Implementation method of setting random comparison verification code in Internet webpage login system
A technology of login system and implementation method, which is applied in the direction of transmission system, electrical components, etc., can solve problems such as difficult identification of users, poor user experience, troubles, etc., and achieve the effect of protecting security, increasing complexity, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
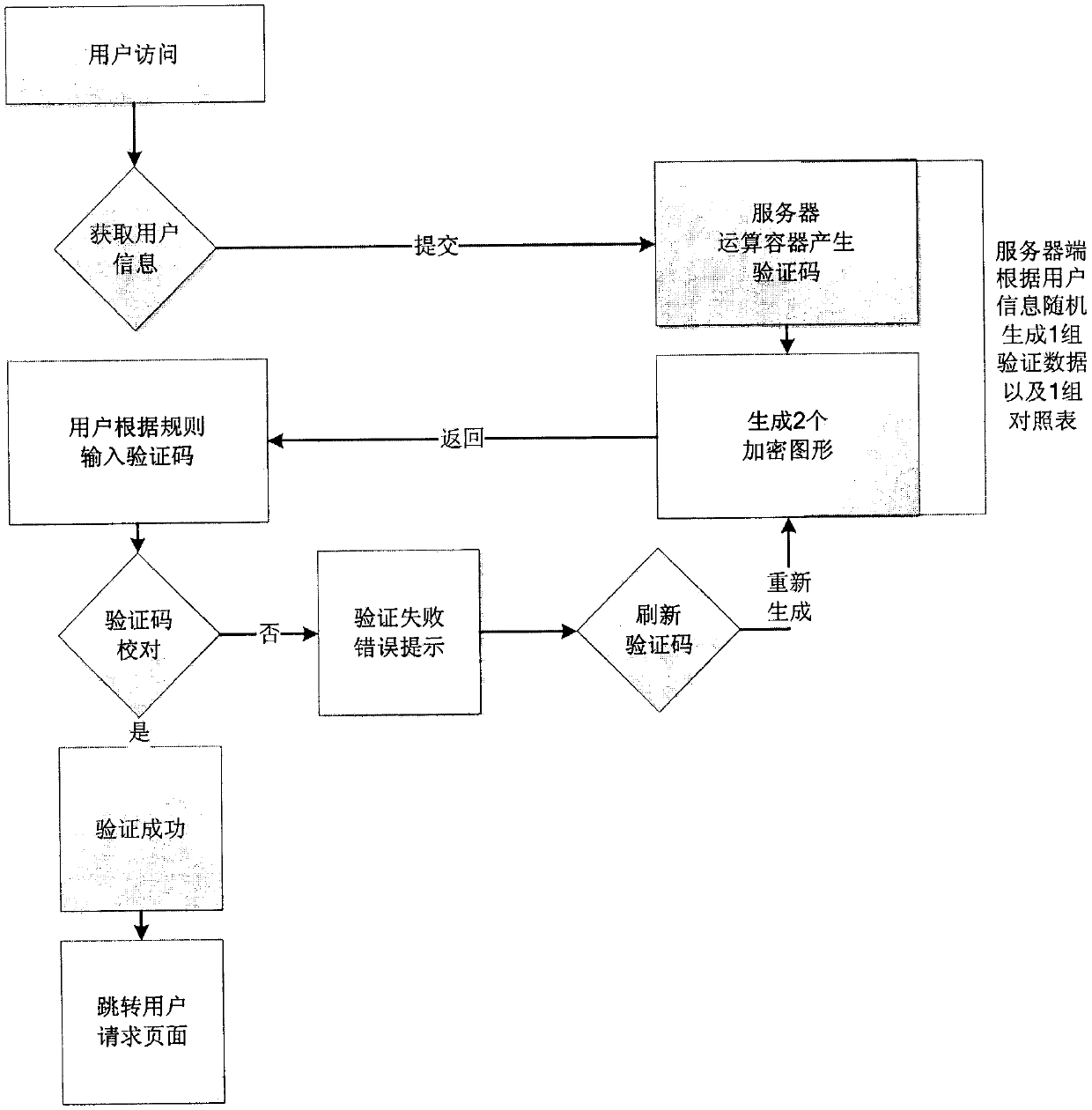
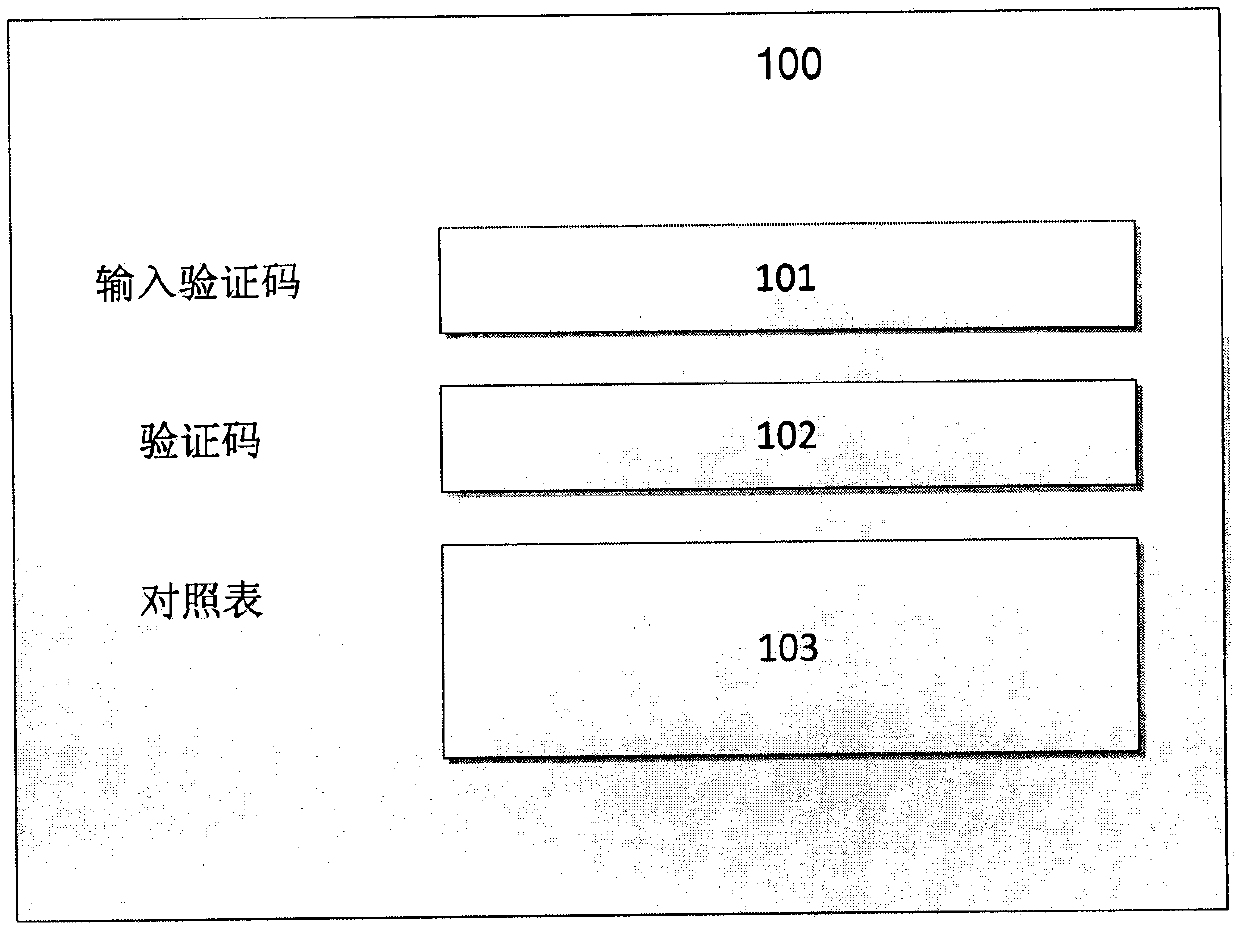
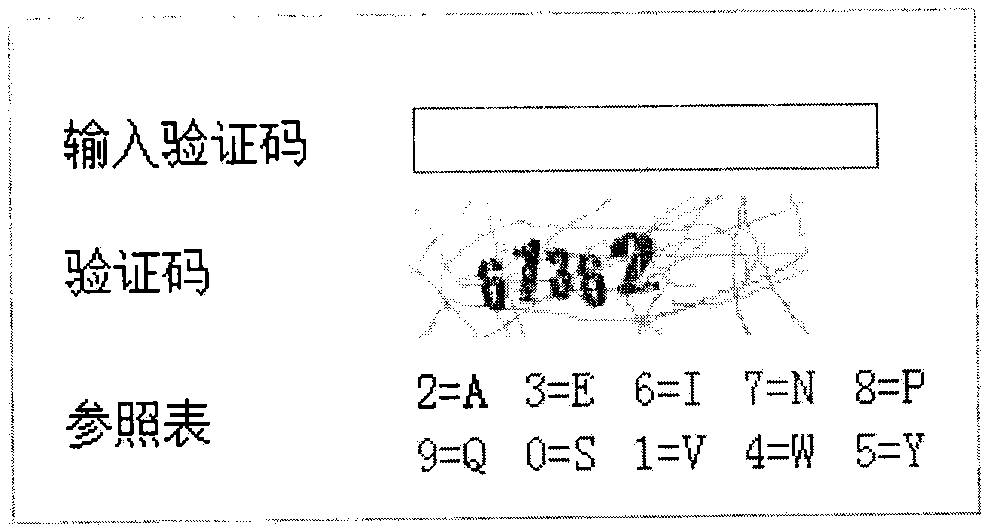
[0015] like figure 1 As shown, the implementation method of setting a random control verification code in the Internet web page login system of the present invention, that is, when the user logs in to the system, the server side of the login system randomly uses the generated algorithm of the operation container module according to the user information to encrypt the graph. A set of verification data and a set of comparison tables are generated in the form and reflected on the login interface at the same time. In this process, a randomly generated parameter number a (the number of digits of a is greater than or equal to 1) is preset in the system as the verification data, and then set The letter parameter b of 26 English letters with a value ran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com