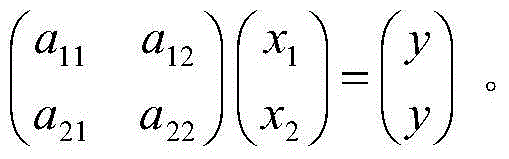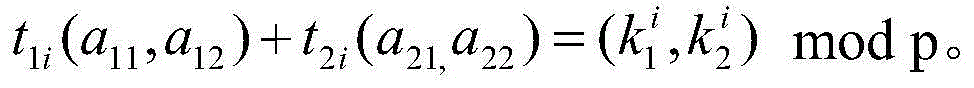Multi-user encryption data comparable encryption method and encryption data method
A technology for comparing encryption and encrypting data, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as inability to achieve multi-user tag comparison, and achieve the effect that it is not easy to be attacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0024] This article specifically takes the whole process from ciphertext encryption to ciphertext comparison as an example, and takes one of the feasible algorithms as an example to give a specific example.
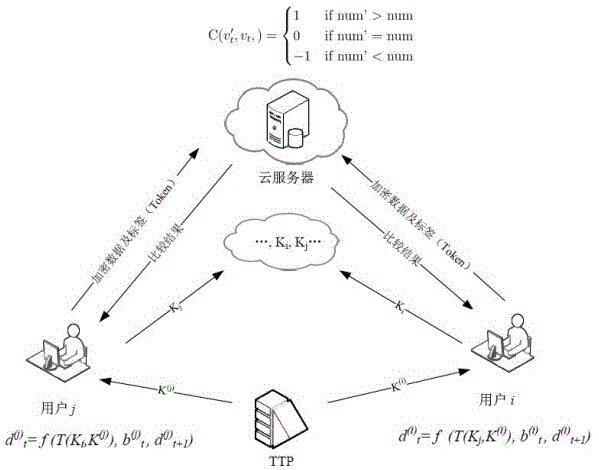
[0025] by figure 1 As shown, in this specific embodiment, user i (using U i ) and user j (indicated by U j Representation) is described in detail as an example of comparing requests and obtaining comparison results through the cloud service platform. Before each user releases the data type of the data that can be used for comparison to the cloud service platform, it will generate a tag for the encrypted data according to the private key of the data type L of the data to be released combined with the specific private key assigned by a trusted third party . Encrypted data and label conversion information that can be used for comparison; the label is used to convert your own label into a new label by using the other party's label conversion information when it needs to be ...
specific Embodiment 2
[0105] The difference from the first embodiment is that the user U i Convert data type L and its corresponding label to information K Li Information binding (L, K Li ) is stored on the cloud server; user U j The data under the data type L needs to be connected with the user U i When comparing data of this type, the user U j Send a comparison request to the cloud server; user U i The comparison request is received by the cloud server, and if the comparison request is agreed, the cloud server converts the tag of the data type into information K Li send to user U j ; j Convert information K using tags Li Convert its label to label T Lj , then by the label T Lj Generate comparable encrypted data M Lj , and label T Lj Comparable encrypted data M Lj sent to the cloud server; the cloud server utilizes the tag T Lj For comparable encrypted data M Li and comparable encrypted data M Lj Make a comparison and send the result of the comparison to the user U j .
[0106] Th...
specific Embodiment 3
[0107] The difference from Embodiments 1 and 2 is that the user U i Convert data type L and its corresponding label to information K Li Bind and publish (L, K Li ); user U j The data under the data type L needs to be connected with the user U i When comparing data of this type, directly obtain the bound label conversion information K Li , U j Convert information K using tags Li Convert its label to label T Lj , then by the label T Lj Generate comparable encrypted data M Lj , and label T Lj Comparable encrypted data M Lj sent to the cloud server; the cloud server utilizes the tag T Lj For comparable encrypted data M Li and comparable encrypted data M Lj Make a comparison and send the result of the comparison to the user U j .
[0108] In this way user U i No need to store label conversion information K Li , and when comparing U j No need to U i send request.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com