Method and system for detecting Web application
A web application and function point technology, applied in the field of computer networks, can solve problems such as missing web pages, missing web pages, and inability to accurately identify loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
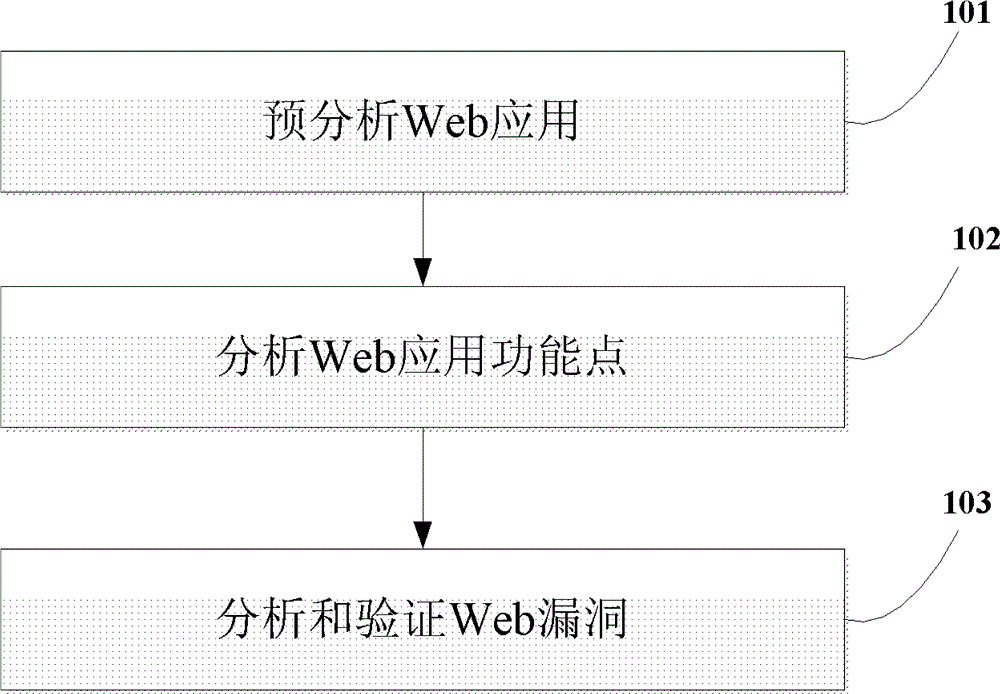
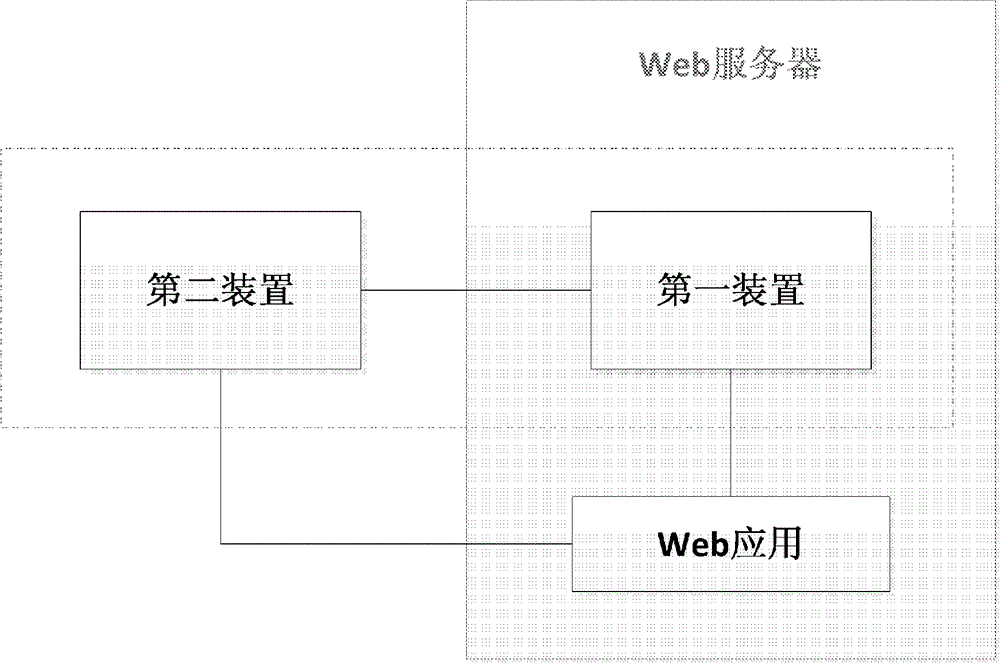
[0021] figure 1 is a flowchart of a method for detecting a Web application according to one aspect of the present invention. As shown in the figure, the method for detecting a web application includes one or more of the following processes. In process 101, a web application is pre-analyzed. In this process, information related to function points of the web application and / or a set of vulnerability templates for the web application are determined, where the vulnerability template is a script for detecting a specific vulnerability. In process 102, Web application function points are analyzed. In this process, a subset of vulnerability templates applicable to the function point of the web application is determined from the set of vulnerability templates. In process 103, web vulnerabilities are analyzed and verified. In this process, the second device analyzes and verifies web vulnerabilities according to the HTTP response and / or monitoring information.
[0022] In one embodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com