An Image Encryption Method
An encryption method and image technology, applied in image watermarking, image data processing, image data processing, etc., can solve problems such as differential attacks
Inactive Publication Date: 2019-01-22
GUANGDONG OCEAN UNIVERSITY
View PDF2 Cites 3 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
However, there are still many problems that have not been effectively resolved: first, when scrambling and encrypting, the encryption algorithm only considers the scrambling of the pixel position of the image, that is to say, the statistical characteristics of the plaintext image before and after scrambling, especially the histogram The graph remains unchanged; second, the feature "pixel sum" of the plaintext image does not change before diffusion, which is easy to cause a differential attack; third, the key stream used in the image encryption process has nothing to do with the plaintext image, which leads to different image When encrypting, the key stream used remains the same; fourth, the secret key is only used to generate the key stream during the encryption process, and does not directly participate in the acquisition of the ciphertext image
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
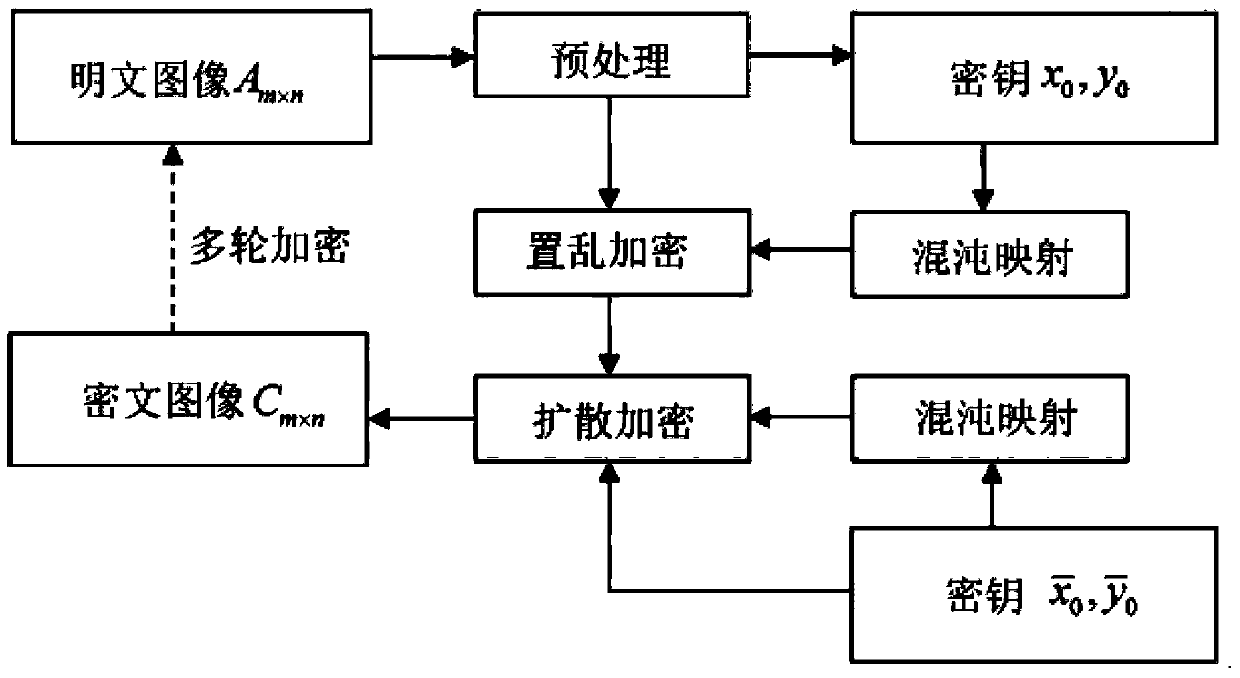
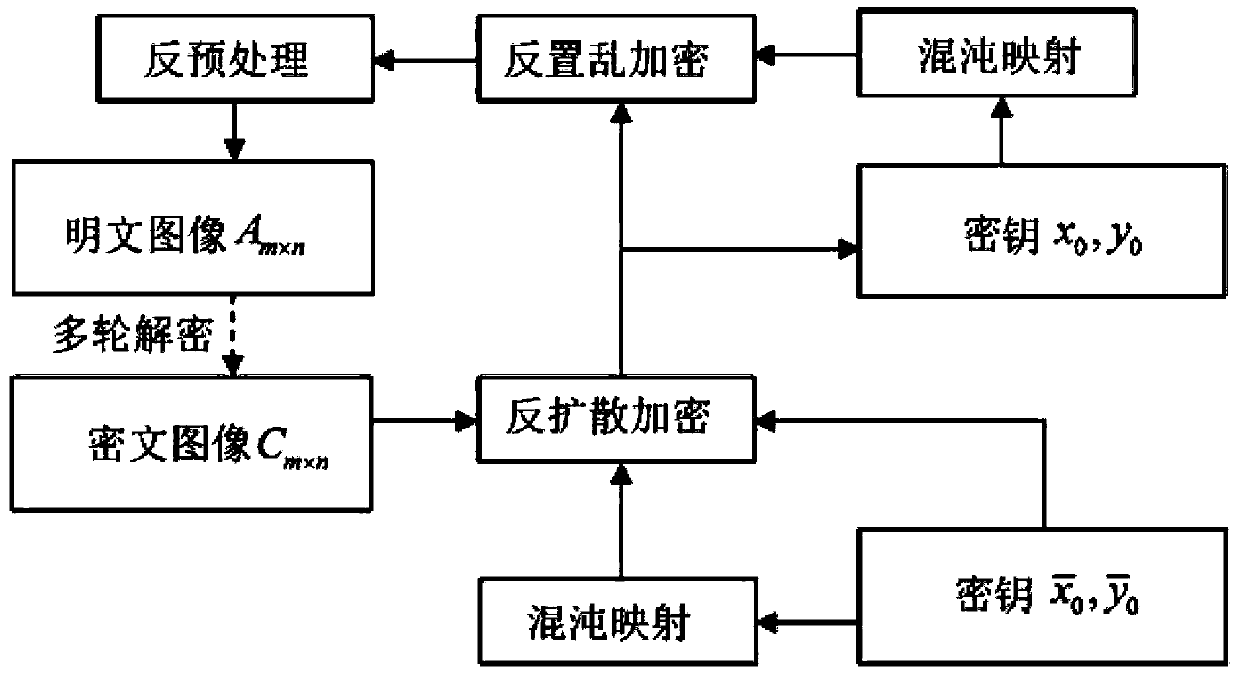
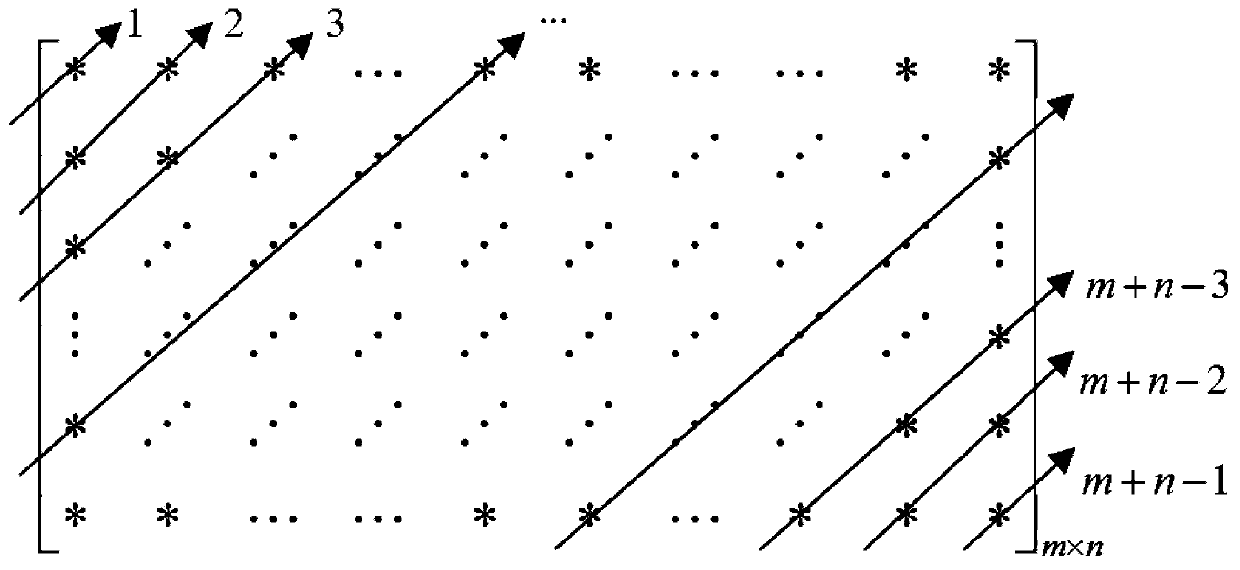
The invention provides a novel image encryption method based on correlation between chaos and plaintext. The method comprises the steps: carrying out row and column updating of a plaintext image A, and obtaining a processed image E; employing the modular operation of a gray level 256, changing the pixel sum of the image through the modular operation between rows and the modular operation between columns, and breaking the strong correlation between the adjacent rows and the adjacent columns of an original plaintext image; enabling the pixel sum s of the image E to serve as the feature of the image, extracting the feature of the image, participating the generation of a key stream, carrying out the second layer encryption through scrambling encryption, and obtaining an image Q; and solving a problem that a conventional algorithm employs the same key stream while encrypting different images. Through the gray value diffusion of the image, the method builds the mutual influence between two adjacent pixels, and a secret key directly participates in the output of a ciphertext image. In order to achieve an avalanche effect, the mutual influence between two adjacent pixels is built through the key stream. Meanwhile, a second group of secret keys are designed to participate in the output of the ciphertext image, thereby achieving the third layer encryption.
Description
technical field The present invention relates to the field of image encryption, and more specifically, to an image encryption method. Background technique With the development and popularization of computer networks, the exchange of digital information (such as: video, audio and images, etc.) is becoming more and more common. Among them, images, as one of the most direct ways for people to understand the natural world, have been widely used in daily life. However, in an open network environment, unauthorized third parties can easily intercept, read or disseminate these image information. In order to protect the security of images, especially private images, military images and even images involving state secrets, people have proposed to encrypt and hide images. Unlike traditional text, images have the characteristics of large data, high redundancy and strong correlation, which makes traditional encryption algorithms (such as: AES, DES and IDEA, etc.) unable to effectively ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): G06T1/00
CPCG06T1/0021G06T1/005
Inventor 叶国栋黄小玲
Owner GUANGDONG OCEAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com