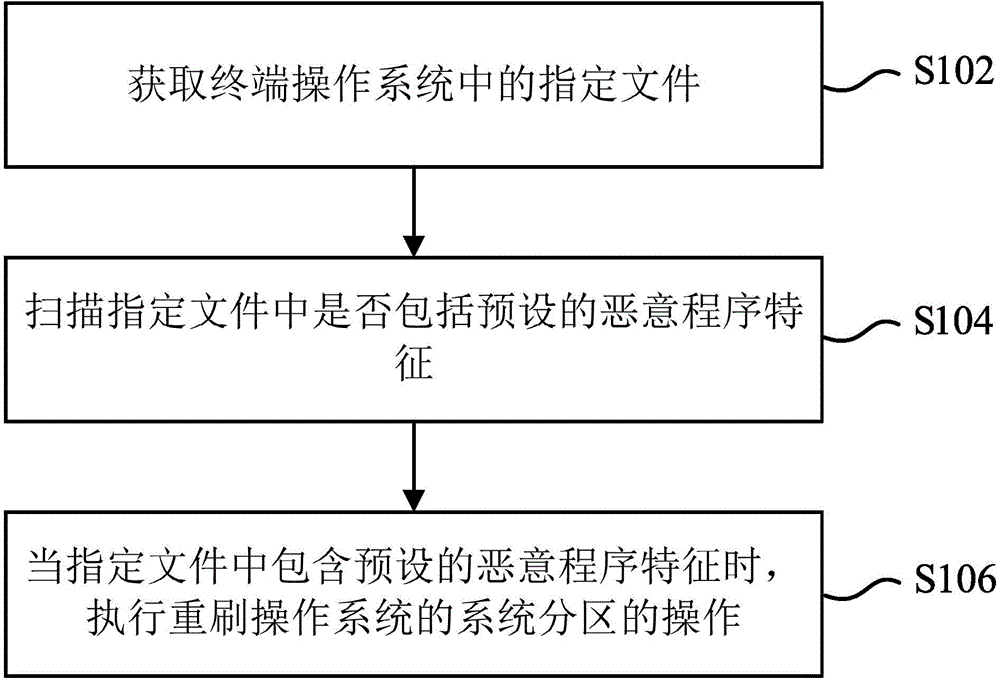
[0096] figure 1 It is a flow chart of a method for checking and killing malicious programs provided by an embodiment of the present invention, and the method includes steps S102 to S106.
[0097] S102. Obtain a specified file in the terminal operating sys...
Embodiment 2
[0103] This embodiment is a specific application scenario of the first embodiment above. Through this embodiment, the method provided by the present invention can be described more clearly and specifically. In this embodiment, the malicious program in the mobile terminal is checked and killed by a toolbox installed in the PC (for example, it can be a first-aid kit, and after the mobile terminal accesses the PC, the first-aid kit automatically starts a corresponding killing program). Take this as an example.
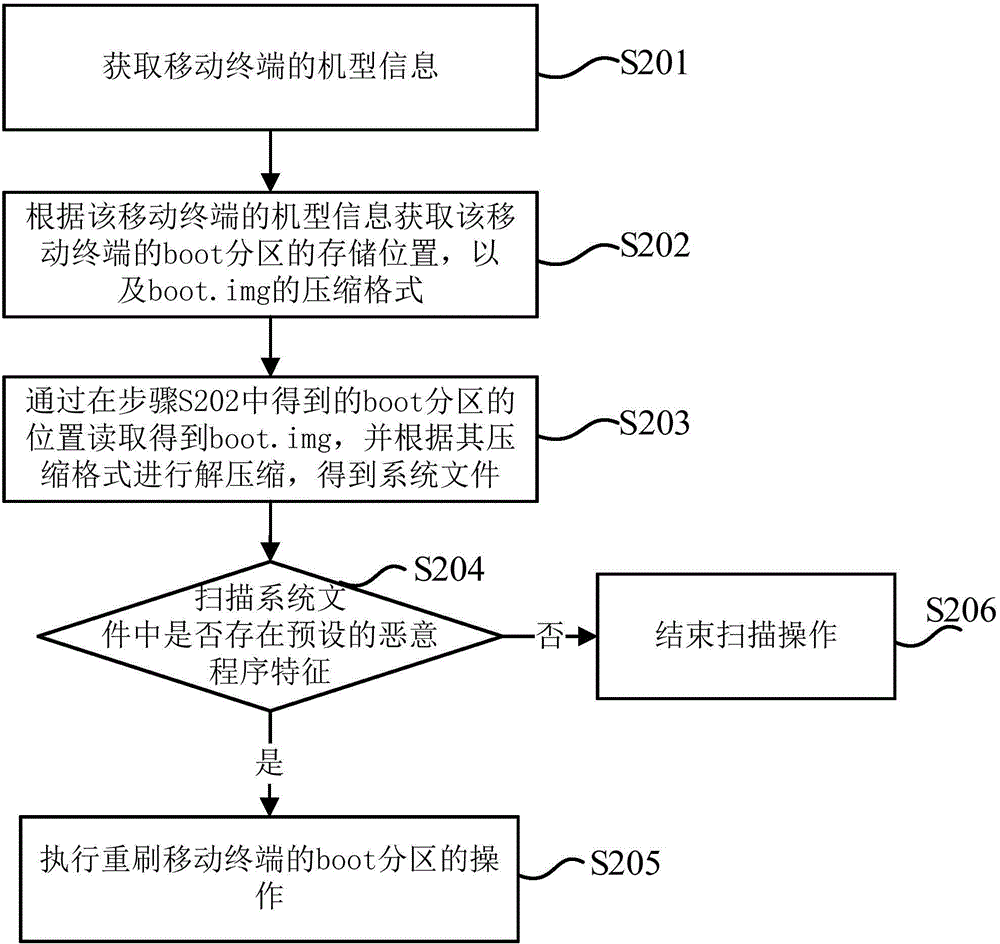
[0104] figure 2 It is a flow chart of a specific method for checking and killing malicious programs provided by an embodiment of the present invention, and the method includes steps S201 to S206.
[0105] It should be noted that since the method provided in this embodiment needs to complete the removal of malicious programs by re-flashing the mobile terminal, it is necessary to connect the mobile terminal to a PC and execute the flow of the method.
[0106] Taking Andr...
Embodiment 3
[0236] Figure 7 It is a structural block diagram of a device for checking and killing malicious programs provided by an embodiment of the present invention. The device 700 includes:
[0237] A file obtaining module 710, adapted to obtain a specified file in the terminal operating system;
[0238] A program scanning module 720, adapted to scan whether the specified file includes preset malicious program features;
[0239] The operation execution module 730 is adapted to execute the operation of reflashing the system partition of the operating system when the specified file contains preset malicious program features;
[0240] Wherein, the specified file is stored in the system partition.
[0241] Optionally, the system partition is a BOOT partition, and the designated file is a system file compressed package stored in the BOOT partition.
[0242] Optionally, the file obtaining module 710 is adapted to obtain a specified file in the terminal operating system in the following...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com