Method for terminal authority management and terminal
A rights management and terminal technology, applied in electronic digital data processing, instruments, digital data authentication, etc., can solve the problems of sensitive data leakage, privacy theft, relying on manual judgment, etc., to protect data security and reduce malicious application misauthorization Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
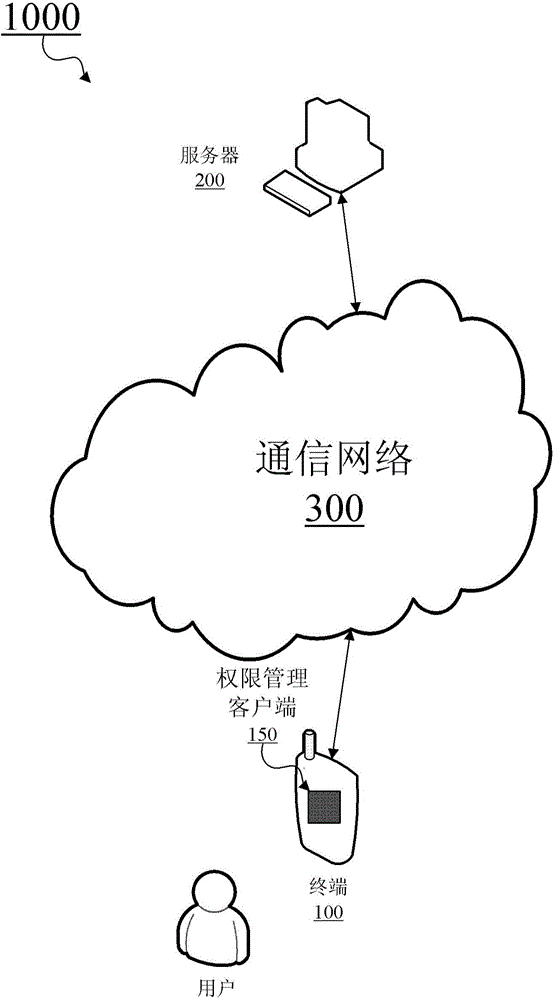
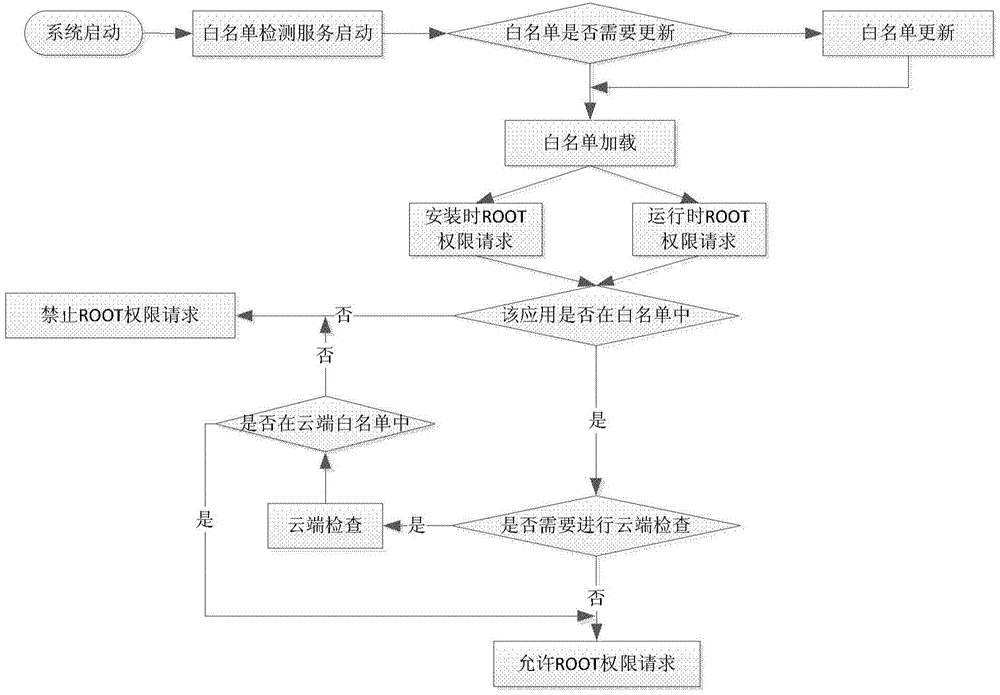
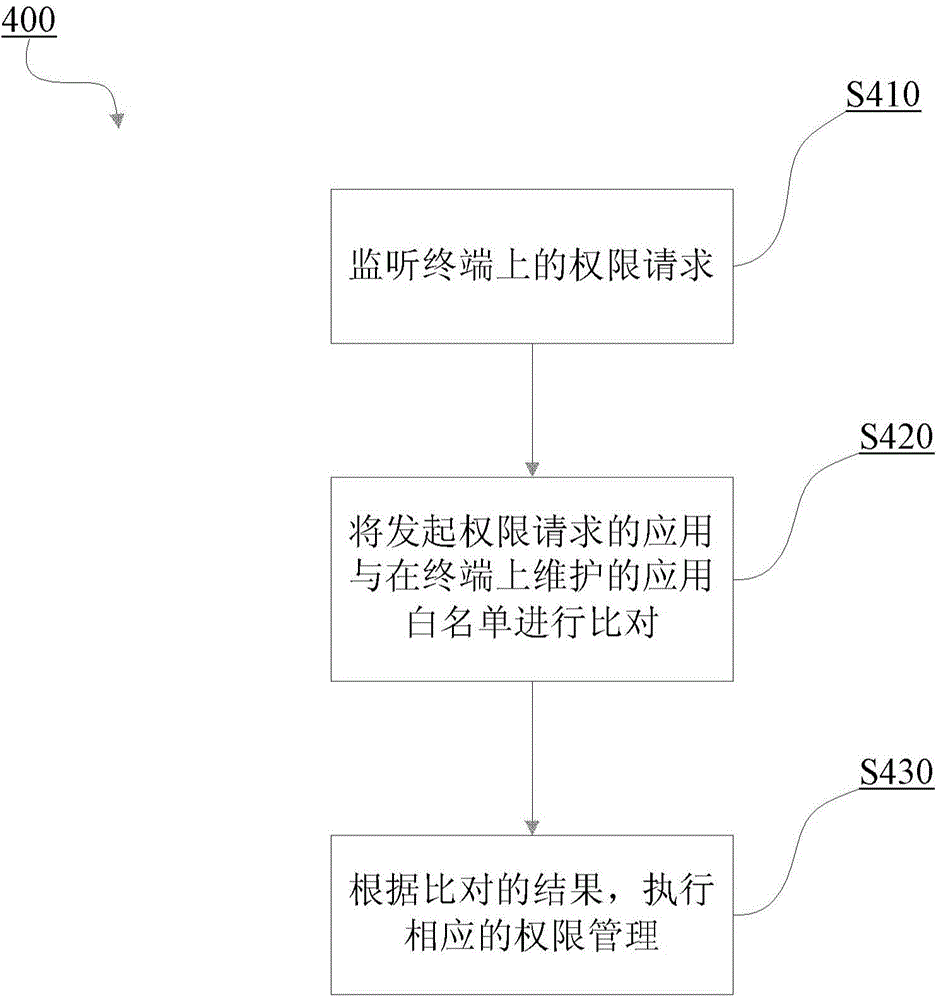
[0037] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings, and unnecessary details and functions for the present invention will be omitted during the description to avoid confusing the understanding of the present invention. Hereinafter, the present invention is described in detail by taking the scenario where the present invention is applied to a wireless mobile communication system as an example. But the present invention is not limited thereto, and the present invention can also be applied to a fixed communication system, a wired communication system, or any hybrid structure of a wireless mobile communication system, a fixed communication system, a wired communication system, and the like. As far as the mobile communication system is concerned, the present invention is not limited to the specific communication protocols of the various mobile communication terminals involved, and may include (but no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com