Mobile phone alarm method and device
A mobile phone and receiver technology, applied in the field of alarm, can solve the problems of the alarm person's exposure to the alarm, the alarm person or the victim's danger, etc., and achieve the effect of continuous and smooth communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
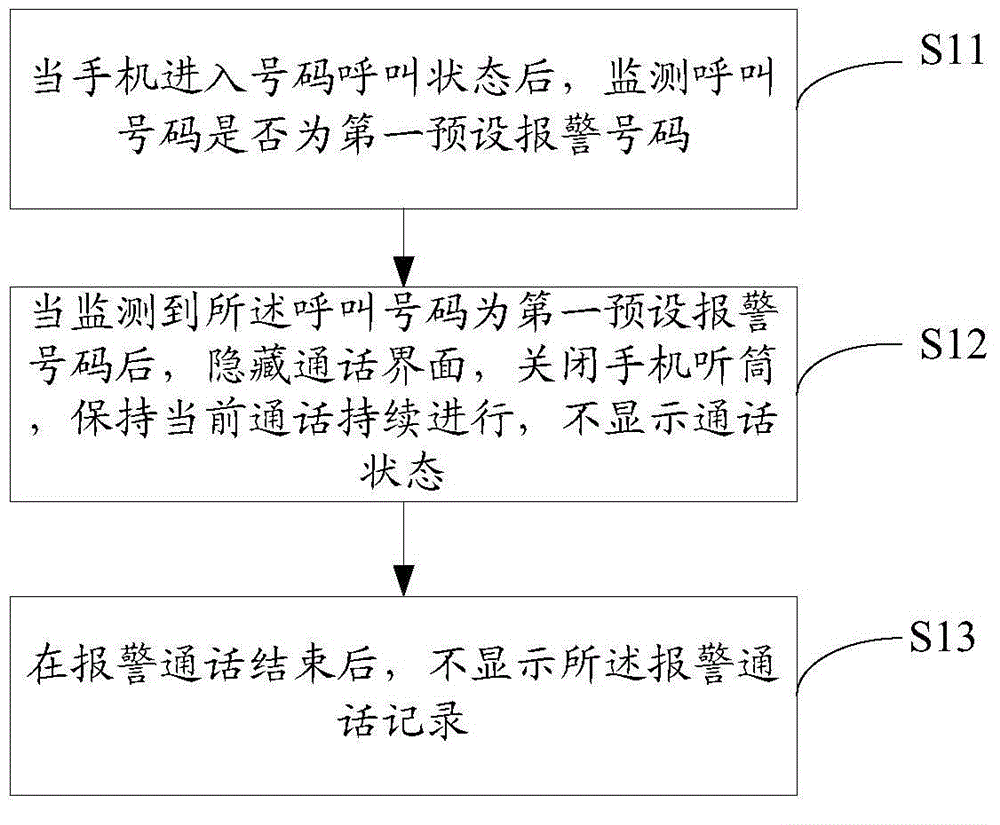
[0051] figure 1 It is a schematic flowchart of the mobile phone alarm method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the mobile phone alarm method comprises the following steps:
[0052] S11. When the mobile phone enters the number calling state, monitor whether the calling number is the first preset alarm number:
[0053] The user enters the calling number on the dialing interface of the mobile phone, clicks the dial key, and the mobile phone enters the number calling state.
[0054] At this time, the mobile phone monitors whether the calling number being connected is the first preset alarm number, if yes, execute step S12, and if not, make a call according to the normal call mode of the mobile phone.
[0055] It should be noted that the preset alarm number may be an alarm number defined by the mobile phone system, such as "110". In addition, the preset alarm numbers can also be some alarm numbers customized by mobile phone users. Fo...
Embodiment 2
[0066] The mobile phone alarm method described in Embodiment 2 has many similarities with the mobile phone alarm method described in Embodiment 1. For the sake of brevity and to highlight the differences from Embodiment 1, this embodiment of the present invention only focuses on the differences For the similarities, please refer to the description of Embodiment 1.
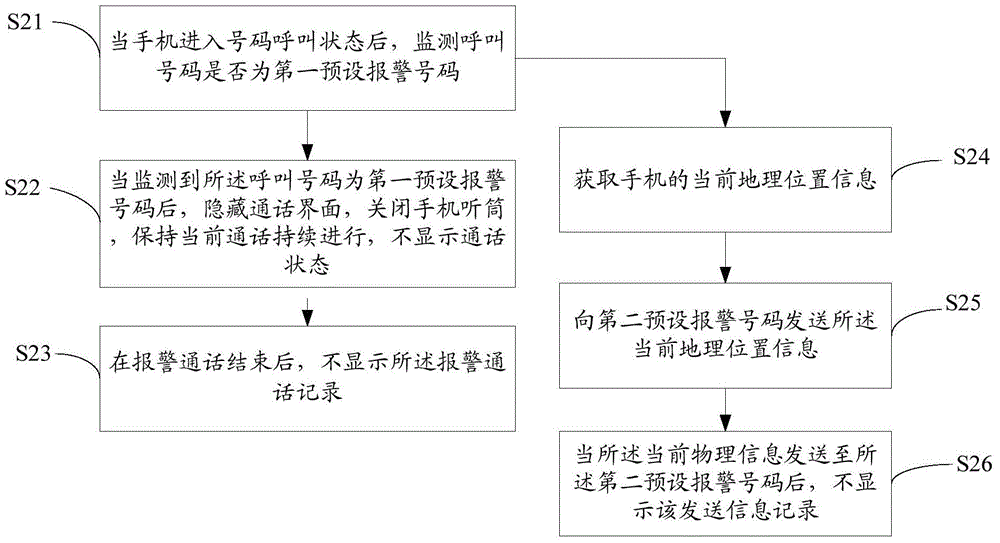
[0067] figure 2 It is a schematic flowchart of the mobile phone alarm method provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the mobile phone alarm method comprises the following steps:
[0068] Step S21 to step S23 are the same as step S11 to step S13 in the first embodiment, and for the sake of brevity, no detailed description is given here. For details, refer to the corresponding description of the first embodiment.
[0069] Different from Embodiment 1, the mobile phone alarm method provided in Embodiment 2 of the present invention may further include the following steps when t...
Embodiment 3
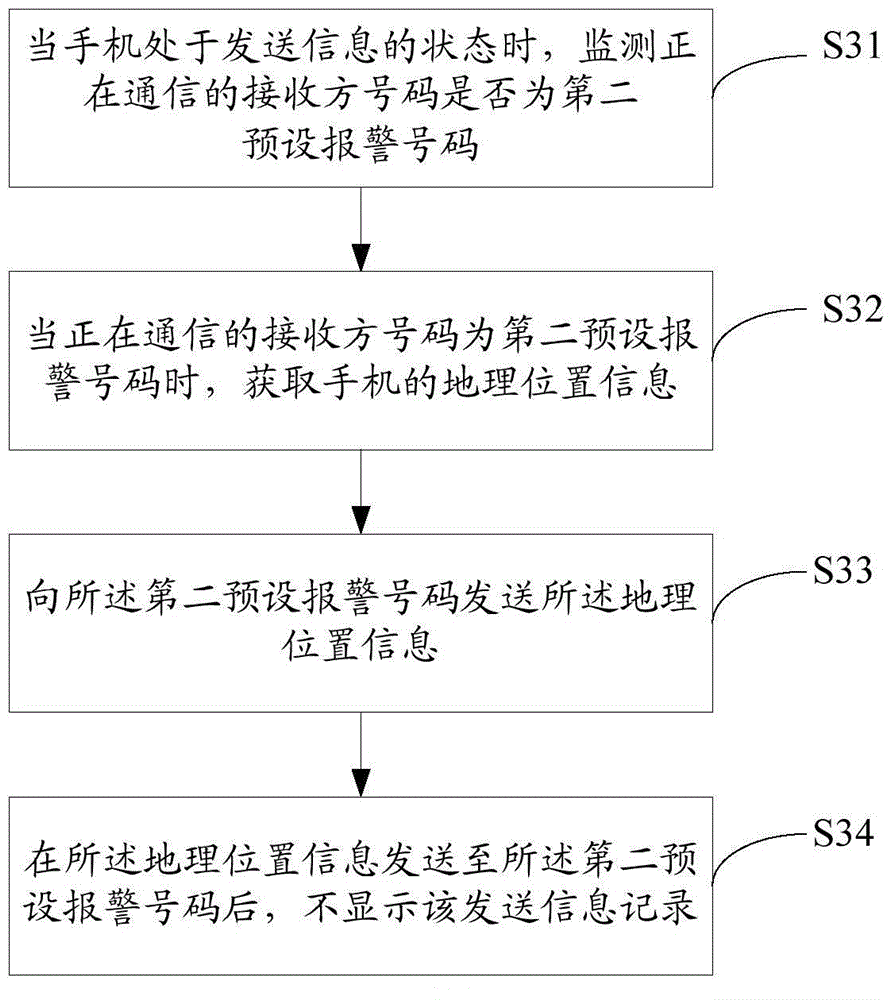
[0085] image 3 It is a schematic flowchart of the mobile phone alarm method provided by Embodiment 3 of the present invention. Such as image 3 As shown, the mobile phone alarm method comprises the following steps:
[0086] S31. When the mobile phone is in the state of sending information, monitor whether the number of the receiving party in communication is the second preset alarm number:
[0087] S32. When the communicating receiver's number is the second preset alarm number, obtain the geographic location information of the mobile phone:
[0088] When the communicating receiver number is the second preset alarm number, the GPS function module of the mobile phone is turned on to obtain the current geographic location information of the mobile phone.
[0089] S33. Send the geographic location information to the second preset alarm number.
[0090] S34. After the geographic location information is sent to the second preset alarm number, the sending information record is n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com