A Global Offset Table Protection Method Based on Address Randomization and Segment Isolation
An offset table and address technology, which is applied in computer security devices, platform integrity maintenance, instruments, etc., can solve the problems of time-consuming function analysis and analysis waste, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
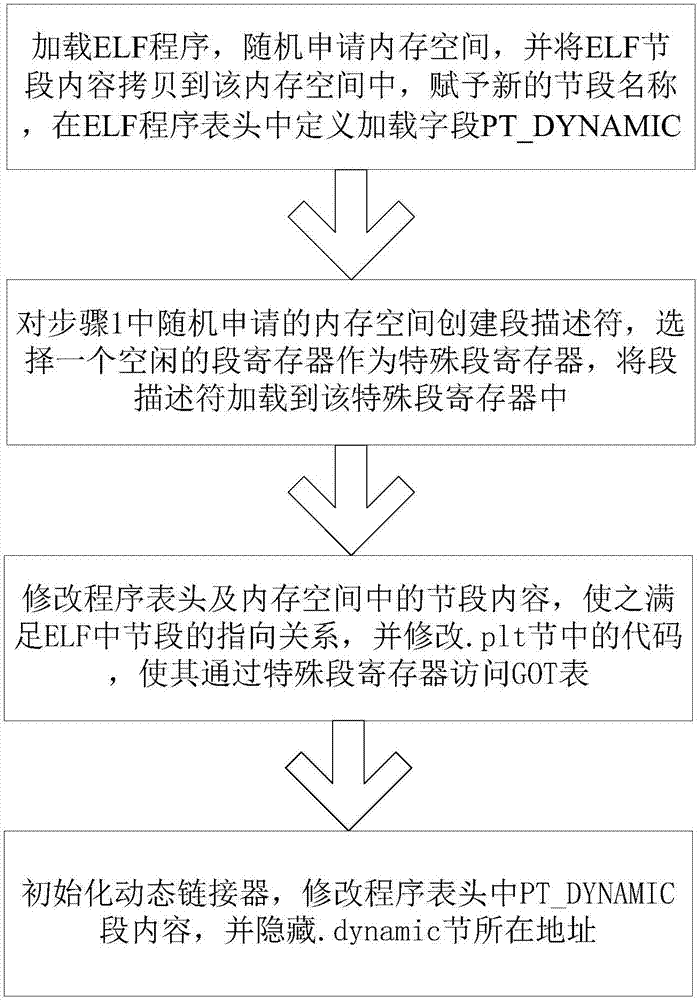
[0026] Example 1, see figure 1 As shown, the global offset table protection method based on address randomization and segment isolation includes the following steps:
[0027] Step 1. After the ELF program is loaded, randomly apply for a memory space, copy the content of the ELF segment into the memory space, give a new segment name, and define the loading field PT_DYNAMIC in the ELF program header to describe .dynamic section information;
[0028] Step 2. Create a segment descriptor for the randomly applied memory space in step 1, select a free segment register as a special segment register, and load the segment descriptor into the special segment register;
[0029] Step 3. Modify the program header and the section content given the new section name in Step 1 to satisfy the pointing relationship of the section in the ELF, and modify the code in the .plt section to access the GOT through the special segment register surface;
[0030] Step 4. Initialize the dynamic linker, mo...
Embodiment 2
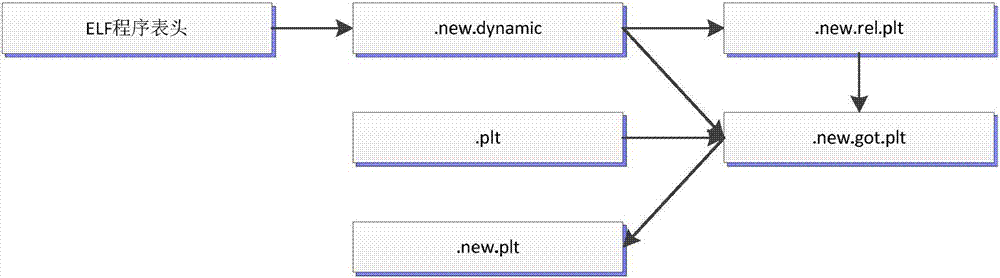
[0032] Example 2, see Figures 2 to 3 As shown, it is basically the same as the first embodiment, except that: in the step 1, randomly applying for a memory space and copying the content of the ELF segment into the memory space specifically includes randomly applying for at least three pages of memory space on demand, including Readable and executable pages, readable and writable pages, and readable and writable pages, where .plt is copied to a readable and executable page, denoted as .new.plt; .rel.plt is copied to a readable-only page, denoted as . For .new.rel.plt; .dynamic and .got.plt are copied to readable and writable pages, and recorded as .new.dynamic and .new.got.plt respectively. The memory space of the three pages can be any address space. Three unused pages of memory.
[0033] Preferably, in step 1, the content of the ELF section is copied to the memory space, and the new section name is assigned to specifically include: copying the content of the .plt, .rel.plt,...
Embodiment 3
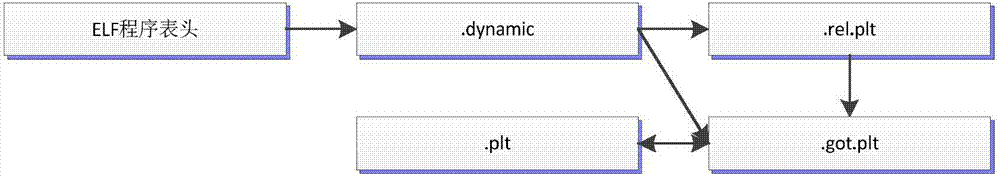
[0041] Embodiment 3, the technical scheme of the present invention is further introduced in conjunction with specific embodiments, and the specific implementation process is as follows:
[0042] The ELF program header table contains a section of type PT_DYNAMIC, which contains the .dynamic section. By parsing the .dynamic section, you can obtain the starting offset of .plt.got, .rel.plt section, and .rel.plt section size, the type of the relocation item in .rel.plt; according to the obtained information about the .rel.plt section, you can know the number of library functions referenced by the program:
[0043] libfun_num=size(.rel.plt) / sizeof(Type_Rel)
[0044] Among them, Type_Rel is determined as Elf32_Rel or Elf32_Rela according to the type of the relocation table. The definitions of these two types are as follows Figure 7 shown.
[0045] According to the number of library functions, the size of .got.plt is calculated, size(.got.plt)=libfun_num*4+12, the library function...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com