Method and apparatus to encrypt plaintext data
A technology of plaintext data and temporary data, applied in encryption devices with shift registers/memory, digital transmission systems, secure communication devices, etc., can solve problems such as technical inefficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The word "exemplary" or "example" is used herein to mean "serving as an example, instance, or illustration." Any aspect or embodiment described herein as "exemplary" or as an "example" is not necessarily to be construed as preferred or advantageous over other aspects or embodiments.
[0016] Embodiments of the invention relate to techniques to provide enhanced mechanisms for protecting data stored in memory. In particular, methods and procedures for extending the functionality of block ciphers to enhance memory encryption are described. Additionally, these techniques can also improve performance, throughput, and power consumption, as will be described below. These techniques can also be used to improve performance, throughput and power consumption for the purpose of secure data storage transmitted across (wired or wireless) networks.
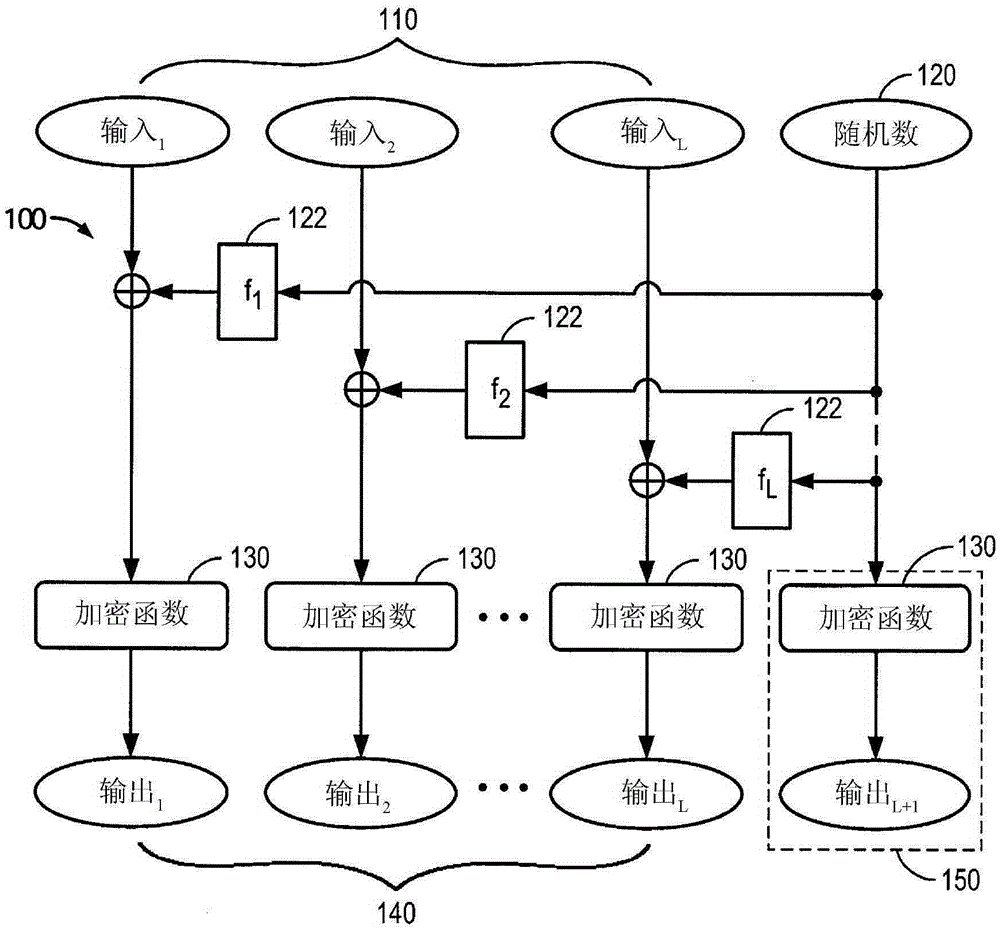
[0017] In one embodiment, an encryption scheme is employed in which a series of L plaintext data input blocks are encrypted using an e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com