A security audit method and system for mobile Internet
A mobile Internet and security audit technology, applied in the field of mobile Internet-oriented security audit, can solve the problems of lack of analysis and supervision means, weak data audit links, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to make the technical problems, technical solutions and technical effects to be solved by a mobile Internet-oriented security audit method and system of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
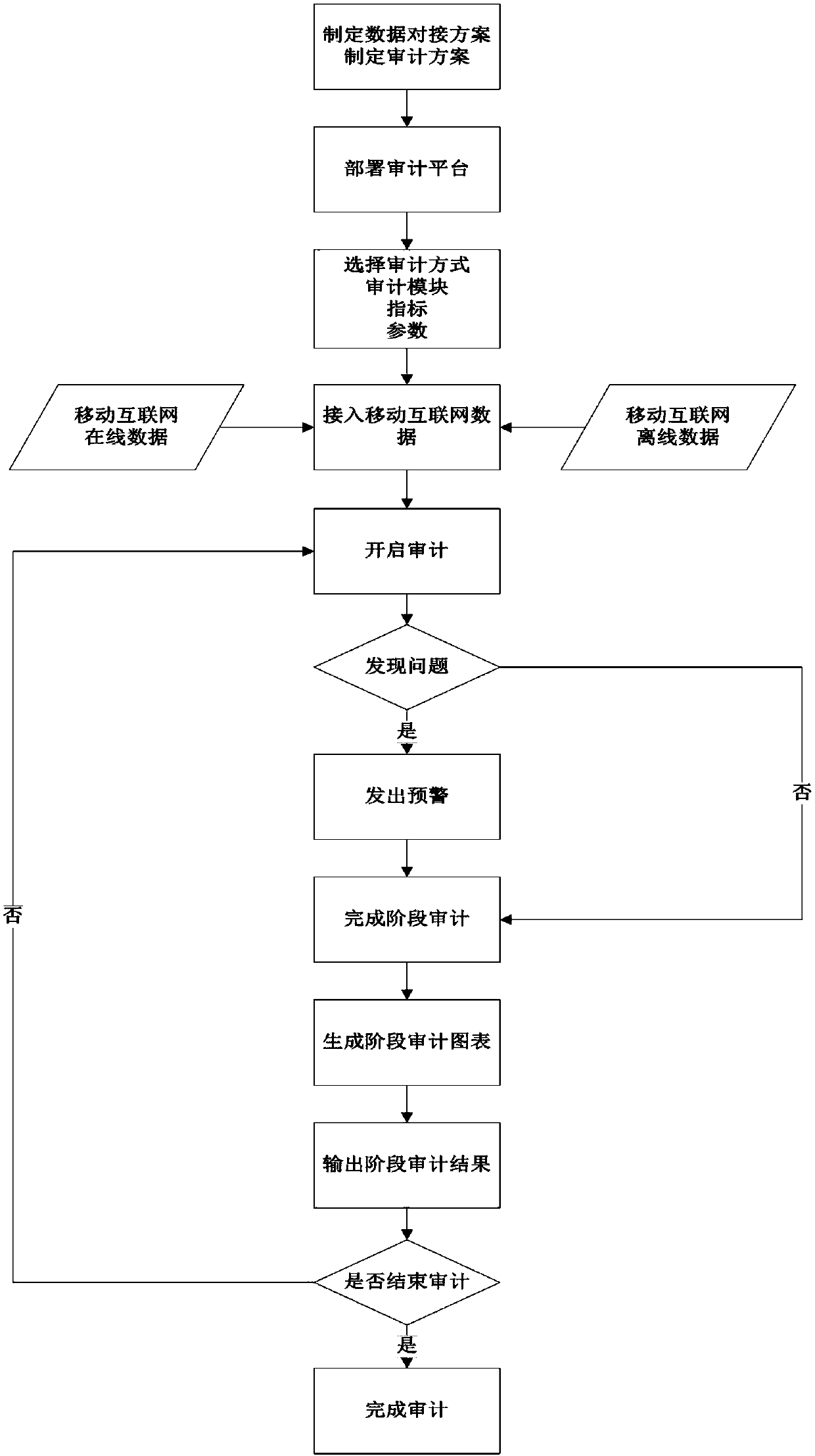
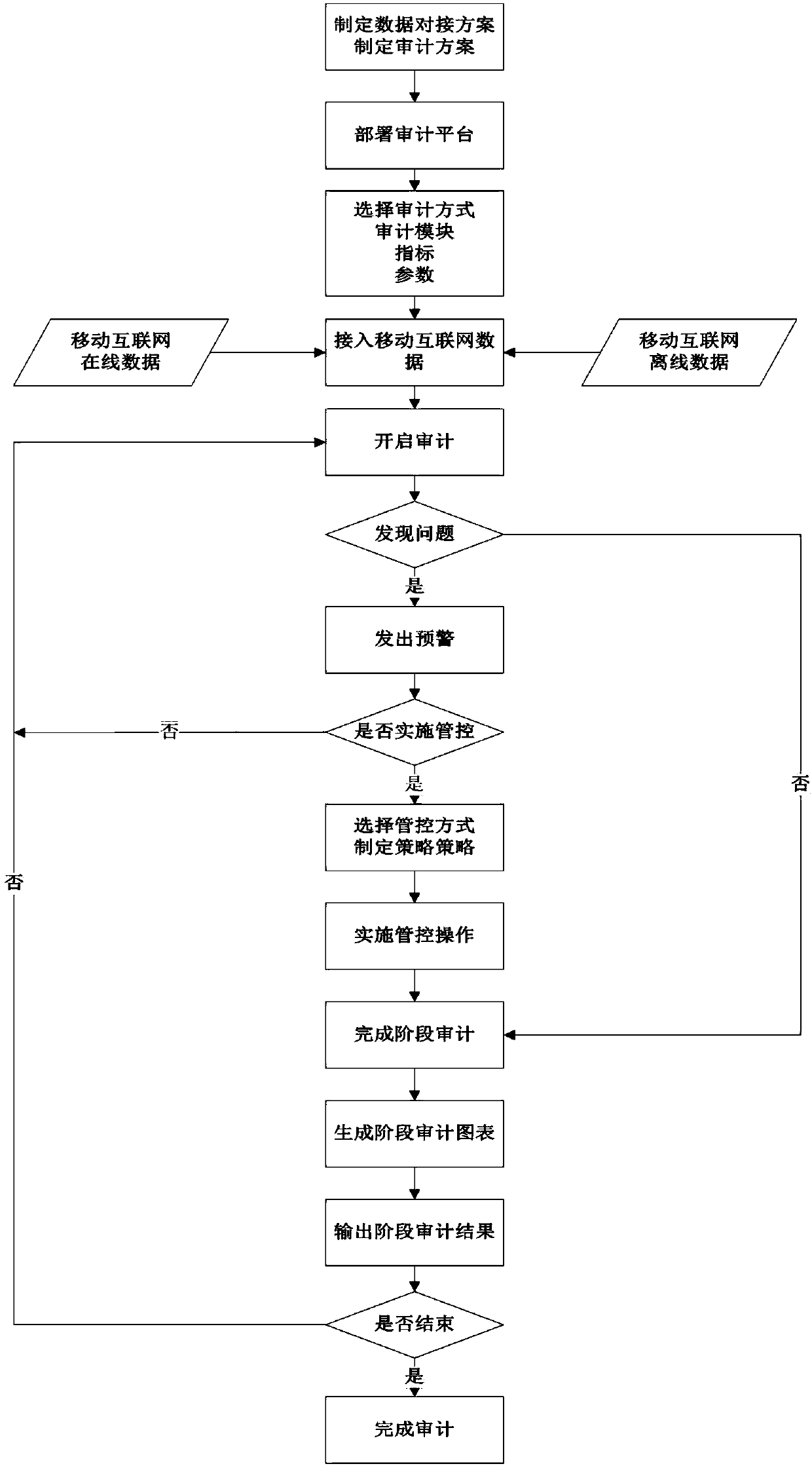
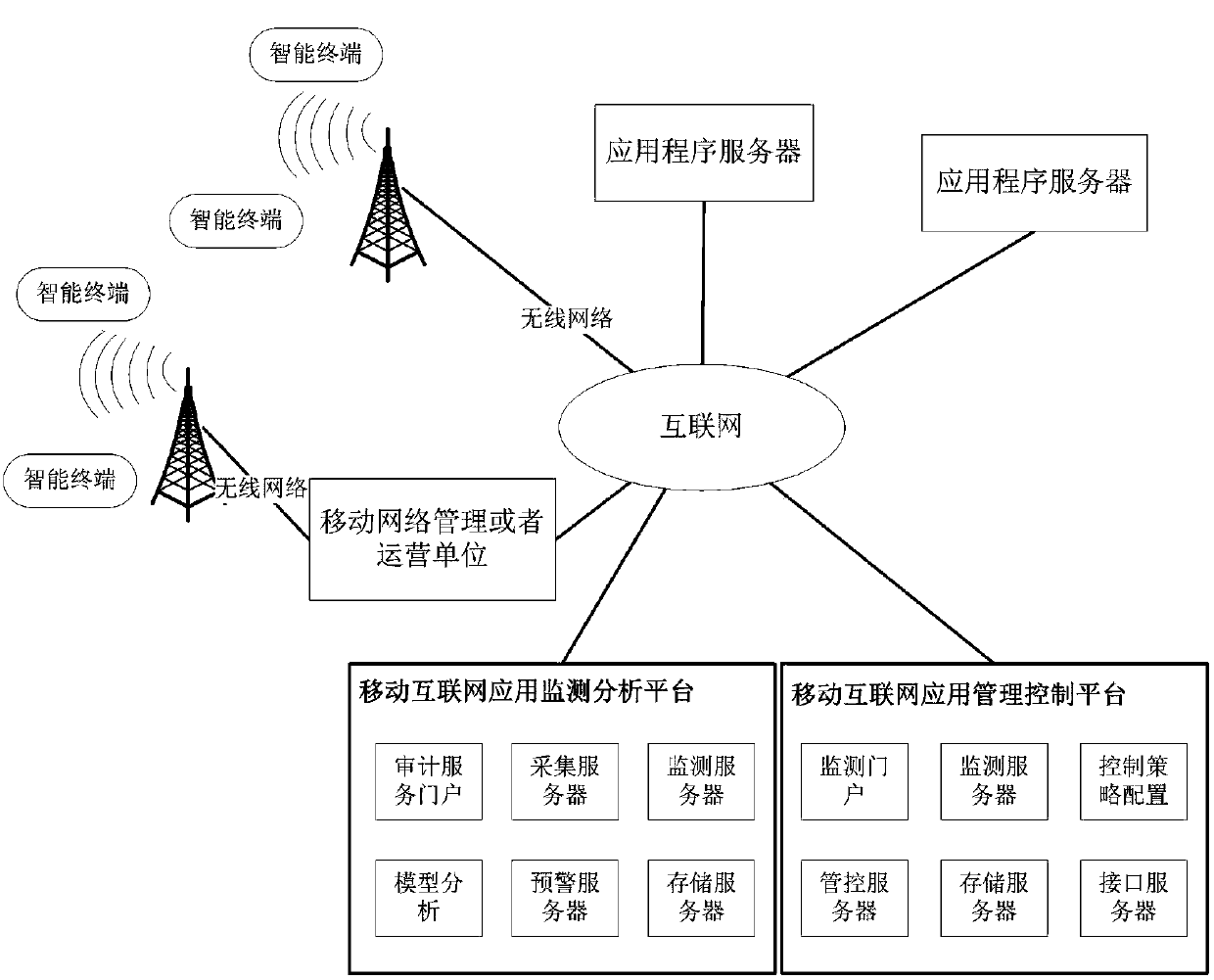
[0062] The implementation of the mobile Internet-oriented security audit system includes four aspects:
[0063] First, establish an audit system implementation process suitable for various objects of mobile Internet management and operation units. According to the specific needs of different service providers, design and specify the implementation process of the audit system. Comprehensive consideration is given to the audit function of the mobile Internet system and the requirements of the audit platform, the selection of parameters and modules of the audit system, the real-time collection of data and the use of historical data, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com