Malware program sample family naming method and device
A malicious program and sample technology, which is applied in the field of malicious program sample family naming methods and devices, can solve the problems of inconvenient malicious program sample family security processing, no effective naming scheme for malicious program sample families, etc., and achieve the effect of improving security processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
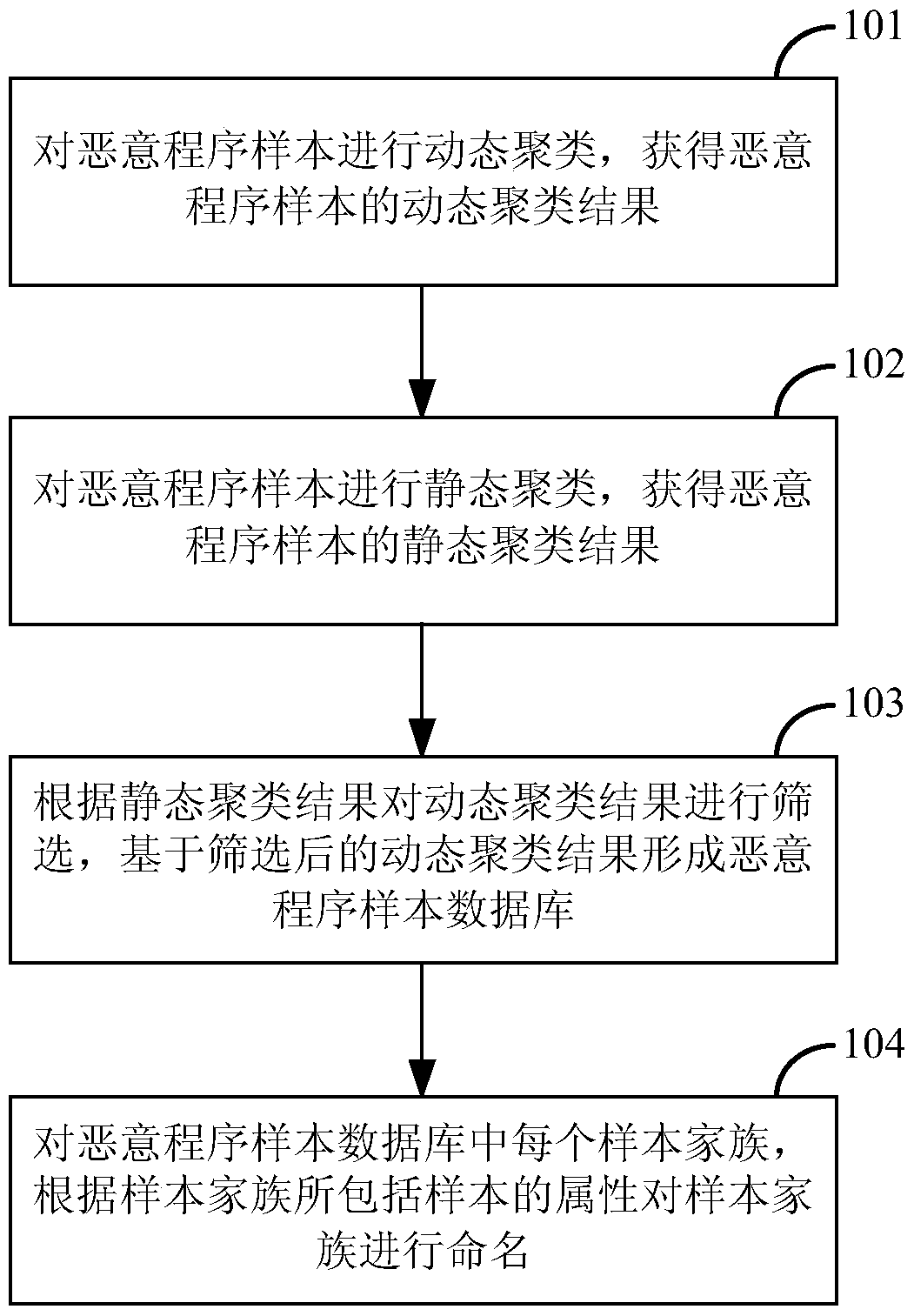
[0042] The inventor considers that, on the one hand, before naming the sample family, it is necessary to accurately determine the sample family, and the existing malicious program sample clustering methods include dynamic clustering and static clustering, but for malicious program samples Regardless of whether dynamic clustering or static clustering is performed, the clustering results obtained are not accurate. For example, some behaviors of samples may not be triggered during dynamic clustering, resulting in incomplete collection of sample behaviors. At this time, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com