A Shared Key Secure Communication Method Fused with Private Information
A technology for private information and secure communication, applied in key distribution, can solve the problems of reducing the randomness of generated key bits, reducing channel characteristics, and rare research on shared key secure communication between wired channels and fiber channels, so as to improve the channel. Effects of reciprocity, increased randomness, enhanced security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further explained below in conjunction with the drawings.
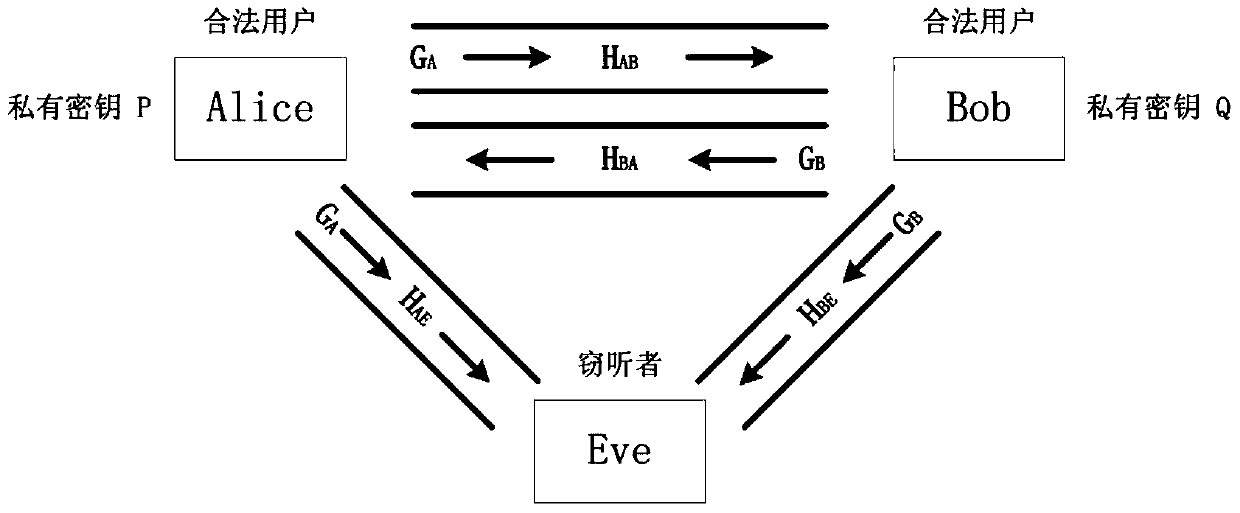
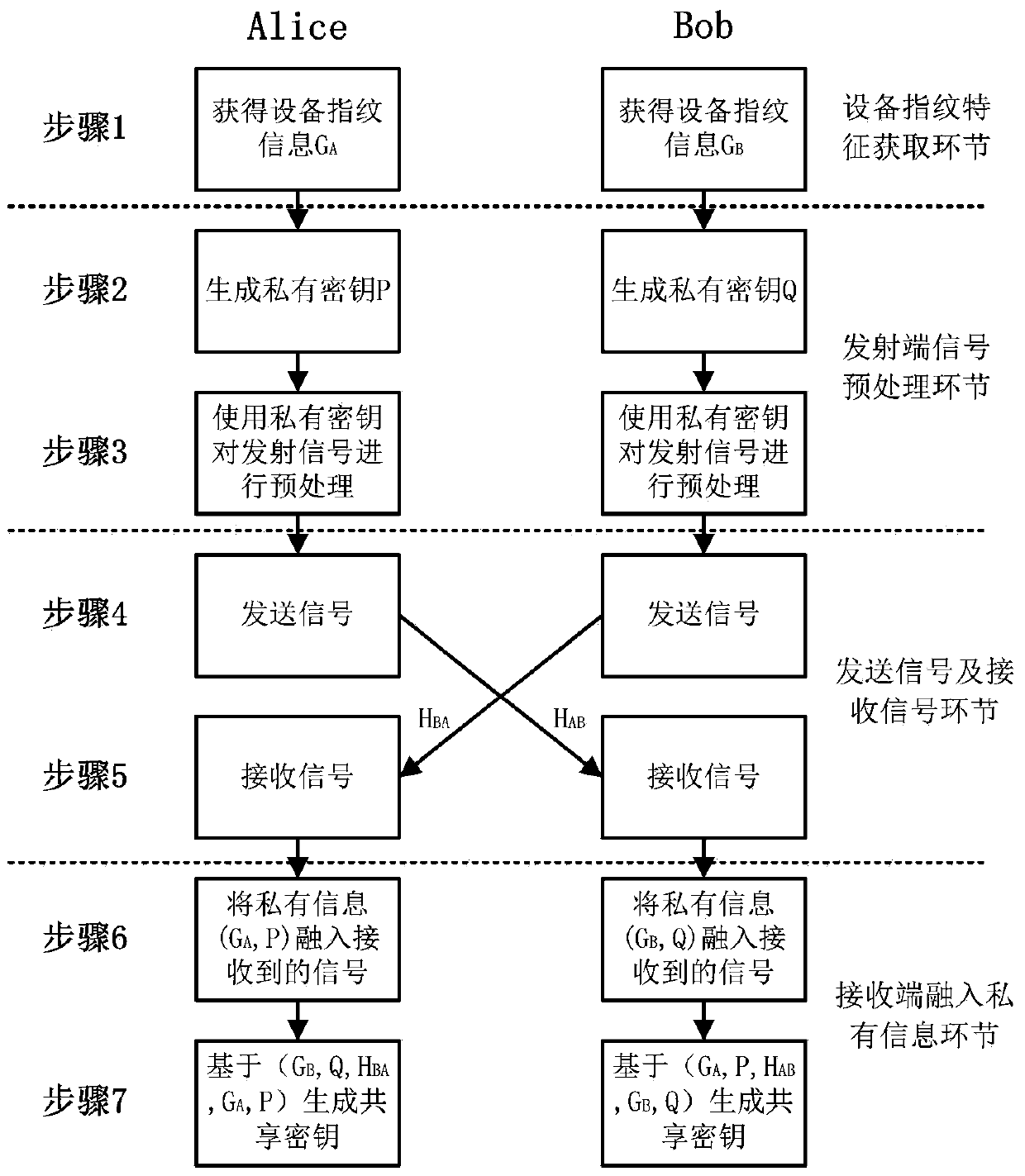
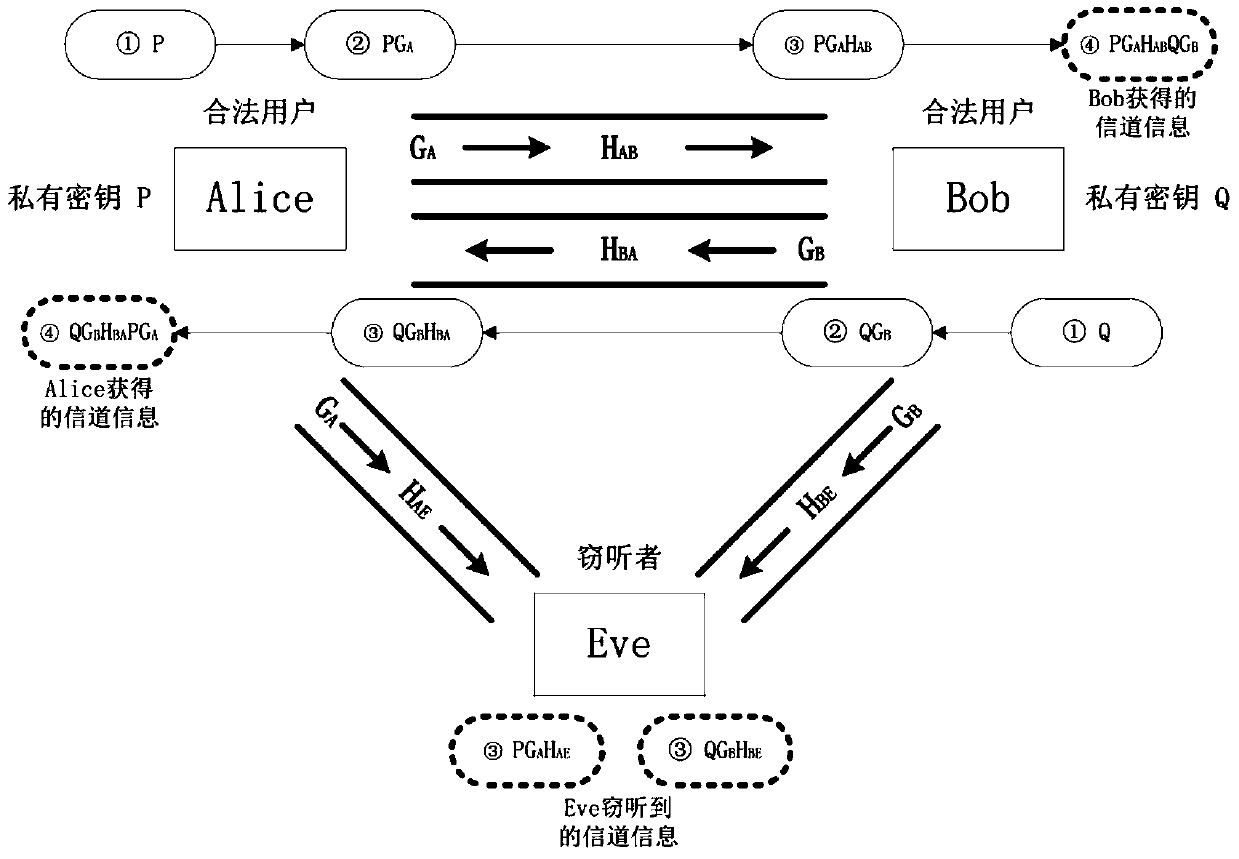
[0027] A shared key secure communication method that integrates private information. In the TDD communication system, the device fingerprint information of the communicating parties and the generated private key are taken as implicit private information, and these private information are protected through public channel characteristics And pass it to the other party, and then at the receiving end, by superimposing the known private information on the received signal, the reconstruction of channel reciprocity is completed, thereby realizing the secure communication of the shared key that integrates channel characteristics and private information. The method includes four links: the device fingerprint feature acquisition link, the signal preprocessing link at the transmitter, the signal sending and receiving link, and the receiver integrating private information. In the implementation p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com