Identity authentication method
An identity verification method and technology for verifying requests, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve data conflicts, reduce user experience and other problems, and achieve the effect of avoiding data conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
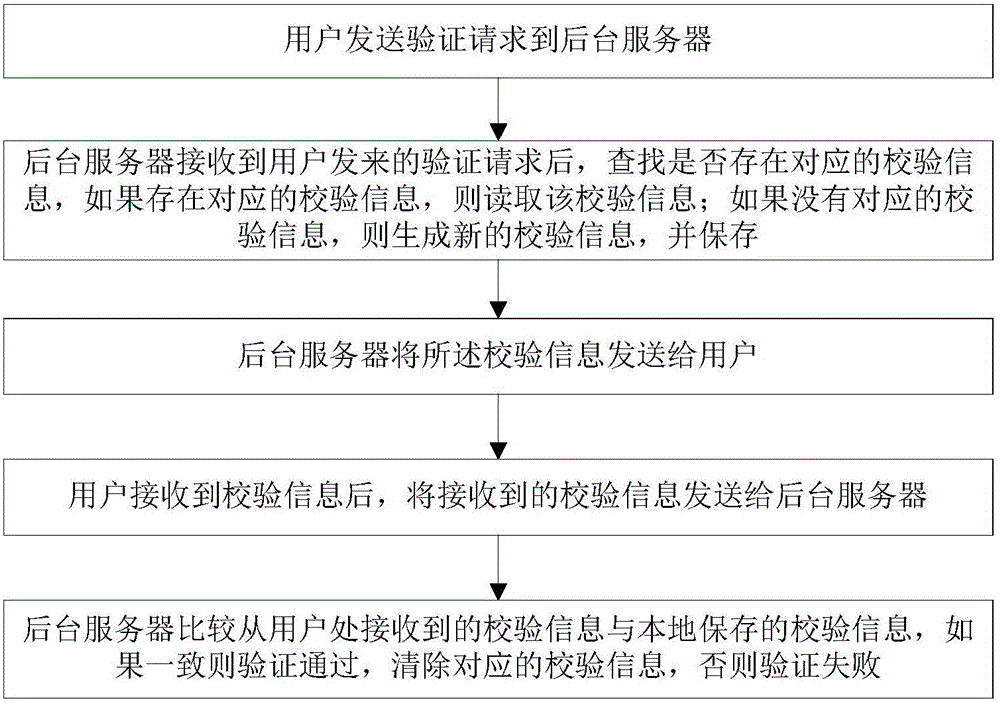
[0025] The technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments, and the following embodiments do not constitute a limitation of the present invention.
[0026] Identity verification is to determine whether the currently logged-in user is indeed a registered legal user by comparing whether the verification information entered by the user is consistent with the last verification information stored in the background server. Verification is usually achieved through channel modes such as SMS, email, WeChat, etc. The essence is to determine that the currently logged-in user is indeed a user of certain related information, such as the owner of the mobile phone number registered during registration, or the email address registered during registration. , The head of household of WeChat ID.
[0027] In this embodiment, the verification information (generally a verification code) sent by a sho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com