Key Virtual Link Protection Method Based on Parallel Multipath
A virtual link and multi-path technology, applied in the field of network security, can solve problems such as paralysis and inefficient network operation, and achieve the effect of improving robustness, improving security performance, and avoiding abnormal network services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
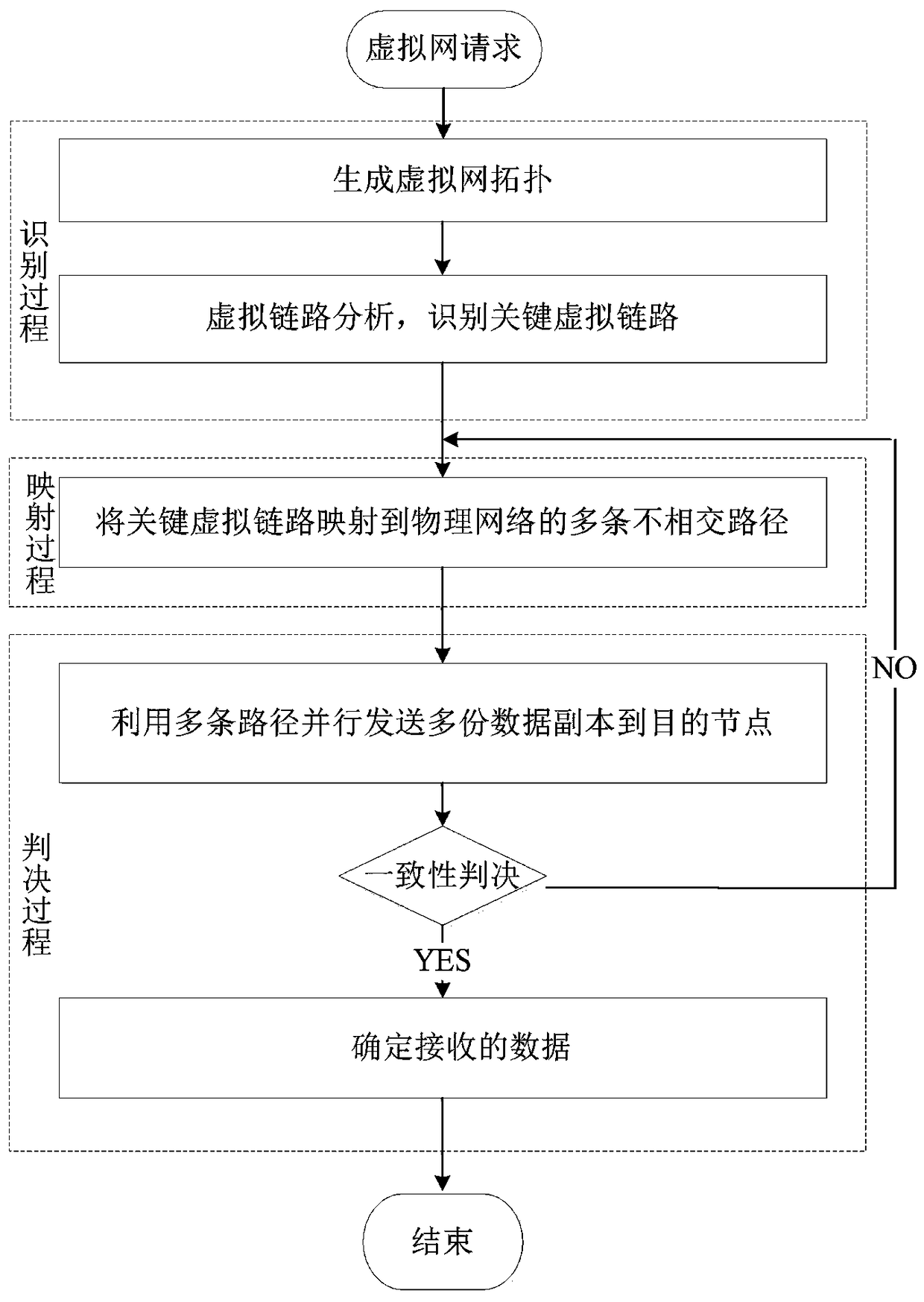
[0023] Embodiment one, see figure 1 As shown, a key virtual link protection method based on parallel multipathing includes the following steps:
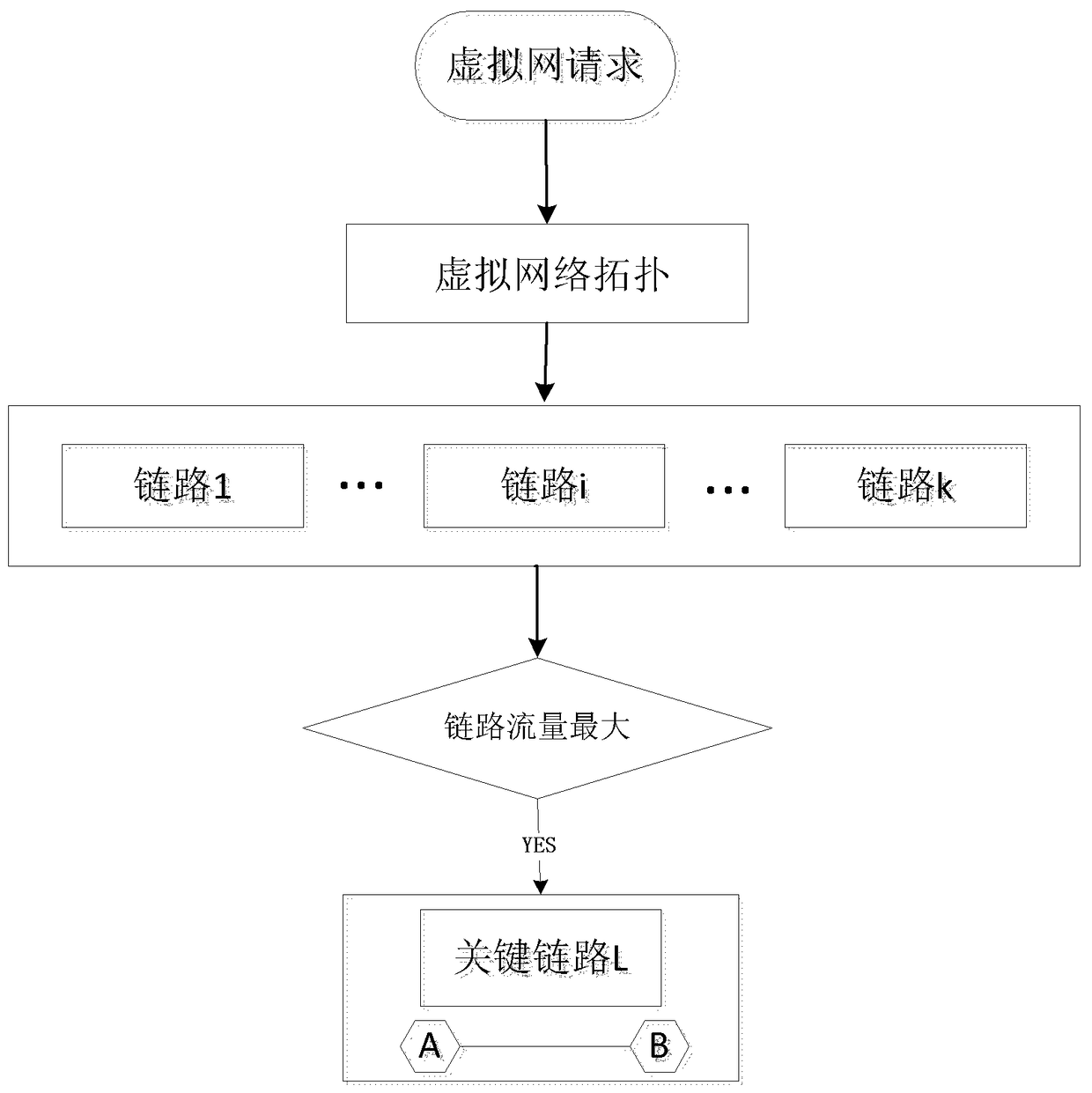
[0024] Step 1, virtual link identification, generate a virtual network topology according to the virtual network request, analyze the traffic demand of each virtual link in the virtual network topology, and select the link with the largest traffic as the key virtual link L;
[0025] Step 2, key virtual link L mapping, the key virtual link L identified in step 1 is mapped to multiple disjoint paths of the physical network, and the traffic of the key virtual link L is carried in parallel;
[0026] Step 3, data judgment, use the multiple disjoint paths of the physical network in step 2 to send multiple copies of data to the destination node, and cache the data at the destination node, according to the consistency judgment mechanism, that is, satisfy the large number judgment and select the consistent The data with the largest amount is...
Embodiment 2
[0028] Embodiment two, see Figure 1~4 As shown, a key virtual link protection method based on parallel multipathing includes the following steps:
[0029] Step 1, virtual link identification, generate a virtual network topology according to the virtual network request, analyze the traffic demand of each virtual link in the virtual network topology, and select the link with the largest traffic as the key virtual link L;
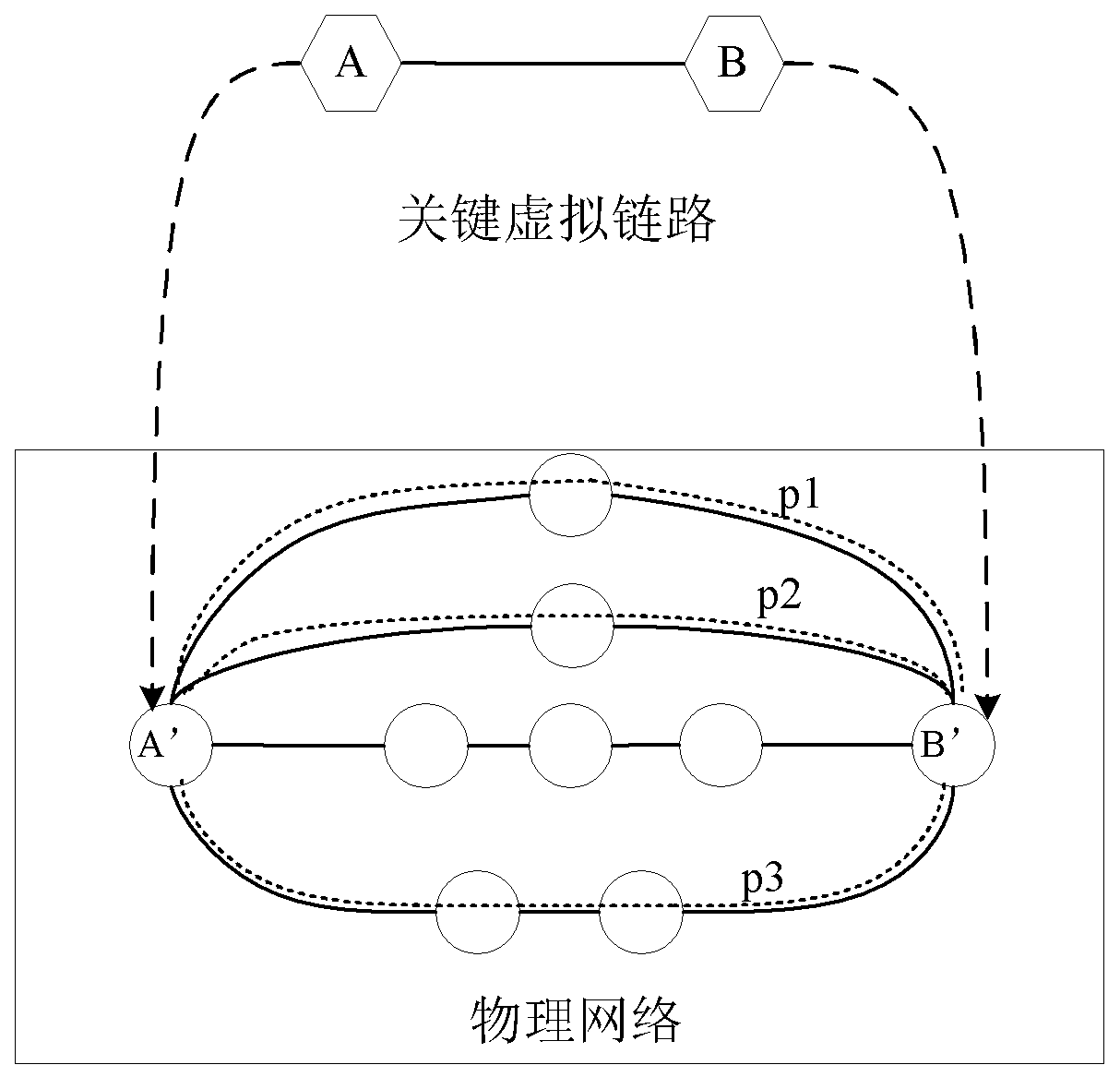
[0030] Step 2, key virtual link L mapping, the key virtual link L identified in step 1 is mapped to multiple disjoint paths of the physical network, and the traffic of the key virtual link L is carried in parallel;
[0031] Specifically, according to the requirements of the key virtual link L end node, the virtual end nodes A and B are mapped to the physical nodes A' and B' respectively, and A' and B' are respectively the source node and the destination node; according to the key virtual link According to the bandwidth and delay requirements of road L, selec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com