(k,n) threshold based user-friendly visual secret sharing method
A secret sharing and threshold technology, applied in the field of information security, can solve problems such as low security, inconvenient management, and damage to image integrity, and achieve the effects of improving contrast, improving visual effects, and increasing the scope of image application.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0036] The specific embodiments of the present invention will be described below with reference to the accompanying drawings.
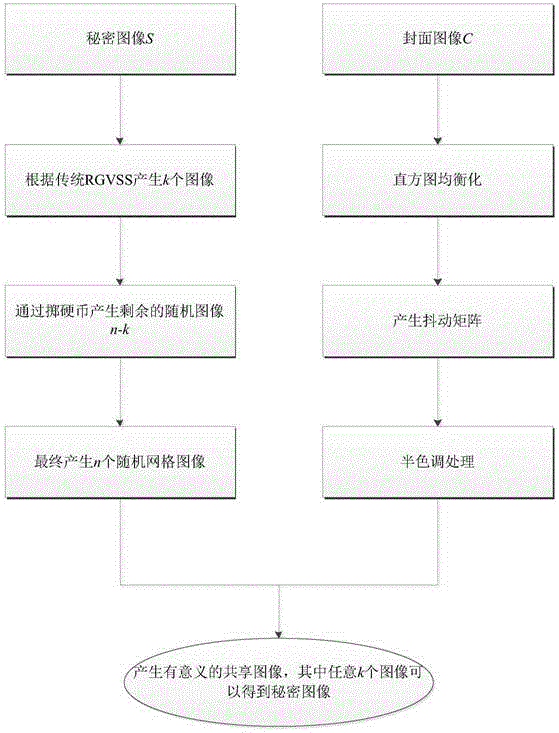
[0037] Reference figure 1 , The implementation steps of the present invention are as follows:
[0038] Step 1. Input a secret image S and n cover images C to be protected.
[0039] The secret image S is the image that needs to be protected. The cover image C is used to hide the secret image S. The size of the cover image and the secret image must be equal, here set to r×c, where r represents the height of the secret image and the cover image, and c represents the secret image and The width of the cover image.
[0040] Step 2: Use the traditional random grid-based method to generate a shared image. The secret image S uses a binary image. For the traditional random grid-based visual secret sharing method, firstly, the pixel S of the secret image S i,j For coding, the following first introduces the traditional random grid.
[0041] 2a) Generate random grid G a...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap