Terminal unlocking method and terminal
A control method and terminal technology, applied in the communication field, can solve problems such as low operation efficiency, and achieve the effect of improving operation efficiency and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
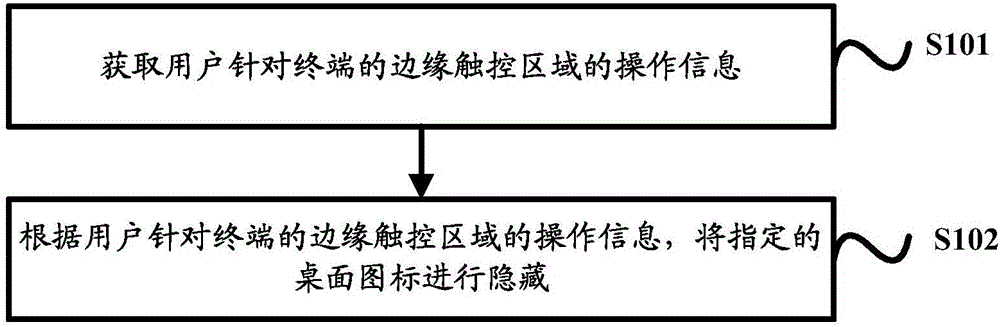
[0072] The embodiment of the present invention provides a terminal control method, please refer to figure 1 , which is a schematic flowchart of Embodiment 1 of the terminal control method provided by the embodiment of the present invention, as shown in figure 1 As shown, the method includes the following steps:
[0073] S101. Obtain operation information of a user on an edge touch area of a terminal.
[0074] Specifically, the purpose of the terminal acquiring the user's operation information on the edge touch area of the terminal is to determine whether the specified desktop icon can be hidden according to the operation information.
[0075] It should be noted that the terminals involved in the embodiments of the present invention may include but not limited to personal computers (Personal Computer, PC), personal digital assistants (Personal Digital Assistant, PDA), wireless handheld devices, tablet computers (Tablet Computer), Mobile phones, MP3 players, MP4 players, e...
Embodiment 2
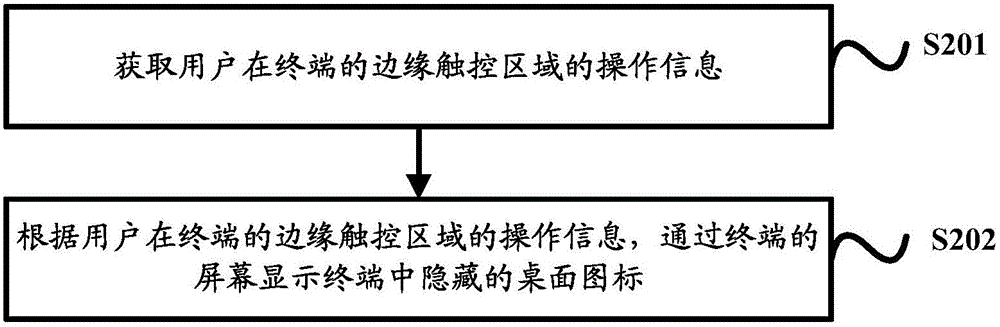
[0113] The embodiment of the present invention provides a terminal control method, please refer to figure 2 , which is a schematic flowchart of Embodiment 2 of the terminal control method provided by the embodiment of the present invention, as shown in figure 2 As shown, the method includes the following steps:
[0114] S201. Obtain operation information of a user on an edge touch area of a terminal.
[0115] Specifically, the purpose of obtaining the user's operation information on the edge touch area of the terminal is to determine whether the hidden desktop icons in the terminal can be displayed on the terminal screen according to the operation information.
[0116] It should be noted that the terminals involved in the embodiments of the present invention may include but not limited to personal computers (Personal Computer, PC), personal digital assistants (Personal Digital Assistant, PDA), wireless handheld devices, tablet computers (Tablet Computer), Mobile phones...
Embodiment 3
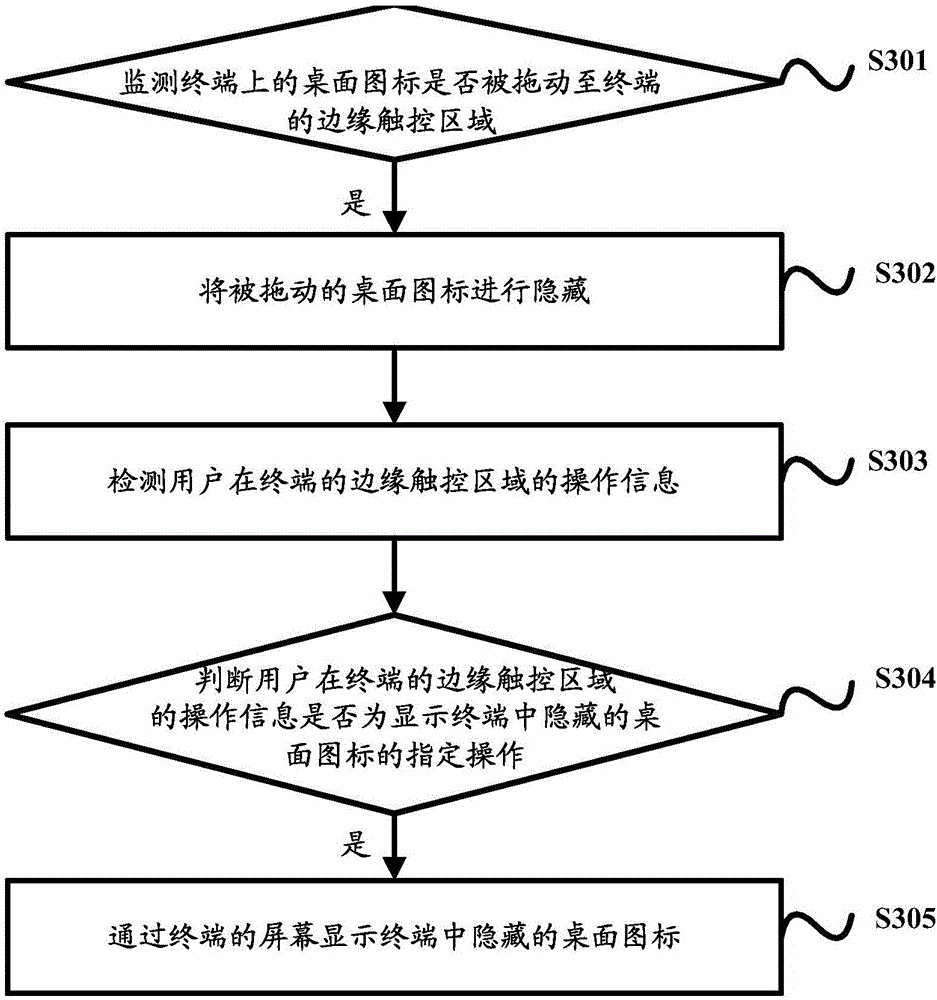
[0141] Based on the terminal control methods provided in the first and second embodiments above, the embodiment of the present invention further provides a specific implementation manner for realizing the above method embodiment, please refer to image 3 , which is a schematic flowchart of Embodiment 3 of the terminal control method provided by the embodiment of the present invention, as shown in image 3 As shown, the method may specifically include:
[0142] S301. Detect whether a desktop icon on a terminal is dragged to an edge touch area of the terminal.
[0143] S302, if yes, hide the dragged desktop icon.
[0144] S303. Detect operation information of the user on the edge touch area of the terminal.
[0145] S304, judging whether the user's operation information on the edge touch area of the terminal is designated operation information of a hidden desktop icon displayed in the terminal. ,
[0146] S305, if yes, display the hidden desktop icon in the terminal th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com