Scheme for simulating master user attack in mobile scene based on cognitive radio network
A technology for cognitive radio and mobile scenarios, applied in the field of imitating the main user attack scheme, it can solve problems such as the fixed value of the transmission power of malicious users, and achieve the effects of intelligent stability, strong attack performance, and large attack range.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
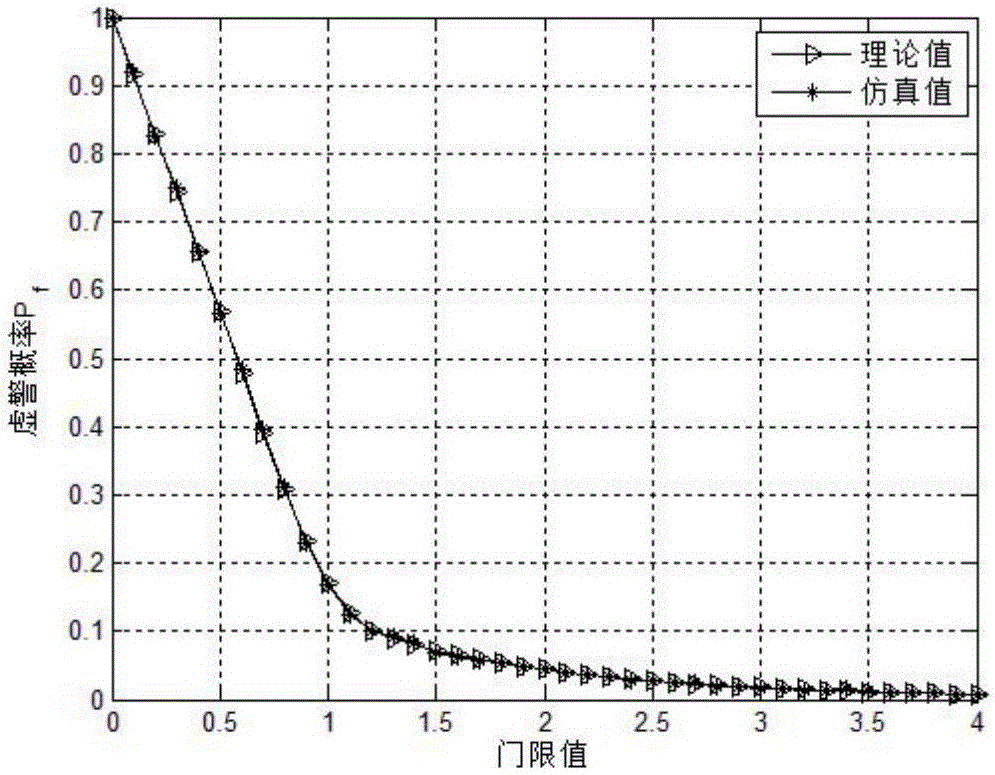
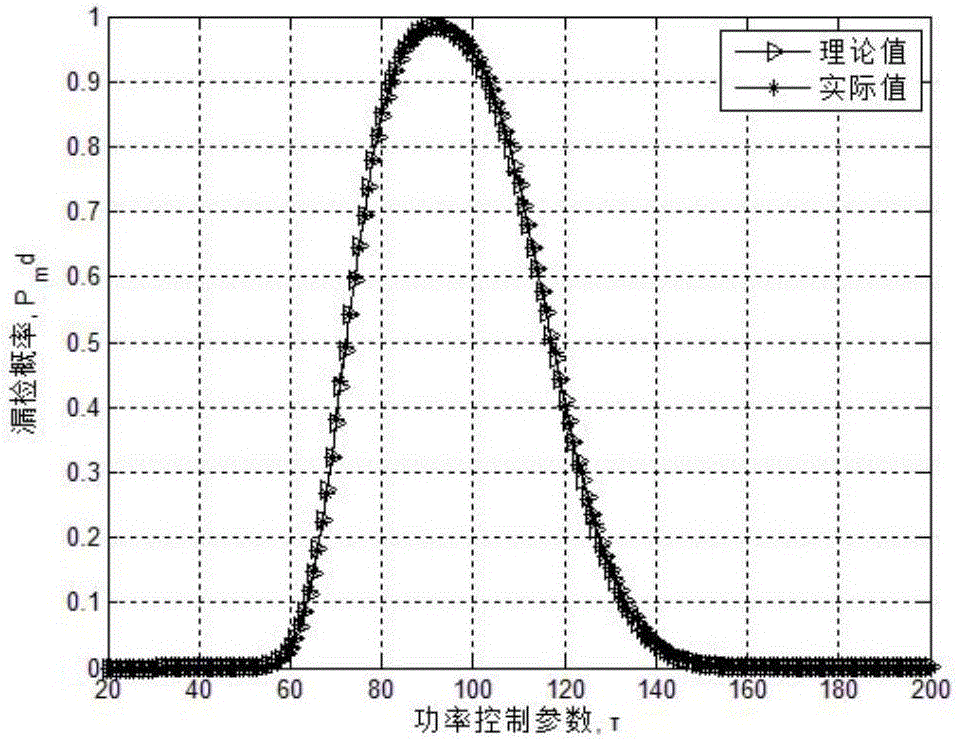
[0035] like figure 1 , 2 , 3, the present invention discloses a cognitive radio network-based imitation master user attack scheme in a mobile scenario, and the attack strategy includes the following specific steps:
[0036] 1) Mechanism hypothesis:
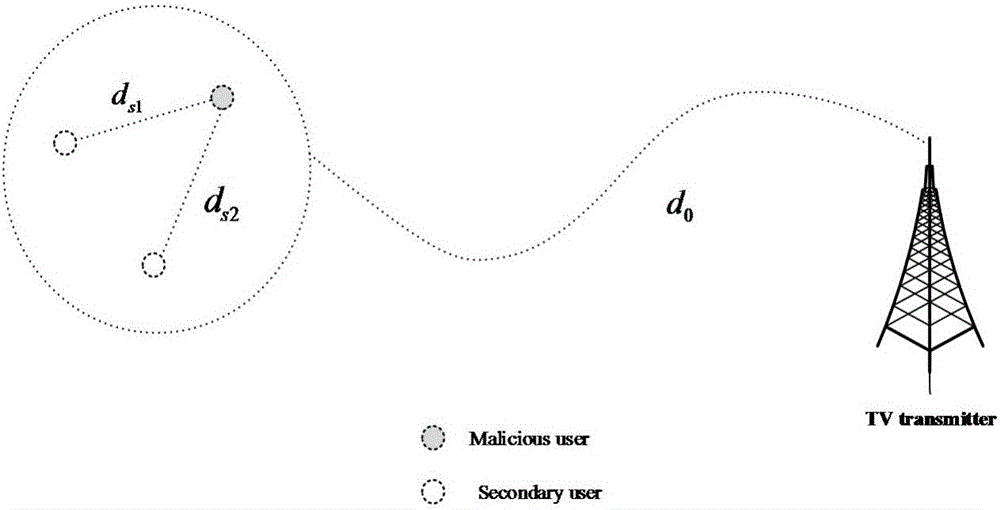
[0037] It assumes the relative distance between PU, MU and SU and the moving range of MU and SU, and at the same time stipulates the relevant parameters of the wireless channel, the transmission power of PU and MU, where, in the circular area with radius R, MU and SU1 , the relative distance between SU2 is Ds 1 , Ds 2 , the position of the TV signal transmitter is fixed, and the distance from the circular area with radius R is d 0 , and d 0 >>R. The power of the PU signal is P t , the preset power of MU is P m , SU receives the energy P of the signal from PU rp , SU perceives the shadow fading variable experienced by the signal of PU where a=ln10 / 10, β p Satisfy the normal distribution β p ~N(0,σ p 2 ), the shadow f...
Embodiment 2
[0053] like Figure 4 , 5 As shown in , 6 and 7, an attack scheme based on cognitive radio network imitating the primary user in a mobile scenario is disclosed. The attack strategy includes the following specific steps:
[0054] 1) Mechanism hypothesis:
[0055] It assumes the relative distance between PU, MU and SU and the moving range of MU and SU, and at the same time stipulates the relevant parameters of the wireless channel, the transmission power of PU and MU, where, in the circular area with radius R, MU and SU1 , the relative distance between SU2 is Ds 1 , Ds 2 , the position of the TV signal transmitter is fixed, and the distance from the circular area with radius R is d 0 , and d 0 >>R. The power of the PU signal is P t , the preset power of MU is P m , SU receives the energy P of the signal from PU rp , SU perceives the shadow fading variable experienced by the signal of PU where a=ln10 / 10, β p Satisfy the normal distribution β p ~N(0,σ p 2 ), the sha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com